Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Best No-Log VPNs – Are Companies Keeping Your Data?

We weren’t doing anything one day so decided to investigate the privacy reality in today’s leading VPNs.
Here’s what we found.
A VPN or virtual private network is advertised as the solution to online privacy concerns but how well does their behavior hold up under the scrutiny of our investigators?
When you sign up for a subscription to a VPN service, either a free or paid one, you must create an account with a username and password.
As part of that process, you will be required to accept the terms and conditions of the service, also known as the privacy policy.
Within this document, the VPN provider must explicitly detail what type of information they will track about their users and how long they will retain such records.
Many companies will claim in their marketing material that they have a no-logging policy. In reality, though, this is rarely the case.
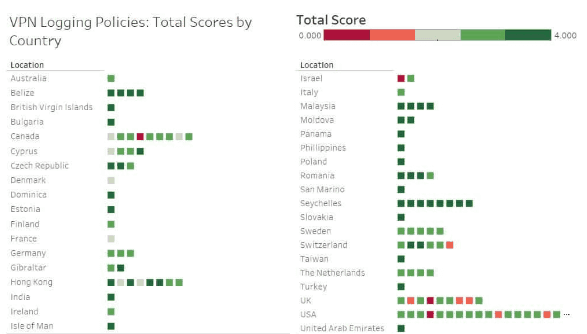
What really should matter to you is the type of logs that a VPN host tracks. Some types of logging are required for administrative and troubleshooting purposes, while others will veer into the territory of privacy invasion. Check our privacy tools breakdown.
Using a VPN is often seen as a workaround to avoid being monitored by an internet service provider (ISP), but you should understand a company’s full logging policy before investing in its VPN service.
For the purpose of this article, we will break the concept of logging into three separate areas:
- Error Logs. Logs that are captured about problems or issues with the VPN service. These logs may include some personal information, such as username or IP address, but are used exclusively for troubleshooting errors and improving the performance of the VPN.
- Connection Log. Some companies enforce restrictions on their service, such as how long a connection can last or how many simultaneous connections are allowed. By tracking connection logs, a company can keep track of each session on their service and manage them appropriately.
- Activity Logs. VPN servers are responsible for routing all of the traffic that comes through its network, so technically providers have the ability to monitor every web request that is sent or received. This means that a VPN host can track all web activity for each user and even determine what types of files are being downloaded.
Logs that are captured about problems or issues with the VPN service. These logs may include some personal information, such as username or IP address, but are used exclusively for troubleshooting errors and improving the performance of the VPN.
Logs that are captured about problems or issues with the VPN service. These logs may include some personal information, such as username or IP address, but are used exclusively for troubleshooting errors and improving the performance of the VPN.
Some companies enforce restrictions on their service, such as how long a connection can last or how many simultaneous connections are allowed. By tracking connection logs, a company can keep track of each session on their service and manage them appropriately.
VPN servers are responsible for routing all of the traffic that comes through its network, so technically providers have the ability to monitor every web request that is sent or received. This means that a VPN host can track all web activity for each user and even determine what types of files are being downloaded.
A VPN provider may set their logging levels for a variety of reasons. They may simply be interested in limiting their own broadband traffic in order to ensure top performance for all of their users. But of course, there is a chance that your web activity could be at risk of being sold to advertisers or other interested parties. Below you’ll find a helpful guide to many of the leading VPN solutions and how their logging policies stack up to one another.
Table of Contents:
- Best No-Log VPNs
- 1. NordVPN
- 2. IPVanish
- 3. StrongVPN
- 4. ExpressVPN
- 5. HideMyAss
- 6. CyberGhost
- 7. VyprVPN
- 8. Private Internet Access
- 9. TorGuard
- 10. Buffered
- 11. GooseVPN
- 12. Hotspot Shield
- 13. AstrillVPN
- 14. ZoogVPN
Best No-Log VPNs
1. NordVPN (Best No-Log VPN)
Key Features:
- Servers for NordVPN are hosted in Panama. This means there is a low chance your activity will be shared among national security agencies.
- The privacy policy for NordVPN states that the service has a complete no-logs policy.
- NordVPN will not track error, connection, or activity logs. Your personal data, including name, email address, and IP address, will all be kept anonymous.

2. IPVanish
Key Features:
- Servers for IPVanish are hosted in the United States. Because America has a data alliance with a number of other countries, including Canada, the UK, Australia, and New Zealand, there is a chance your VPN activity could be shared among national security agencies.
- The privacy policy for IPVanish states that the service takes a zero-logs approach.
- IPVanish will not track error, connection, or activity logs. Each user on the service is treated as an anonymous entity. IPVanish also supports the Electronic Frontier Foundation (EFF), which fights for protecting online privacy.

3. StrongVPN
Key Features:
- Servers for StrongVPN are hosted in the United States. The US has an internet security agreement with a number of other countries, including Canada, the UK, Australia, and New Zealand. This means there is a chance your data could be shared among national security agencies.
- The privacy policy for StrongVPN states that the service does not store any traffic logs. StrongVPN will not track error, connection, or activity logs. You can be confident that your online usage will not be stored at all on their servers.
- StrongVPN will not track error, connection, or activity logs. You can be confident that your online usage will not be stored at all on their servers

4. ExpressVPN
Key Features:
- Servers for ExpressVPN are hosted in the British Virgin Isles. As an independent entity, this means there is a low chance your activity will be shared among national security agencies.
- The privacy policy for ExpressVPN states that they do not monitor user activity or track bandwidth usage.
- ExpressVPN will not track activity logs. However, the service does store a limited amount of information for connection logs. This includes the date of each VPN session and what server was used. Your IP address is not included in this data.

5. HideMyAss
Key Features:
- Servers for HideMyAss are hosted in the United Kingdom. The UK has an internet security agreement with a number of other countries, including Canada, the United States, Australia, and New Zealand. This means there is a chance your data could be shared in relation to a national security incident.
- The privacy policy for HideMyAss explains that the service will not store any specific information about websites that you visit while using their VPN client.
- HideMyAss stores minimal activity logs, but they do track different types of connection logs, including your originating IP address, the duration of each VPN session, and the amount of bandwidth used.

6. CyberGhost
Key Features:
- Servers for CyberGhost are hosted in Romania. You do not have to worry about your personal data being shared among national security agencies.
- The privacy policy for CyberGhost states that the service does not store any statistical data.
- CyberGhost will not store any detailed activity logs. Their connection logs are kept anonymous and are only used to monitor server load and troubleshoot issues.

7. VyprVPN
Key Features:
- Servers for VyprVN are hosted in Switzerland. This means there is a low chance your activity will be shared among national security agencies.
- The privacy policy for VyprVN states that the service will not record any traffic data related to user activity or downloads.
- Although VyprVPN will not store activity logs, they do keep a log of connection data. This information will include source IP addresses, session timings, and the amount of data transferred.

8. Private Internet Access
Key Features:
- Servers for Private Internet Access are hosted in the United States. The US has a security alliance with a number of other countries, including Canada, the UK, Australia, and New Zealand. This means there is a chance your data could be shared among national security agencies.
- The privacy policy for Private Internet Access is somewhat vague, stating that no VPN traffic logs are captured on their service.
- Private Internet Access appears to have a true zero-log policy. This means they do not store error, connection, or activity logs, including any information that could identify one of their customers.

9. TorGuard
Key Features:
- Servers for Torguard are hosted in the United States. Because of the location of these servers and the agreements that the US has with other countries, VPN data could be seized in a case of national security.
- The privacy policy for TorGuard indicates that they abide by a true no-logs policy.
- TorGuard will not track error, connection, or activity logs. Any personal data linked to your VPN account is treated as fully anonymous.

10. Buffered – No Longer Active
Key Features:
- Servers for Buffered are hosted in Gibraltar. This means there is a low chance your activity will be shared among national security agencies from other countries.
- The privacy policy for Buffered states that customers will never have their browsing or download activity monitored.
- Buffered does not store activity logs, but they do capture some connection information, including incoming IP addresses, session times, and data size. These connection logs are only kept for a maximum of 30 days.
11. GooseVPN
Key Features:
- Servers for GooseVPN are hosted in the Netherlands. Because the Netherlands is part of certain international security alliances, there is some risk that your VPN information could be exposed in investigations relating to national security.
- The privacy policy for GooseVPN indicates that the service will never track activity logs with personal information.
- Although GooseVPN does not store activity logs, they do have logging practices around connection information, such as operating system and geographic location. IP addresses are not included in these logs.
12. Hotspot Shield
Key Features:
- Servers for Hotspot Shield are hosted in Switzerland. Laws in Switzerland do not allow for internet activity to be shared with other countries.
- The privacy policy for Hotspot Shield states that connection logs are tracked but then deleted at the end of each VPN session.
- Hotspot Shield has admitted that they do aggregate browsing activity in their logs. IP addresses are not included in the logs, but this means your online behavior is still being tracked.

13. AstrillVPN
Key Features:
- Servers for Astrill are hosted in Seychelles. The country has no international alliances related to internet data sharing.
- The privacy policy for Astrill admits that connection logs are kept on their servers.
- Although Astrill does not capture activity logs, their connection data does include IP addresses and general device information. This is used to monitor simultaneous connections from a single account.

14. ZoogVPN
Key Features:
- Servers for ZoogVPN are hosted in Isle of Man. This means there is a low chance your activity will be shared among national security agencies.
- The privacy policy for ZoogVPN claims that the company has a zero-log policy.
- ZoogVPN evidently does not store activity logs, but their servers do capture information on how much bandwidth is used per VPN session.

You May Also Like:



