Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Open Source Privacy Tools – Complete Guide to Online Safety in 2024
Almost everything you do online is being observed by someone. Private and state-sponsored organizations are monitoring and recording the websites you visit, how long you stay at those websites, what you say on social media, who you send emails to, the content of those emails, and more.
Find what steps you can take to protect yourself and your privacy here at Privacy Australia.
Why should I care about my privacy? I’m not saying anything that anyone should care about and I have nothing to hide.
For those who have nothing to hide, we have a special request. We know someone who would like you to send him all of your email addresses and their associated passwords. Not just the ones that you use at work. He would like all of your personal email addresses and passwords too. He will take a look through your email accounts, and if he finds anything that he feels others should know about, he will publish it online for you. So far we haven’t had anyone who wanted to fulfil this request.
Read Also:
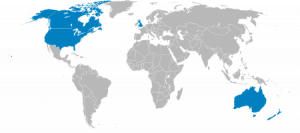
The Fourteen Eyes is the name of a group of countries that share intelligence with one another. This group consists of Australia, Canada, New Zealand, the United Kingdom, the United States, Denmark, France, the Netherlands, Norway, Belgium, Germany, Italy, Spain, and Sweden.
Within this group is a subset called the Five Eyes. The countries that make up the Five Eyes – Australia, Canada, New Zealand, the United Kingdom, and the United States, have made an agreement with one another called the UKUSA Agreement. Under the terms of this agreement, the nations that make up the Five Eyes have agreed to work together to collect, analyse, and share intelligence from different parts of the world. They have also agreed not to spy on each other as adversaries. Even though they have made this agreement, leaks from Edward Snowden revealed that some members of the Five Eyes do in fact spy on each other’s citizens.
They also avoid breaking domestic laws against gathering intelligence about their own citizens by gather intelligence about one another’s citizens and sharing it with each other. The Nine Eyes consists of the countries in the Five Eyes along with Denmark, France, the Netherlands and Norway. The member countries of the Five Eyes share intelligence with the members of the Nine Eyes and Fourteen Eyes. The members of the Five Eyes and third party member countries (those that are in the Nine Eyes and Fourteen Eyes, but not in the Five Eyes) spy on one another.
Five Eyes
- Australia
- Canada
- New Zealand
- United Kingdom
- United States of America
Nine Eyes
- Denmark
- France
- Netherlands
- Norway
Fourteen Eyes
- Belgium
- Germany
- Italy
- Spain
- Sweden
To protect your privacy, avoid services based in the United States
The surveillance programs in the US, along with the use of National Security Letters (NSLs) and associated gag orders, give the US government the freedom to secretly force companies to hand over access to their customer’s telecommunications and financial records. The government can use this access to spy on those customers. The gag orders that are associated with the NSLs prohibit the recipient of this type of request from talking about it. This is why you should avoid US based services.
This scenario took place with a company called Ladar Levison and their secure email service called Lavabit. After the FBI found out that Edward Snowden used this service, they requested that Ladar grant them access to Snowden’s records. Since Lavabit did not keep logs and since it encrypted its customer’s email content, Lavabit could not fulfill the FBI’s request. The FBI responded by serving a subpoena (with a gag order) for Lavabit’s SSL keys. With the SSL keys, the FBI would have access, not only to Snowden’s records but to all real-time communications (both metadata and unencrypted content) for all of Lavabit’s customers.
Levision wasn’t able to win this battle. They gave the SSL keys to the FBI and discontinued Lavabit. In response, the US government accused Levision of violating the subpoena and threatened to arrest Levision.
Levision restarted Lavabit and developed a new email standard called DIME – Dark Internet Mail Environment. DIME is a standard for end to end encrypted email. Lavabit currently offers DIME encrypted email services to consumers and businesses.
Related Information:
- Proof that warrant canaries work based on the surespot example.
- http://en.wikipedia.org/wiki/UKUSA_Agreement
- http://en.wikipedia.org/wiki/Lavabit#Suspension_and_gag_order
- https://en.wikipedia.org/wiki/Key_disclosure_law
VPN providers with extra layers of privacy
Visit our home page to see our full list of recommended VPN Services in Australia.
Our criteria for selecting VPN Providers for our table:
- The provider conducts business outside the member countries of the Five Eyes. For more information read To Protect Your Privacy, Avoid US-based Services
- The provider supports OpenVPN software.
- The provider supports alternate forms of payment including Bitcoin, cash, debit cards or cash cards.
- To open an account, the provider requires no information other than a username, password, and email.
Warrant Canary Examples:
- Discuss this chart on Reddit.
More information about VPNs
- Is Your VPN provider really keeping your data private?
(Note: the first providers listed are sponsors of this site). - How to strengthen the security of any VPN
- When choosing a VPN provider, watch out for VPN companies that pay for advertising and fake reviews.
- Ten Lies Exposed About VPNs
(Note: this is great article, but the site promotes itself in the piece). - VPN provider spies on its own customers to stop hacker.
- IVPN collects the email address and IP address of customers after they sign up.
Read their email statement in response. - blackVPN will no longer keep connection logs with timestamps when customers connect and disconnect from their services. They will now delete that information when a customer disconnects.
- Avoid the LT2P/IPSec Protocol. Select a different one instead.
The Warrant Canary Defined
A warrant canary is a notice that informs users of a service that the service provider has not been served with a warrant or secret subpoena. If the warrant canary is removed or if it ceases to be updated, users of the service should assume that the service provider has been served a warrant or secret subpoena, and the users should stop using the service.
Additional VPN Providers
- https://www.ivpn.net/resources
/canary.txt - https://www.bolehvpn.net/canar
y.txt - https://www.ipredator.se/stati
c/downloads/canary.txt
Additional VPN Providers
- Warrant Canary FAQs
- A list of companies that maintain warrant canaries.
- Bruce Schneier, an internationally renowned security technologist, criticizes warrant canaries in an article on his blog.
Recommended Browsers
Tor Browser

Tor Browser is a free and open source web browser that enables access to the Tor network. The Tor Browser and Tor Network help to keep you from being tracked by sending your data through a distributed network of servers.
Tor Browser runs on Windows, macOS, GNU/Linux, iOS, Android, and OpenBSD
Mozilla Firefox

Firefox is a free and open-source web browser. The Mozilla organization is very clear about what information they collect about you and their website shows you how to disable this collection if you want to do so. Be sure to follow our steps for adjusting the settings in Firefox at these links:
- WebRTC
- about:config
- privacy add-ons
Firefox is available for Windows, macOS, Linux, BSD, iOS, and Android
Brave

Brave is an open source browser that blocks ads and trackers by default. In addition to protecting the privacy of its users, Brave helps its users to save money by loading sites faster than its competitors. Brave was founded by the inventor of Javascript and co-founder of the Mozilla project, Brendan Eich.
Brave is available for Windows, macOS, Linux, Android, and iOS.
Make Sure Your Browser Is Not Leaving Fingerprints As You Browse The Web.
Unless you take steps to protect yourself, your browser will provide information about you as you browse online which makes it easy to identify you. This is also known as “fingerprinting.”
When you visit a website, your browser is telling a story about you to the owners of those websites. It is sharing information such as what browser you are using, what plug-ins your browser has installed, what time zone you are in, what type of device you are using at the time, and so on. If the set of data that the browser passes on about you is unique, then you can be tracked and identified even without cookies. [Panopticlick] is a tool that will show you how unique your browser configuration is.

Visit Panopticlick.eff.orgThere are two ways to prevent your browser from uniquely identifying you. The first way is to make your browser send the same type of information that most other browsers are sending so that you cannot be uniquely identified. To do this you should have the same fonts, plugins, and extensions as most people have on their browsers. If your browser allows it, you should use a spoofed user agent string to make your browser identify as something else. You should disable DNT and enable WebGL like the majority of web users. If you disable Javascript, or use Linux or TBB, your browser will identify you as unique and make it easy to identify you.
An easier way to keep your browser from uniquely identifying you is to use plugins like Privacy Badger, uBlock Origin, and Disconnect. These plugins will help you to keep your identity private.
Additional Information About Browser Fingerprinting
- Peter Eckersley, Chief Computer Scientist for the Electronic Frontier Foundation, discusses fingerprinting, how it threatens privacy, and what can be done to prevent it.
- Redditors discuss browser fingerprinting.
- Links to Firefox privacy add-ons.
- BrowserLeaks.com – A suite of web testing tools that can show you what type of information is available about you when you surf the internet.
Make Sure Your Browser Is Not Leaving Fingerprints As You Browse The Web.
WebRTC is a new communication protocol that relies on JavaScript that can leak your actual IP address from behind your VPN.
While software like NoScript prevents this, it’s probably a good idea to block this protocol directly as well, just to be safe
How to disable WebRTC in Firefox?
In short: Set “media.peerconnection.enabled” to “false” in “about:config”.
Explained:
- Enter “about:config” in the firefox address bar and press enter.
- Press the button “I’ll be careful, I promise!”
- Search for “media.peerconnection.enabled”
- Double click the entry, the column “Value” should now be “false”
- Done. Do the WebRTC leak test again.
If you want to make sure every single WebRTC related setting is really disabled change these settings:- media.peerconnection.turn.disa
ble = true - media.peerconnection.use_docum
ent_iceservers = false - media.peerconnection.video.ena
bled = false - media.peerconnection.identity.
timeout = 1
- media.peerconnection.turn.disa
Now you can be 100% sure WebRTC is disabled.
How to disable WebRTC in Google Chrome.
It is not possible to completely disable WebRTC in Chrome, but you can prevent leaks by changing Chrome’s routing settings. Two open source extensions to help you do this are WebRTC Leak Prevent and uBlock Origin. With WebRTC Leak Prevent you will need to check the options and adjust them as needed for your situation. With uBlock Origin, you need to go to “Settings” and select “Prevent WebRTC from leaking local IP addresses.”
How to disable WebRTC in Chrome on iOS, Internet Explorer, or Safari.[
Chrome on iOS, Internet Explorer, and Safari do not use the WebRTC protocol at this time. Our recommendation is that you use Firefox on all of your devices.
Firefox: Privacy Related “about:config” Tweaks
The following add-ons need to be configured properly before they will work with your browser.
Privacy Badger
Privacy Badger stops non-consensual tracking. If an advertiser or a third-party tracker is tracking your movements online without your permission, Privacy Badger will prevent them from serving content to your browser.
Privacy Badger has one limitation that you should be aware of. It does not block Google Analytics. To block Google Analytics you need to use a blocker like uBlock Origin. Privacy Badger works with Firefox, Opera, and Chrome.

uBlock Origin
uBlock Origin is more than an ad blocker. It is a wide-spectrum blocker. By default, it blocks ads, trackers, and malware sites. It can also block 3rd party scripts and frames depending on what settings you choose. uBlock Origin works with Chromium, Firefox, Microsoft Edge, and Safari.

Cookie AutoDelete
When you close a tab, Cookie Delete automatically deletes any cookies that are not in use. This add-on is available for Firefox and Chrome.

HTTPS Everywhere
HTTPS encrypts the communication between you and websites that support HTTPS. HTTPS Everywhere is available for Firefox, Firefox for Android, Chrome, and Opera.

Decentraleyes
Decentraleyes eliminates the need for your browser to load certain files from third-party services like Google Hosted Libraries and jQuery CDN.

This add-on comes with several commonly used files, and when your browser needs to access one of them, Decentraleyes will load it locally, which prevents your browser from making a call externally for the file, and at the same time protects your privacy. Decentraleyes is compatible with content blockers like uBlock Origin and Adblock Plus. It is available for Firefox. Source code available at GitHub.
We recommend that if you use Firefox that you use one or more of the following add-ons to protect your privacy.
uMatrix
uMatrix lets you determine exactly which sites your browser can connect to, what type of data your browser can download, and what functions your browser can perform. This add-on is recommended for advanced users.

NoScript Security Suite
With NoScript installed a website has to be whitelisted by you before it can execute any scripts in your browser.
You are in control and if you don’t give permission, NoScript will disable JavaScript, Java, Flash, and other plugins at websites where you have not specified that it is okay.

Recommended Firefox Add-ons For Protecting Your Privacy
This is a collection of privacy related about:config tweaks. We’ll show you how to enhance the privacy of your Firefox browser.
Getting started
- Enter “about:config” in the firefox address bar and press enter.
- Press the button “I’ll be careful, I promise!”
- Follow the instructions below…
Preparation:
- privacy.firstparty.isolate = true
- A result of the Tor Uplift effort, this preference isolates all browser identifier sources (e.g. cookies) to the first party domain, with the goal of preventing tracking across different domains.
- privacy.resistFingerprinting = true
- A result of the Tor Uplift effort, this preference makes Firefox more resistant to browser fingerprinting.
- privacy.trackingprotection.ena
bled = true - This is Mozilla’s new built in tracking protection. It uses Disconnect.me filter list, which is redundant if you are already using uBlock Origin 3rd party filters, therefore you should set it to false if you are using the add-on functionalities.
- browser.cache.offline.enable = false
- Disables offline cache.
- browser.safebrowsing.malware.e
nabled = false - Disable Google Safe Browsing malware checks. Security risk, but privacy improvement.
- browser.safebrowsing.phishing.
enabled = false - Disable Google Safe Browsing and phishing protection. Security risk, but privacy improvement.
- browser.send_pings = false
- The attribute would be useful for letting websites track visitors’ clicks.
- browser.sessionstore.max_tabs_
undo = 0 - Even with Firefox set to not remember history, your closed tabs are stored temporarily at Menu -> History -> Recently Closed Tabs.
- browser.urlbar.speculativeConn
ect.enabled = false - Disable preloading of autocomplete URLs. Firefox preloads URLs that autocomplete when a user types into the address bar, which is a concern if URLs are suggested that the user does not want to connect to. Source
- dom.battery.enabled = false
- Website owners can track the battery status of your device. Source
- dom.event.clipboardevents.enab
led = false - Disable that websites can get notifications if you copy, paste, or cut something from a web page, and it lets them know which part of the page had been selected.
- geo.enabled = false
- Disables geolocation.
- media.navigator.enabled = false
- Websites can track the microphone and camera status of your device.
- network.cookie.cookieBehavior = 1
- Disable cookies
- 0 = Accept all cookies by default
- 1 = Only accept from the originating site (block third party cookies)
- 2 = Block all cookies by default
- network.cookie.lifetimePolicy = 2
- cookies are deleted at the end of the session
- 0 = Accept cookies normally
- 1 = Prompt for each cookie
- 2 = Accept for current session only
- 3 = Accept for N days
- network.http.referer.trimmingP
olicy = 2 - Send only the scheme, host, and port in the Referer header
- 0 = Send the full URL in the Referer header
- 1 = Send the URL without its query string in the Referer header
- 2 = Send only the scheme, host, and port in the Referer header
- network.http.referer.XOriginPo
licy = 2 - Only send Referer header when the full hostnames match. (Note: if you notice significant breakage, you might try 1 combined with an XOriginTrimmingPolicy tweak below.) Source
- 0 = Send Referer in all cases
- 1 = Send Referer to same eTLD sites
- 2 = Send Referer only when the full hostnames match
- network.http.referer.XOriginTr
immingPolicy = 2 - When sending Referer across origins, only send scheme, host, and port in the Referer header of cross-origin requests. Source
- 0 = Send full url in Referer
- 1 = Send url without query string in Referer
- 2 = Only send scheme, host, and port in Referer
- webgl.disabled = true
- WebGL is a potential security risk. Source
Related Information:
- ffprofile.com – Helps you to create a Firefox profile with the defaults you like.
- mozillazine.org – Security and privacy-related preferences.
- user.js Firefox hardening stuff – This is a user.js configuration file for Mozilla Firefox that’s supposed to harden Firefox’s settings and make it more secure.
- Privacy Settings – A Firefox addon to alter built-in privacy settings easily with a toolbar panel.
Privacy-Conscious Email Providers – No Affiliates
All providers listed here are operating outside the US and support SMTP TLS. The table is sortable. Never trust any company with your privacy, always encrypt.
Another Email Service Provider You May Be Interested In
- Confidant Mail – Confidant Mail is a non-SMTP encrypted email system. It uses GNU Privacy guard to encrypt and authenticate communications, and TLS 1.2 to encrypt transport. Your private key stays with you, not the Confidant Mail server. This provides much more security for you than SMTP based email systems. Confidant Mail is available for Windows, macOS, and Linux. https://www.confidantmail.org/
Host Your Own Email Service

Mail-in-a-Box allows you to take total control of your email by enabling you to operate your own mail server. To set up Mail-in-a-Box you will need a cloud-based server with at least 1 GB of RAM running Ubuntu 14.04 and your own domain name. For more information visit https://mailinabox.email/
Additional Resources To Help You Keep Your Email Private
- gpg4usb.org – a free, open source, portable text editor that enables you to encrypt and decrypt text messages and files.
- Mailvelope – a browser extension for Chrome and Firefox that enables the user to encrypt email sent through services like Gmail, Yahoo mail, and Outlook. It encrypts messages using OpenPGP.
- Enigmail – an add-on for Thunderbird and SeaMonkey. It uses OpenPGP for encryption, decryption, digital signatures, and verification of email messages.
- TorBirdy – an extension that enables Thunderbird users to connect to the Tor network.
- Email Privacy Tester – This tool runs several tests to see if your email client is compromising your privacy.
Links to Articles about Email Privacy

- If your email messages are stored in the cloud, they may not be as private as you think. The Electronic Communications Privacy Act (ECPA), which at one time protected the privacy of email messages stored on servers, has not kept pace with technology. Email that has been stored on a server for longer than six months is considered abandoned and the government can search it. This article takes a look at how this affects the privacy of your data when it is stored in the cloud.
- [OpenMailBox link not pulling up]
- FBI seizes server of progressive ISP – An update to the FBI seizure of a server from May First/People Link and Riseup.
- Police investigation causes server to become compromised – the Italian Postal Police used an investigation into one mailbox to spy on all communications going through the Autistici/Inventati server.
Recommended Email Clients
Thunderbird
Thunderbird is a free, open source email client developed by the Mozilla Foundation. It supports real-time chat, web searching, and the Do Not Track option.
Thunderbird is available for Windows, macOS, and Linux operating systems.

Claws Mail
Claws Mail is a free email client based on GTK+. Users can use plugins for Claws Mail to read RSS and Atom newsfeeds, PDF attachments, and more. Claws Mail is included with Gpg4win, an encryption application for Windows users.
Claws Mail is available for Windows, macOS, Linux, BSD, Solaris, Unix and other operating systems.

Links to Articles about Email Privacy
- K-9 Mail – an open source email client for Android. It has many features including support for push IMAP, WebDAV, and multiple identities.
- GNU Privacy Guard – free, open source software based on OpenPGP. It enables users to encrypt and sign data and email communications. It is a command line tool that can be integrated with several different mail readers and graphical user interfaces to make it easier to use.
- MailPile – a free, open source application that works as an email client, a search engine, and a personal webmail server. It uses OpenPGP for email encryption and signatures.
Alternatives to Email
I2P-Bote

I2P-Bote is a plug-in for the I2P network. It keeps your email messages private by providing automatic encryption and digital signatures, and by storing your email in a distributed hash table instead of on a server.
I2P is available for Windows, macOS, Linux, Debian, and Android operating systems.
Bitmessage

Bitmessage is a decentralized, peer to peer communications system that simplifies the process of sending encrypted email messages by not requiring its users to use keys.
Bitmessage is free, open source, and is available for Windows, macOS, and Linux.
RetroShare

RetroShare is free, open source software that allows the user to create your own secure, anonymous, and decentralized network. You can use it to only connect to people you know and trust.
RetroShare can be used for forums, messaging and VoIP. RetroShare is available for Windows, macOS, and Linux.
Search Engines That Respect Your Privacy
To maximize your privacy when searching the internet you should select one of the search engines listed here.
Searx

Searx is a metasearch engine. When you type a query into its search box and hit return, the results will be a combination of results from several search engines. Searx protects your privacy by not collecting or storing information about you or your searches.
StartPage

StartPage provides search results from Google and protects your privacy at the same time. To protect your privacy they don’t record your IP address, they don’t collect personal information about you, and they don’t place identifying cookies on your browser. Each search result comes with a proxy option that allows you to visit websites anonymously.
DuckDuckGo

DuckDuckGo is a search engine that uses over four hundred sources to provide you with the best answers to your inquiries. When you search using DuckDuckGo, your personal information is not stored, and you are never tracked.
An Extension For Firefox That Protects Privacy
- Google search link fix – an open source addon that prevents Google and Yandex from changing the URLs of your search results when you click them. By disabling this behavior, this addon also prevents these search engines from tracking your clicks. Google search link fix is available for Firefox, Chrome, and Opera. (Open Source)
Other Search Engines With Privacy Features
- Qwant – Qwant is a search engine based in France. Qwant protects the privacy of its users by encrypting their search queries and by not tracking them or recording their searches.
- MetaGer – MetaGer is an open source search engine based in Germany. To protect the privacy of its users, MetaGer doesn’t save IP addresses, doesn’t track its users, encrypts data transmission, and offers a proxy server so that search results can be viewed anonymously.
- ixquick.eu – ixquick.eu is a metasearch engine that excludes results from Google and Yahoo. It is maintained by the same company that runs Startpage.com. It offers results by proxy and does not record information about you or place cookies in your browser.
Instant Messengers with Encryption
If you are using WhatsApp, Viber, LINE, Telegra, or Threema, or a similar instant messenger application, you should switch to an encrypted service, like the ones listed here, to protect your privacy.
Signal
Signal is a free, open source application that lets you send group, text, voice, video, document, and picture messages anywhere in the world. Messages and calls sent with Signal are encrypted from end to end. You can also set your messages to disappear at a time you choose.
Signal is available for Android, iOS, Windows, macOS, and Debian-based Linux.
Wire
Wire is a messaging app based out of Switzerland. You can use Wire for chat, phone calls, pictures, music, video, and images. Everything sent through Wire is encrypted end-to-end. One word of caution: Wire will keep a list of all people you contact until you delete your account. Wire is free for personal use.
Wire is available for Android, iOS, Windows, macOS, Linux and web browsers (Chrome, Firefox, Edge, and Opera).
Ricochet

Ricochet is a free, open source messaging service that operates over the Tor network. Every message sent through Ricochet is anonymized and encrypted end-to-end.
Ricochet is available for Windows, Mac, and Linux.
Other Instant Messaging Services With Privacy Features
ChatSecure

a free, open source messaging app for iOS. It offers end-to-end encryption through OMEMO and OTR over XMPP.
Kontalk

Kontalk is an open source messaging app that operates over a distributed network run by volunteers. It uses XMPP to encrypt client to server and server to server communications. Kontalk is available for Android, macOS, Linux, and Windows.
Additional information about Encrypted Instant Messengers
- Ricochet passes professional security audit and demonstrates that they are serious about security.
- How to communicate online without being watched or tracked.
- A link to download the Signal APK if you are an advanced user with special needs. Not recommended for regular users.
- Wire stores a list of all customer contacts until the customer account has been deleted.
- An audit demonstrates that the Telegram messaging app is not IND-CCA secure.
- A reddit discussion thread about Telegram and whether or not it is actually private as advertised.
Video and Voice Messengers with Encryption
If you are a Skype, Viber, or Google Hangouts user, you should switch to an encrypted service, like the ones listed here, to protect your privacy.
Signal

Signal is a free, open source application that lets you send group, text, voice, video, document and picture messages anywhere in the world. Messages sent with Signal are encrypted from end to end. You can also set your messages to disappear at a time you choose.
Signal is available for Android, iOS, Windows, macOS, and Debian-based Linux.
Wire
Wire is a messaging app based out of Switzerland. You can use Wire for chat, phone calls, pictures, music, video, and images. Everything sent through Wire is encrypted end-to-end. One word of caution: Wire will keep a list of all people you contact until you delete your account. Wire is free for personal use.
Wire is available for Android, iOS, Windows, macOS, Linux and the web.
Linphone

Linphone is an open source VoIP application that uses the SIP protocol for voice and video calls, instant messaging, and file sharing. Linphone offers end-to-end encryption through zRTP, TLS, and SRTP.
Linphone is available for Android, iOS, Windows10 mobile, macOS, Windows for the desktop, and Linux.
Other Video and Voice Messaging Services With Privacy Features
Jitsi

a set of free and open source applications made for secure online videoconferencing. Jitsi for the desktop offers chat, desktop sharing, file transfer and support for instant messaging.
Tox

a free, open source, distributed, peer-to-peer voice and video messaging application that offers end-to-end encryption. Tox is available for Windows, macOS, Linux, iOS, Android, and FreeBSD.
Jami

a free, distributed application for video, voice, and instant messaging that offers encryption. Ring is available for Linux, Windows, macOS, and Android.
Articles and Links with additional information about Encrypted Voice and Video Messengers
- A link to download the Signal APK if you are an advanced user with special needs. Not recommended for regular users.
- Wire stores a list of all customer contacts until the customer account has been deleted.
File Sharing Services with Privacy Features
OnionShare

OnionShare is a free, open source application for sharing files of any size. It enables its users to share files anonymously and securely through the Tor onion service. It generates a secret URL that has to be accessed for the recipient to download the file.
OnionShare is available for Windows, MacOS, and Linux.
Magic Wormhole

Magic Wormhole is a command line file sharing tool. It was designed to avoid the complexities of other encrypted file sharing systems. It protects the privacy of its users through a PAKE (password authenticated key exchange).
Cloud Storage Services with Privacy Features
If you are using Dropbox, Google Drive, Microsoft OneDrive, Apple iCloud, or a similar service to store your data in the cloud, you should switch to service that protects your privacy, like the ones listed here.
Seafile

Seafile is a file storage application that offers built-in file encryption and file syncing. Users can supply their own server or use the Seafile cloud service to store files. The Community Edition, which is for users providing their own servers, is free. The Pro Edition, which is for customers whose files are hosted by Seafile’s cloud service, is free for up to 3 users. Both the Community Edition and the Pro Edition provide two-factor authentication. The Pro Edition also offers remote wipe, an audit log, and antivirus integration.
The client software is available for Windows, macOS, Linux, iOS, and Android.
The server software is available for Linux, Raspberry Pi, and Windows.
NextCloud

NextCloud is a file storage application that allows its users to securely store their data at home, on a server of their choice, or with one of NextCloud’s service providers. NextCloud is free and open source.
NextCloud is available for Windows, macOS, Linux, Android, iOS and Windows Mobile.
Least Authority S4

Least Authority offers a cloud storage service called S4 (Simple Secure Storage Service) for individual customers. S4 provides client side encryption for stored files. Your data can be accessed either through Gridsync (a graphical user interface) or through a command line interface. The service costs $25 per month.
Gridsync is available for MacOS, Linux, and Windows.
Another Cloud Storage Service To Consider
- Muonium – Muonium is a free, open source cloud storage provider that offers anonymity and end-to-end encryption for your files.
Additional Information
- Cryptomator – a simple, free, open source file storage application that enables you to encrypt file content and names with AES. Available for Windows, macOS, Linux, Android, and iOS
- Top NBN Plans – Although slightly unrelated, this is a guide to the best NBN providers in Australia. I compared them by speed and privacy features as some ISPs are known to actively sell customer data.
Applications That Let You Host Your Own Cloud Server
If you are using Dropbox, Google Drive, Microsoft OneDrive, Apple iCloud, or a similar service and you would like to host a cloud server yourself, take a look at these options.
Seafile

Seafile is a file storage application that offers built-in file encryption and file syncing. Users can supply their own server or use the Seafile cloud service to store files. The Community Edition, which is for users providing their own servers, is free. The Pro Edition, which is for customers whose files are hosted by Seafile’s cloud service, is free for up to 3 users. Both the Community Edition and the Pro Edition provide two-factor authentication. The Pro Edition also offers remote wipe, an audit log, and antivirus integration.
The client software is available for Windows, MacOS, Linux, iOS and Android.
The server software is available for Linux, Raspberry Pi, and Windows.
Pydio

Pydio is an open source file sharing application for businesses. Files can be accessed through a web interface, through the desktop, or through a mobile device. It can be deployed on a server located at the business premises or in a private cloud. Pydio has different security settings that can be customized to match the privacy policy of the business that is using it.
Available for Windows, MacOS, Linux, Android, iOS, or through the web.
Tahoe-LAFS

LAFS stands for Least-Authority File Store. Tahoe-LAFS is a cloud storage system that is free and open source. It works by encrypting your communications and distributing them over several servers. LAFS is the system used by Least Authority S4.
Available for Windows, MacOS, and Linux.
Additional Information
- NextCloud – NextCloud is a file storage application that allows its users to securely store their data at home, on a server of their choice, or with one of NextCloud’s service providers. NextCloud is free and open source.
- Muonium – Muonium is a free, open source cloud storage provider that offers anonymity and end-to-end encryption for your files.
- Web Hosting Reviews – We looked at the top hosting companies and compared them based on speed and security.
File Syncing Applications with Privacy Features
Sparkle Share

Sparkle Share is a free and open source file syncing application. It offers both client side and server side encryption.
Available for Windows, MacOS, and Linux
Syncany

Syncany is an open source cloud storage and file sharing application that synchronizes your files to whatever type of storage you have. Your files are encrypted before you upload them. Syncany is not being actively maintained.
Available for MacOS, Windows and Linux
Syncthing

Syncthing is a free and open source decentralized file sharing application that enables you to store your data where you want. It protects your privacy by encrypting all of your communications with TLS. No central server is ever involved in transporting or syncing your data.
Available for Mac OS X, Windows, Linux, FreeBSD, Solaris and OpenBSD
Other Cloud Server Applications with Privacy Features
- git-annex – git-annex is a command line application that allows you to synchronize your files with git. If you are uncomfortable with using the command line, you can use git-annex assistant which comes bundled with git-annex.
Password Management Applications
f you are currently using 1Password, LastPass, Roboform or iCloud Keychain to manage your passwords, we recommend that you look for a more secure alternative below or check out our best password managers.
Master Password

Master Password is an open source free software application that works by algorithmically generating your passwords as you need them. Your privacy is protected with this solution because your generated passwords aren’t saved on your device, and they aren’t sent over the network.
Master Password is available for iOS, MacOS, Android, Windows, Linux, and the Web.
KeePass / KeePassX

KeePass is a free, open source password manager that is designed to be easy to use. With KeePass, your passwords are stored in an encrypted database that is secured with either a master key or a key file. The databases are encrypted with AES and Twofish. Visit these links for more information about [KeePassX] (not currently maintained) and [KeePassXC]
Available for Windows, MacOS, Linux, Android, and BSD
LessPass

LessPass is a free, open source application that was developed to make password management easier. LessPass works by computing passwords instead of generating and storing them. It never stores your passwords in a database and it doesn’t need to sync to your device to work. It uses PBKDF2 and sha-256.
Available for Windows, MacOS, Linux, Android, Firefox, and Chrome.
Other Password Management Applications
- Secure Password Generator – An online tool that generates strong and random passwords. All password generation is done in the browser.
- Strong Password Generator – a free, open source password generator that runs in your browser. It generators strong, secure passwords quickly and easily. Your passwords are never stored or transmitted.
- Password Safe – a free, open source password application that let you manage your existing passwords and generate new passwords according to your own rules. With Password Safe, you store your passwords in one or several encrypted databases. Designed with love by security expert Bruce Schneier, we strongly recommend using PW Safe if you want to support the open source privacy tools movement.
Additional Information About Password Generation
- John Oliver of Late Week Tonight and Edward Snowden discuss passwords (Youtube).
International Laws Regarding Key Disclosure
Links related to Key Disclosure Laws
Key disclosure laws determine the conditions under which an individual is compelled to give encryption keys to law enforcement officials. The laws differ in each country, but most countries require a warrant. Steganography and data encryption methods that ensure plausible deniability are two of the ways that individuals can use to defend themselves against key disclosure laws.
Steganography refers to hiding one message, image, or file inside of another message, image, or file. For the purposes of our context, the message being hidden is usually one that contains encrypted information. To ensure plausible deniability, the message that is hidden would have to be encrypted in such a way as to prevent an adversary from being able to prove that the hidden message exists.
Nations that have Key disclosure laws
- Antigua and Barbuda
- Australia
- Canada
- France
- India
- Norway
- South Africa
- United Kingdom
Nations where Key disclosure laws may or may not apply
- Belgium *
- Finland *
- New Zealand (unclear)
- Sweden (proposed)
- The Netherlands *
- United States (see related information)
Nations where Key disclosure laws do not apply
- Czech Republic
- Poland
Links to Additional File Encryption Services
- An in-depth look at Key disclosure laws from Wikipedia.
- Answers to a question about key disclosure laws at Law Stack Exchange.
- Maria Hoffman, Senior Staff Attorney for the Electronic Frontier Foundation, speaks about key disclosure laws and forced decryption at DEFCON 20.
File Encryption Applications
If you do not currently encrypt your hard drive, email records, or file archives, we recommend that you use one of these encryption applications.
Links to Additional File Encryption Services
- Cryptomator – a simple, free, open source file storage application that enables you to encrypt file content and names with AES.
- miniLock – an audited, peer-reviewed file encryption addon for Google Chrome and Chromium.
- AES Crypt – a file encryption application based on the Advanced Encryption Standard. It is simple to use and after installation it only requires clicking on a file and entering a password to use. Available for Windows, Mac, Linux and Android.
- DiskCryptor – an open source file encryption application that can be used to encrypt some or all disk partitions on a disk drive. Supports AES, Twofish, and Serpent. Runs on Windows.
VeraCrypt

VeraCrypt is a free, open source application based on TrueCrypt 7.1a. It can create a virtual encrypted disk, it can encrypt a partition or storage device, it operates in real time, and it is designed to provide plausible deniability.
Available for Windows, MacOS, and Linux.
GNU Privacy Guard

Free, open source software based on OpenPGP. It can be used as a command line tool or it can be used with front end applications. It encrypts and signs data and email communications.
Available for Windows, Vista, and Linux.
PeaZip

PeaZip is a free, open source utility for managing files and creating file archives. It supports over 180 different file formats. PeaZip includes several methods for securing your data including encryption using AES, Twofish, or Serpent, an encrypted password manager, two-factor authentication (optional, not required), and secure delete and file hashing tools.
Available for Windows, MacOS, Android, and Debian.
Networks Outside of the Surface Web
If you want to access content on the Dark web, browse the information in this section.
Tor Project

The Tor network enables its users to bypass the Surface web through its network of volunteer operated servers. Tor distributes your communications among several relay connections to protect your identity.
Available for Windows, Mac, Linux, iOS, Android, and OpenBSD
I2P Network

The I2P network is an overlay network that allows its users to communicate anonymously. All communication taking place with the network is encrypted end-to-end. I2P supports email, web browsing, website hosting, instant message, blogging, forums, and file storage.
Available for Windows, MacOS, Linux, Android
The Freenet Project

Freenet is a decentralized, distributed network. Files and communications are encrypted, and nodes are anonymized on Freenet. Users can share files, publish websites, and chat on forums.
Available for Windows, MacOS, and Linux
Links to Additional Networks Outside of the Surface Web
- ZeroNet – A peer to peer network using the BitTorrent network and Bitcoin cryptography.
- Retroshare – free, open source software that allows the user to create a secure, anonymous, and decentralized network to send encrypted communications.
- GNUnet – a suite of tools and applications for building decentralized applications that protect privacy.
- IPFS – a peer-to-peer file distribution system. The goal of IPFS is to replace HTTP and make the internet more efficient and cost effective. [Link to privacy warning].
Networks Outside of the Surface Web
If you are currently using Facebook, Twitter, or Google+, we recommend that you look for a more secure social media alternative here.
diaspora*

diaspora is a decentralized social network that is run off of servers (which they call “pods”) all over the world. To join diaspora you need to find a pod and register with it. In diaspora you can keep your identity private, and you choose who sees your information.
Friendica

Friendica is a decentralized social network that supports the diaspora protocol. Users can communicate with users at Friendica and also with users at diaspora and Hubzilla. Friendica also supports bidirectional communication with Twitter, App.net, GNU Social, and Mail.
GNU Social

GNU Social was developed as a social media application that lets its users control their own data and maintain their contacts. GNU Social was developed from Status Net.
A Link to an Additional Decentralized Social Network
- Mastodon – a free, open source, decentralized social network. It is based on GNU Social.
Additional Information about Social Networks
- Delete your Facebook account – Visit this link to delete your Facebook account permanently.
- A Guide to Deleting your Facebook account – Step-by-step instructions for getting rid of your Facebook account.
Domain Name Services for Greater Security
DNSCrypt

DNSCrypt is a free and open source domain name protocol that prevents domain name spoofing. DNSCrypt uses cryptography to make sure that communications coming from a specific DNS resolver are authentic and have not been modified or altered.
Available for Windows, MacOS, Linux, Android and iOS.
OpenNIC

OpenNic is a user owned alternative to domain name registries like ICANN. They offer several unique top level domains (including .bbs, .chan, .indy, and several others) not available through other registries. In addition, if you meet their requirements, you can propose and host your own TLD through their service.
Links to Additional Domain Name Services
- NoTrack – NoTrack is a DNS server that protects your privacy by overriding tracking requests from over 10,000 tracking domains. It can also be used to block ads. Available for Linux.
- NameCoin – NameCoin is a free and open source application based on bitcoin that powers the .bit TLD.
Secure Note Taking Applications
If you are currently using Evernote, Google Keep, or Microsoft OneNote, we recommend that you look for a more secure note taking application here.
Laverna

Laverna is a free, open source note taking application that offers a markdown editor, a distraction free mode, and the ability to encrypt your notes. You can use it with your Dropbox or RemoteStorage accounts.
Available for Linux, MacOS and Windows.
Turtl

Turtl is a free, open source application for taking notes, saving documents, bookmarking sites, keeping photos, and more. It uses cryptographic keys to protect your data. You can use the hosted Turtl or run your own Turtl server.
Available for Windows, MacOS, Linux, and Android.
Standard Notes

Standard Notes is a free, open source note taking application designed to be simple and private. It uses AES-256 to encrypt your notes and offers automatic syncing, web access, and offline access. Users who want extra features can subscribe to their Extended service which offers full access to their extensions and automated backups to cloud storage.
Available for MacOS, Windows, iOS, Linux, and Android
Link to an Additional Secure Note Taking Application
- Paperwork – a free, open source note taking application. To use it you need a server with Linux, Apache, MySQL and PHP.
Secure Note Taking Applications
PrivateBin

PrivateBin is an open source pastebin that provides security for your pastes by encrypting and decrypting them in the browser. The server has no access to pastes. Pastes can be password protected. To use it, you need to install it on your own server, or find a server running it that you can use and that you trust. For a list of servers running PrivateBin visit here.
0bin

0bin is a free, open source pastebin that encrypts pastes in the browser using Javascript. The creators of 0bin say that their goal is not to protect the users of 0bin. Their goal is to protect those who host 0bin from being sued for the content of the pastes. Their encryption methodology is set up to provide hosts with plausible deniability. You can use 0bin at 0bin.net, or download the code and set it up on your own server.
Links to Additional Secure Pastebins
- Disroot – Disroot offers a suite of secure services including a PrivateBin pastebin.
- Hastebin – Hastebin is an open source pastebin application. You can use it on the web, or download the code and run it on your own server.
Productivity Tools
Etherpad

Etherpad is a free, open source text editor. You can use it alone, or edit an Etherpad document in realtime with a group. You can install Etherpad on your own server, or use it through one of several publicly available instances.
Available for Windows, MacOS, and Linux
EtherCalc

EtherCalc is a free, open source spreadsheet application. You can use it alone, or collaboratively. You can use the version available at the website, or install it on your own server.
Available for Windows, MacOS, Linus, FreeBSD
ProtectedText

Protected Text is a free service that allows users to store encrypted notes. Protected Text encrypts text in the browser. They don’t track users and don’t serve ads. The service does not require registration to use. Users choose a name for their file and save it with a password when they are finished.
Links to Additional Productivity Tools
- Disroot – Disroot offers a suite of secure services including Etherpad and EtherCalc.
- Dudle – A free, online polling and scheduling application. It doesn’t require registration to use.
Security Enhanced Operating Systems
If you are currently using Microsoft Windows or Apple’s OSX, we recommend that you look for a more secure operating system here.
Qubes OS

Qubes OS is a free, open-source operating system designed as a secure alternative to other operating systems. The Qubes approach to security is “security by compartmentalization.” The various tasks that you perform on your computer are separated into “qubes” that are separated from each other. This way if one qube gets compromised by malware, it cannot compromise the other qubes.
Debian

Debian is a free, open source operating system created by members of the Debian Project. Debian systems use Linux or FreeBSD to run. Debian comes with over 51,000 free software applications. You can install Debian from a CD, you can download it online, or you can buy a computer with Debian preinstalled.
Trisquel

Trisquel is a free operating system based on Linux. There are several editions available depending on what your needs are. It was originally developed to provide an operating system that supported the Galician language.
Warning
If you want to preserve your privacy, avoid Windows 10 at all costs.
Links to Additional Operating Systems
- OpenBSD – a free operating system based in Canada that was designed to resemble UNIX. The goal of the developers is to be number one in security. Cryptography is embedded in several places in the OpenBSD OS. In addition, they have a security auditing team which has been auditing OpenBSD since 1996.
- Arch Linux – Arch Linux was designed to be the do-it-yourselfer’s version of Linux. The default installation contains only what is needed to operate the OS, and the user can modify it as needed. Parabola is a free, open source OS derived from Arch Linux.
- Whonix – Whonix is a free operating system based on Tor and Debian GNU/Linux. It was designed for security and privacy and accomplishes this by using the Tor network and an architecture that uses virtual machines.
- Subgraph OS – Subgraph was designed to be easy to use but difficult to attack. It comes with a kernel hardened with Grsecurity, it requires users to have encrypted filesystems, it restricts applications so that they only use the Tor network, and it comes with a secure instant messaging and a secure email client. Subgraph is based on Debian GNU/Linux.
OWASP’s 10 Most Critical IoT Vulnerabilities
- Weak, Guessable, or Hardcoded Passwords – Use of easily brute-forced, publicly available, or unchangeable credentials, including backdoors in firmware or client software that grants unauthorized access to deployed systems.
- Insecure Network Services – Unneeded or insecure network services running on the device itself, especially those exposed to the internet, that compromise the confidentiality, integrity/authenticity, or availability of information or allow unauthorized remote control…
- Insecure Ecosystem Interfaces – Insecure web, backend API, cloud, or mobile interfaces in the ecosystem outside of the device that allows compromise of the device or its related components. Common issues include a lack of authentication/authorization, lacking or weak encryption, and a lack of input and output filtering.
- Lack of Secure Update Mechanism – Lack of ability to securely update the device. This includes lack of firmware validation on device, lack of secure delivery (un-encrypted in transit), lack of anti-rollback mechanisms, and lack of notifications of security changes due to updates.
- Use of Insecure or Outdated Components – Use of deprecated or insecure software components/libraries that could allow the device to be compromised. This includes insecure customization of operating system platforms, and the use of third-party software or hardware components from a compromised supply chain.
- Insufficient Privacy Protection – User’s personal information stored on the device or in the ecosystem that is used insecurely, improperly, or without permission.
- Insecure Data Transfer and Storage – Lack of encryption or access control of sensitive data anywhere within the ecosystem, including at rest, in transit, or during processing.
- Lack of Device Management – Lack of security support on devices deployed in production, including asset management, update management, secure decommissioning, systems monitoring, and response capabilities.
- Insecure Default Settings – Devices or systems shipped with insecure default settings or lack the ability to make the system more secure by restricting operators from modifying configurations.
- Lack of Physical Hardening – Lack of physical hardening measures, allowing potential attackers to gain sensitive information that can help in a future remote attack or take local control of the device.
Privacy Enhanced Live Operating Systems
Tails

Tails is a free Debian GNU/Linux-based live operating system that can run off of a USB stick or a DVD. All software applications running on Tails that require internet access are forced to go through the Tor network to protect your privacy. Tails comes with cryptographic tools to encrypt your files and messages, and leaves no trace of itself on the computer where it is used.
KNOPPIX

KNOPPIX is a free, open source live operating system based on Debian GNU/Linux. It can run from a CD, USB stick, or DVD. The CD version contains Open Office, LXDE (for the desktop), Firefox, GIMP, and MPlayer, and utility applications. The DVD contains the same software as the CD and includes additional applications for office productivity, engineering, education, and gaming.
Puppy Linux

Puppy Linux is a free open-source operating system based on GNU/Linux. It is designed to be simple to use and fast to run. Like other live OS’s, Puppy Linux can be run from a USB drive, CD, or DVD. Because it is a small program (about 100 MB) it loads very quickly on most computer systems.
A Link to an Additional Live Operating System
- Tiny Core Linux – Tiny Core is a live operating system designed to be tiny. Tiny Core is based on Linux. It is 10 megabytes and does not ship with end user applications.
Privacy Enhanced Mobile Operating Systems
Using Google Apps with these operating systems may compromise your security. We recommend that you install MicroG on your device as an alternative.
LineageOS

LineageOS is a free and open source alternative operating system for smart phones, phablets, and tablets running Android. It was originally developed from CyanogenMod.
CopperheadOS

CopperheadOS is a mobile operating system designed for security and privacy. The free version of CopperheadOS supports Nexus 5L and 6P. The paid version of CopperheadOS supports Pixel and Pixel XL. Some of the security features included with CopperheadOS include full disk encryption at the filesystem layer and separate disk encryption keys for each user of a particular device.
Sailfish OS

Sailfish OS is a mobile operating system designed to be compatible with Android devices and chipsets. Sailfish is based on Linux with its core based on the Mer Project. Its user interface was developed with the QML language.
Links to Additional Mobile Operating Systems
- Replicant – a mobile operating system that is a modification of LineageOS and that had been designed with extra security and privacy features.
- OmniROM – a free mobile operating system designed to be an alternative to Android.
- MicroG – A collection of software programs designed to replace Google’s Android apps and libraries.
Open Source Router Applications
OpenWrt

OpenWrt is a free and open source GNU/Linux distribution designed for routers and other embedded devices. Its architecture allows you to add privacy features such as stateful packet inspection and intrusion detection for a low cost.
pfSense

pfSense is a free, open source software application based on FreeBSD. It is designed to be used as a firewall and router and can be managed through a web interface. You can use pfSense with hardware available from Netgate, or you can purchase your own hardware to use with pfSense.
LibreCMC (orig. LibreWRT)

LibreCMC is a collection of free GNU/Linux based embedded operating systems designed for routers and small single board computers.
Links to Other Open Source Router Applications
- OpenBSD – a free operating system based in Canada that was designed to resemble UNIX. OpenBSD runs on Ubiquiti Networks EdgeRouters.
- DD-WRT – free and open source firmware developed for several IEEE 802.11a/b/g/h/n wireless routers. DD-WRT does not require product activation and does not include tracking.
Open Source Router Applications
Many of the new features included with Windows 10 are being used to track you.
- Windows 10 includes data syncing by default. This includes:
- your browsing history, URLs you have typed, your favorites.
- our app settings
- Wifi hotspot names and your passwords for them.
- Windows 10 tags your device with a unique advertising ID. This setting is on by default.
- The unique ID is used to serve customized advertising to you.
- By default, Cortana, the virtual assistant that comes with Windows 10, is learning about you. It does this by collecting information about you such as:
- your search history
- your mic input
- your calendar entries
- your purchase history
- your credit card data
- your music preferences
- your keyboard stroke patterns
- According to Microsoft’s own privacy statement, the following types of data may be collected when you interact with a Microsoft product:
- your identity
- your passwords
- your demographics
- your interests
- your device and usage data
- your content
- your location
- your contacts and people you are connected to
- Microsoft can share your data with or without your consent.
- When you download Windows 10, you are giving Microsoft permission to share your data with any third party “with your consent or as necessary…”
Information and links to help you protect your privacy even if you use Windows 10.
- WindowsSpyBlocker – an open source application to stop Windows from tracking and spying on you.
- Windows 10 Privacy Tools – a link to an article at ghacks.net reviewing privacy tools for Windows 10.
- A guide for fixing the settings in Windows 10 so that you can maintain some privacy – from fix10.isleaked.com.
- A guide for adjusting the default settings in Windows 10 so that your privacy is respected – from arstechnica.com
- A guide for turning off data logging in Windows 10 – from reddit.
Links to articles that discuss how Windows 10 is violating your privacy.
- Adjusting the privacy settings does not stop Windows 10 from spying on you. – the Hacker News
- Windows 10 continues to violate the privacy of users that have disabled its data collection features. – Ars Technica.
- Microsoft’s terms of service give it permission to disable software and hardware that it has determined is unauthorized. – Techdirt
Quotes
“Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.”
“But just as the Internet has opened up the world for each and every one of us, it has also opened up each and every one of us to the world. And increasingly, the price we’re being asked to pay for all of this connectedness is our privacy. Today, what many of us would love to believe is that the Internet is a private place; it’s not. And with every click of the mouse and every touch of the screen, we are like Hansel and Gretel leaving breadcrumbs of our personal information everywhere we travel through the digital woods. We are leaving our birthdays, our places of residence, our interests and preferences, our relationships, our financial histories, and on and on it goes.”
“Privacy is one of the biggest problems in this new electronic age. At the heart of the Internet culture is a force that wants to find out everything about you. And once it has found out everything about you and two hundred million others, that’s a very valuable asset, and people will be tempted to trade and do commerce with that asset. This wasn’t the information that people were thinking of when they called this the information age.”
Links to Recommended Resources on Privacy
Guides
- Protect Yourself from Surveillance – a guide from the Electronic Frontier Foundation containing tutorials, overviews, and briefings on how to protect yourself from electronic spying.
- CryptoPaper – a documented collection of the thoughts, knowledge, and experiences on the subject of security, privacy, and anonymity from Crypto | Seb
- Email Encryption – a guide from the Free Software Foundation on how to encrypt your email.
- A Guide to Staying Private Online – an article by Douglas Crawford at BestVPN
- A Guide to Internet Privacy – a series of privacy guides from IVPN.
Information
- Security Now! – a weekly podcast covering personal computer security.
- TechSNAP – a weekly podcast covering systems, networking, and administration topics for people in the tech industry.
- Keybase.io – a free, open source security app for mobile and desktop devices. It is similar to Slack, but it provides end-to-end encryption.
- Freedom.press – Freedom of the Press Foundation is an organization that supports journalists and whistleblowers all over the world.
- Secure Australian Credit Cards – Although definitely not open source, my guide to the best Australian credit cards discussing the cards with the best history of financial security and protecting customer data.
- Erfahrungen.com – a site that reviews privacy related services. The site is in German.
- TOSDR.org – a service that rates and summarizes the Terms of Service for various sites on the web.
- ipleak.net – web based tools that show you your IP addresses, your DNS address, your location, your system information, and other bits of data that are being collected about you.
- Privacy Testing Tools – The folks at ghacks.net have put together a list of tools that you can use to test your privacy.
- Prism-Break.org – A directory of resources for protecting your privacy online.
- SecurityinaBox.org – a guide to online privacy for human rights advocates.
- AlternativeTo.net – a database of over 64,000 software applications listed as alternatives to mainstream applications. Users get to rate the applications and leave reviews.
- SecureDrop.org – an encrypted, open-source system that whistleblowers can use to submit information to the media anonymously. SecureDrop is a project of the Freedom of the Press Foundation.
- Privacy Pack – A collection of links to tools to help you maintain your privacy and security online.
[The website hosting Security First returns a 404 error] - Best Web Hosting – Best hosting has consistently been a security risk for small business websites. This guide walks new buyers through the choices available to them.
You May Also Like:







