Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Secure Email Options for Total Privacy

Even in the age of social media, email remains to be one of the main forms of digital communication across the globe.
Most individuals with internet access have multiple email accounts, with separate mailboxes for personal use and business use.
The amount of data passing between email boxes on a daily basis is truly staggering.
It shouldn’t be a surprise that hackers and cybercriminals focus a significant amount of their effort on trying to crack and infiltrate email systems.
In fact, many recent data breaches and security incidents have come about because of information within emails being intercepted.
As a general rule, internet users and organizations should avoid sending any confidential data over email, even if the message is being sent within a single domain.
Think about it in terms of snail mail. You would never write your social security number or credit card information in a paper letter because of the threat that someone could open the message in transit.
Fortunately, when it comes to digital communication, there are mechanisms available to ensure the security of data transfer. Secure, encrypted email is considered best practice among users who need to transmit confidential information.
This article will outline the basics of email security and offer reviews of some top encryption tools.
Normal Email Protocols – How It All Started
In the early days of the internet, email services were built on a system known as the Post Office Protocol (POP). The service got its name because of the model used to build it.
With a POP service, the email server will receive an incoming message and route it to the correct inbox without storing a copy of the message. The same is true in snail mail: the local post office delivers content to your mailbox and never makes a copy of it.

Quickly after the invention of POP email, users found a glaring concern with it.
If they accidentally deleted a message from their local email client, such as Microsoft Outlook, the message would be gone forever with no way of recovering it from the central email server that sent or delivered it.
The desire for better message retention led to a new invention: the Internet Message Access Protocol (IMAP). In order to support IMAP accounts, email servers needed to add capacity to store mailbox data online. Improved network speeds around the world made IMAP a possibility.
When you receive an incoming message on an IMAP account and open it from a desktop or web client, such as Gmail, you are actually viewing a copy of the email file.
The source object remains on the IMAP server, which means that if you log in to your email account from several different devices, your inbox will always look the same.
Both POP and IMAP are incoming mail protocols. The two of them rely on a separate service known as the Simple Mail Transfer Protocol (SMTP) for handling and delivering outgoing messages.
Transport Layer Security – What Does It Encrypt

At their core, the POP, IMAP, and SMTP protocols are managed over an unencrypted channel.
When you send or receive basic messages, content is sent in plain text.
This includes the subject and body of the email, as well as the headers that are used to direct the message to the correct destination.
Any sort of plain text transmission that hits the open internet is vulnerable to attack from outsiders. Since neither the data nor the channel is secured, hackers can intercept the message data and see what text has been sent.
As a protective measure, a system known as Transport Layer Security (TLS) was added to all of the popular email protocols. Nowadays, most email providers and clients have TLS enabled by default. TLS encrypts the channel in which data is sent through, but the data itself remain unencrypted.
TLS functions in the same manner as secure socket layer (SSL) technology for web browsers. When you see a padlock icon next to the URL in your browser address bar, that means the site has a valid SSL certificate installed.
Any web traffic you send to the secured site will be encrypted so that hackers have less of a chance to intercept and decode your data.
VPN’s – An Added Layer of Protection
If you regularly use public wi-fi hotspots when sending or checking your email, then it may be smart to consider investing in a reliable virtual private network (VPN) solution.
Using the best VPN around will protect your online data by adding an extra layer of security that shields you from intruders, an example of which, is NordVPN.
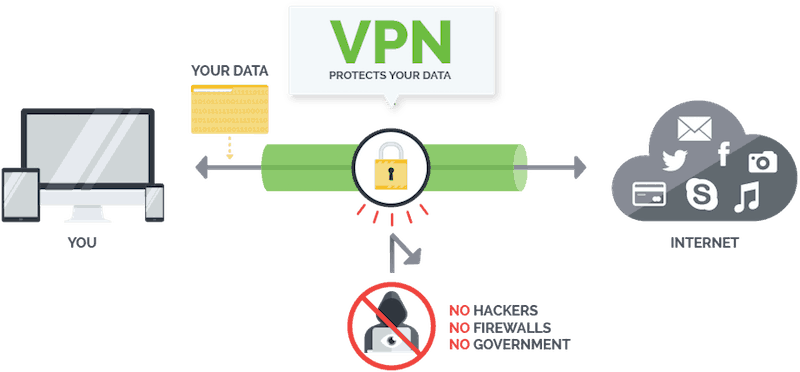
After you have established a VPN connection, your data becomes encrypted on the local network and passes through a secure tunnel before reaching the open internet.
This means that even if a hacker managed to take over a public wi-fi router, your information would still be coded so that they could not read the content.
As an added benefit, VPN tools offer you a certain level of anonymity. Normal internet connections can be traced by the IP address of your internet service provider (ISP).
With a VPN, you get assigned a new IP address that will mask your geographic location and make it harder to locate you.
See if your ISP can see your downloads.
End-to-End Encryption – The Benefits

With a typical POP or IMAP email account, even one that has TLS enabled and is used over a VPN connection, there is still a risk that your private information could be breached.
The web hosting company that maintains the backend email servers have full access to data you send or receive.
Even if you use one of our recommended web hosting services, the best hosting providers all keep a log of your messages, attachments, and files.
In order to fully protect your online communications, you’ll want to research secure email providers that offer end-to-end encryption. These types of systems rely on a public and private key system. Each user on the secure email platform will be assigned a public key and a private key.
The user’s public key is needed for encrypting outgoing messages, while the private key is used to decode received content and view it like a traditional message.
Because the private key is known only to the individual, even the email provider cannot access or read the data hidden behind it… effectively encrypting the data itself.
Today, most secure email platforms are web-based. You’ll log in to an interface, similar to Gmail or Yahoo mail, and compose a new message in a browser. When it comes time to send the email, you’ll be prompted to enter your private passcode or key to encrypt the outgoing transmission.
On the receiving end, users can access encrypted messages even if they do not already have an account with the secure email provider. Typically, you will need to give the recipient a one-time access code that they can use to log in to the system and retrieve the message.
5 Secure Email Options for Total Privacy
1. Zoho – Putting Security First
Secure emails are important, and truthfully, too many people rely on Gmail and Microsoft, both of which are good, but they don’t offer the most secure services.
Even more so, SMEs also tend to eschew the importance of secure emails, especially if they don’t have a mail server for their own usage.

This is where Zoho steps in: A comprehensive secure email that is great for both solo and co-operative requirements.
To start you off, you can sign up for free, for a modest storage of 25MBs which, while not a massive number, still more than enough for most of your needs. Thankfully though, Zoho has your back, and for just $1/month you can upgrade to their “lite mail” tier, which bumps that up to 5GBs
Not only that but once you start paying you also get some excellent collaborative features. For example, with the lite plan, you get folder sharing, streams, and email routing. They also have some good productivity tools such as notes, bookmarks, and tasks, which granted, is not as much as some other secure email providers, but it isn’t far off.
Of course, if you’re going for a business solution, you’ll want their business plan which starts at $3/month/user. With it comes a host of great business features such as an online word processor, spreadsheets and file manager, and you also get multiple domain hosting and even an intranet if you desire it.
You also get yourself 30GB of storage per user and 10GB of shared workspace storage per user.
Finally, in terms of security, it’s got all the bells and whistles you’d expect from a top-end secure email. Not only does it support 2FA, but it also supports OAuth 2.0, which allows third-party apps to access it. It also has POP and IMAP support, as well as TLS/SSL encrypted traffic.
Finally, it’s GDPR compliant which means that you can absolutely use it in the EU or if you have an office in the EU.
Overall, it’s a great service that is targeted to the business-minded who want good security, GDPR compliance, and want it at a good price.
2. ProtonMail – The Largest Secure Email Service Provider
ProtonMail is one of the leading end-to-end encryption email service providers. The organization was founded in 2013 in an effort to build a more secure internet.
Their data center is located in a secure facility in Switzerland, which means that information stored there is covered by the country’s strict data privacy laws.

ProtonMail offers a web interface as well as mobile applications for the Apple iOS and Android operating systems. Any message you compose within the ProtonMail interface will be automatically secured with your private key, so you don’t need to manually choose which messages to protect.
Keeping with their stance of offering top-level security, ProtonMail does not store any activity logs related to your account. Inboxes are kept completely anonymous and you don’t need to provide any personal information in order to create an account.
ProtonMail also prides itself on having an open-source codebase and offering a free basic account to all new customers.
The free option includes up to 500 megabytes of stored data and a maximum of 150 messages sent per day. A downside of the free version of ProtonMail is that all outgoing emails will have a default signature block that cannot be removed or changed.
For 4.00 euros a month, an individual can upgrade to 5 gigabytes of data and 1,000 messages per day. Enterprise options are also available for larger customers.
3. Mailfence – The Secure Email Service That Uses Digital Signatures
Mailfence is one of the most esteemed secure email providers on the market today. The company’s servers are based in Belgium, which offers good protection with data privacy laws.
However, if a local court issues an official order, Mailfence may be required to provide activity logs as part of an open investigation under a Belgium court.

Mailfence is a pure browser application and does not support mobile operating systems on their free plan. They do, however, offer a larger suite of tools than most competitors.
For example, Mailfence accounts include calendar tracker, contact management, and secure data storage to go along with their end-to-end email encryption.
Unlike with ProtonMail, the Mailfence application allows you to specify which outgoing messages are encrypted and which ones are sent normally. This way, you can use your Mailfence account as your primary inbox without forcing all recipients to decode your messages.
The free plan from Mailfence offers 500 megabytes of email storage and does not set a limit on the number of messages you can send.
For an added 2.50 euros per months, you will receive 5 gigabytes of storage and access to mobile applications. Mailfence also offers a 20 gigabyte option for 7.50 per month as well as various business plans.
In terms of downsides, Mailfence requires new customers to sign up with an existing email address, which means that your account cannot be completely anonymous. In addition, Mailfence’s codebase is not open-source like that of ProtonMail.
4. Hushmail – One of the Oldest Secure Email Services
Hushmail was first launched in 1998, making it one of the oldest secure email service providers with the intent of making email communication more secure worldwide.
Nowadays, it markets itself more to business customers although the service is also available for individuals looking for end-to-end encryption on personal emails.

Hushmail offers a full-featured browser client. There is an iOS app available for iPhone and iPad users, but Android owners will need to use a mobile website interface instead.
While composing a new message in Hushmail, you have the option of whether to secure the content or not. If you enable encryption, the recipient will be prompted to set up a personal passcode and view the content on a secure webpage.
Hushmail does not offer any free option for individual customers. Users can sign up for a 2-week trial but then have to pay $49.98 yearly for 10 gigabytes of email storage.
On the business side, Hushmail has custom designed solutions for companies in the healthcare, legal, or nonprofit industries.
Hushmail is based in the United States, and for that reason, some experts see it as a less secure option than tools like ProtonMail and Mailfence. There is a chance that government agencies could demand information from Hushmail servers. Your actual email content would remain encrypted, but data like IP addresses could be vulnerable.
5. Tutanota – The Mail Service that Encrypts the Entire Mailbox
Tutanota is an end-to-end encrypted email software and ranks as one of the best secure email providers on the market today.
The software was developed in Germany along with their entire team and servers being based in the secure EU country.
Being part of the EU means that Germany has one of the strictest data protection regulations in GDPR.

Along with that, Germany has other data protection laws that top the list in the world as far as protecting a citizen’s right to privacy. Not only that, the German constitution itself goes over the human right to privacy.
It is worth noting that Germany is part of the Fourteen Eyes group of countries. This may concern some people as the government does have the ability to meddle in the affairs of companies but Tutanota is clear about what the government can and can’t do with their service.
The service works as an ad-free web-based software. The software automatically encrypts your entire mailbox and address book. The webmail service does come as an iOS and Android app as well. The other thing to keep in mind is that the software is completely open source.
Different options are available with three different versions. The free option lets you have 1 GB of storage, only 1 user, Tutanota domains only, and limited search functionality.
The premium option, which comes in at €12 per year, includes more goodies. It enables you to add other users for €12 and gives you unlimited search, 5 aliases, inbox rules, and email support.
The Pro version is €60 per year and gives you the ability to pay for more users and contact forms while also giving you 15 more aliases, priority support, custom options, and 10 GB of storage.
Tutanota encrypts inboxes using AES 128-bit and RSA 2048-bit protocols which more than does the job. The interface Tutanota sports is probably our favorite but the biggest selling point of the service is that you can try it for free if you want.
When to Go Encrypted
So, how do you know whether you need to invest in a robust end-to-end email encryption tool? And what type of package or plan will meet you needs? That all depends on what line of work you are in and what types of email you send.
From a personal point of view, it can be valuable to have a basic subscription to a secure email system for the instances when you need to transmit social security numbers or financial records over the internet.
It will also offer reassurance to the recipient that the data is being sent over a secure channel.
Businesses that work with health, finance, or legal records should have a secure email platform available to their employees. While options discussed in this article offer compelling solutions that eliminate the need to develop internal tools. Ultimately, the perfect tool will entirely depend on you.
You May Also Like:



