Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
What Are DDoS Attacks and How to Stop Them

The media has a tendency to oversimplify and over-exaggerate certain digital threats.
DDoS attacks have, indeed, become a sort of catchall term for any kind of cyber-attack on a business or individual server or website.
As a result, lots of people aren’t really sure what a DDoS attack is and how they can best defend themselves against this potential issue.
Today, let’s break down exactly what DDoS attacks are and how you can stop them from affecting your website.
What Are DDoS Attacks?
DDoS stands for “distributed denial of service”. In short, a DDoS attack occurs whenever a cyber attacker floods a network with repetitive signals and traffic over and over.
The hacker normally uses bots (which replicate over and over) or hijacks multiple computers to create enough traffic to interrupt a service or network. Think of it as flooding a network with so much traffic that the server isn’t able to keep up, so it shuts down instead.
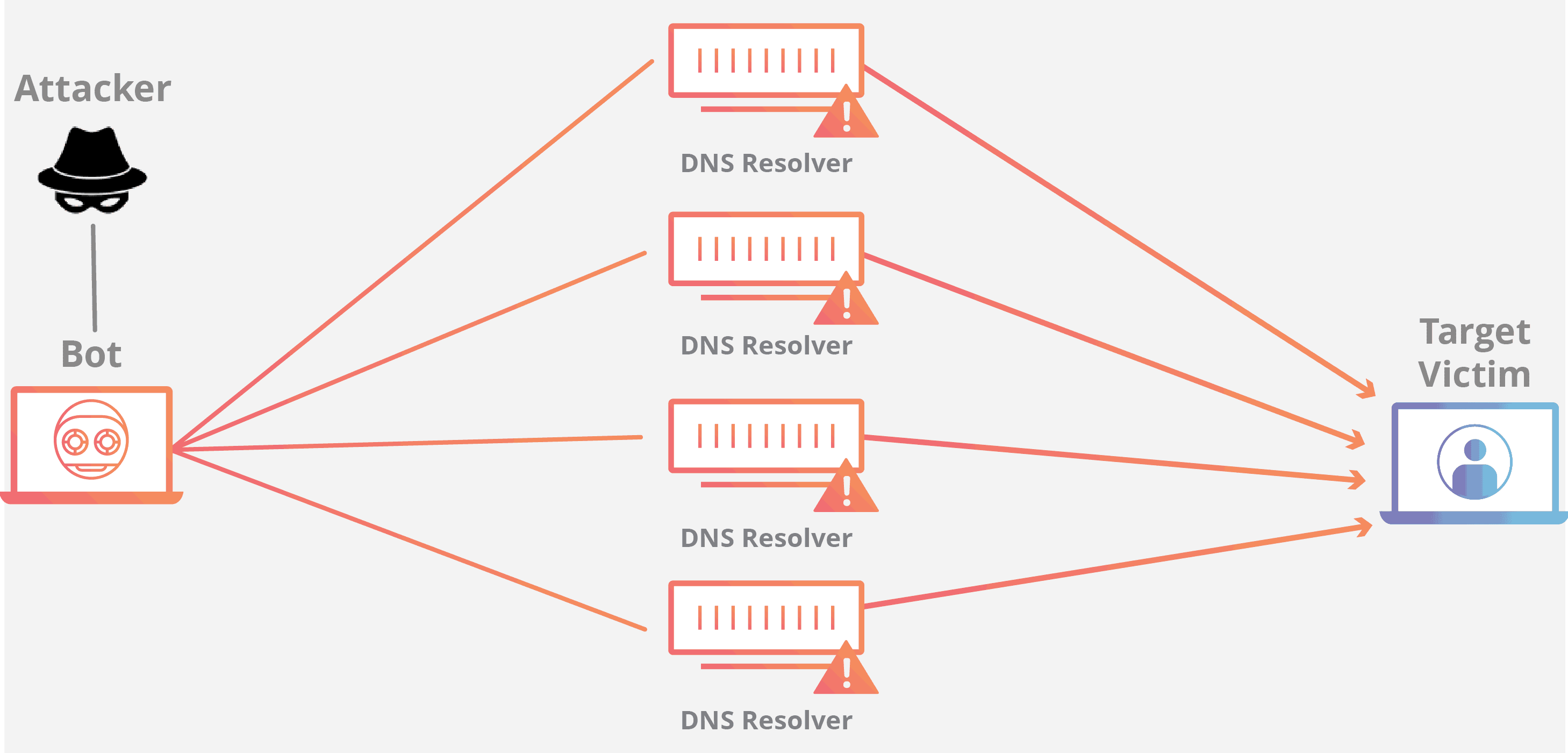
The purpose of these types of attacks is to send far more requests than the target server can handle, thus preventing the server from working with legitimate users. It’s often away for hackers to exact revenge against servers or organizations they don’t like or just for “trolling”.
However, when hackers target servers specifically linked to security or vulnerable data in a company or big organization, it can often have bigger ramifications. Some DDoS attacks can certainly leave a company’s network open for intrusion.
This makes figuring out how to prevent DDoS attacks or defend yourself against the critical if you have a small online business or any potentially vulnerable data on the web.
Why DDoS Attacks Are So Bad

There are a few reasons why these types of attacks are so attractive to hackers.
For one, they’re usually pretty affordable.
A would-be Internet criminal may not have the skill to pull off a DDoS attack themselves.
In that case, they can hire someone on the black market or dark web to execute an attack for them for only a couple hundred dollars.
Furthermore, for that small price, a DDoS attack can easily cause damage up to the thousands or millions of dollars. For larger sites that depend on consistent uptime, such traffic interruption can stop sales, prevent employees from communicating with clients, and much more.
Other DDoS attacks can ruin network security and leave a system vulnerable to intrusion and cyber theft. Even for smaller websites, these can be bad. If the website’s layout or data hasn’t been backed up, a DDoS attack can empty a site of content and media. This forces the owner to rebuild the site from scratch.
The ease by which DDoS can be done has led them to be one of the most common cyber-attacks carried out every single day. They’re a lot like the malware of the cyber-attack world; they’re more common than you might think, and knowing how to defend yourself is paramount.
What Are the Types of DDoS Attacks?
There are three main types of DDoS attacks that you might experience and need to be prepared to defend yourself against.
Volumetric Attacks
These attacks are the most common DDoS assault. In a nutshell, one or more bots eventually overwhelm the bandwidth of a network by sending tons of false requests to every open port in that network. The false reports eventually squeeze out legitimate reports and flood the open ports in such a way that everything shuts down.
UDP, or user datagram protocol, floods are volumetric attacks where the bot flood interferes with protocols that relate to the data transmission without checks. ICMP, or Internet control message protocol, floods occur when the protocol that network devices use to communicate with each other is interfered with or otherwise crashed by the sudden onset of too many false reports.
Either way, any networked machine has to deal with too many false data reports and requests and can no longer accept legitimate traffic.
Application Layer Attacks
These attacks occur on the topmost layer of an OSI network. In other words, they target the applications that users normally interact with and interfere directly with web traffic.
They can pick out and attack protocols for HTTP, HTTPS, DNS, or SMTP.
As a result, it’s a little more difficult to catch these types of DDoS attacks and processes since they often mimic real or legitimate web traffic.
Furthermore, these DDoS attacks use a smaller number of attacking computers. Sometimes, hackers can get away with it by using only a single machine. In these cases, after-action reports, where security experts try to discover what happened, may mistakenly interpret the attack as a crash because of a higher than average flood of “legitimate” user traffic.
Protocol Attacks
This last form of DDoS attack is targeted at network protocols that verify connections between machines or users. These attacks are so effective because they involve purposefully sending malformed or slow pings that require machines to use a lot of memory to verify or understand.
It essentially uses up too much memory or processing power for efficient traffic flow, eventually causing a crash.
Because of this, hackers will sometimes use these types of DDoS attacks to target firewalls. By sending huge amounts of irregular data that trips up their security flags, firewalls can be overwhelmed and eventually allow a probe or another attack through.
In particularly bad cases, hackers can use all three types of DDoS attacks at the same time.
These have a very high probability of overwhelming even the most robust network and security defense net.
Best Ways to Prevent DDoS Attacks
As with most other threats in our day-to-day lives, the best way to stop a DDoS attack from affecting you or your online business is to prevent it from happening at all.
Of course, this isn’t entirely up to you. It’s always possible that a hacker could target your business or accounts without any provocation.
But there are still some security measures you can take to minimize your risk. It’s like having a firewall or antivirus; even if you were to have the best antivirus ever created, it’s still smart to not purposefully visit suspicious sites or download files that you don’t trust.
Use a Web Application Firewall
First off, you should always use a web application firewall, which can protect your website and any real traffic that it receives. Some WAF providers or solutions will even offer automatic defense against DDoS attacks.
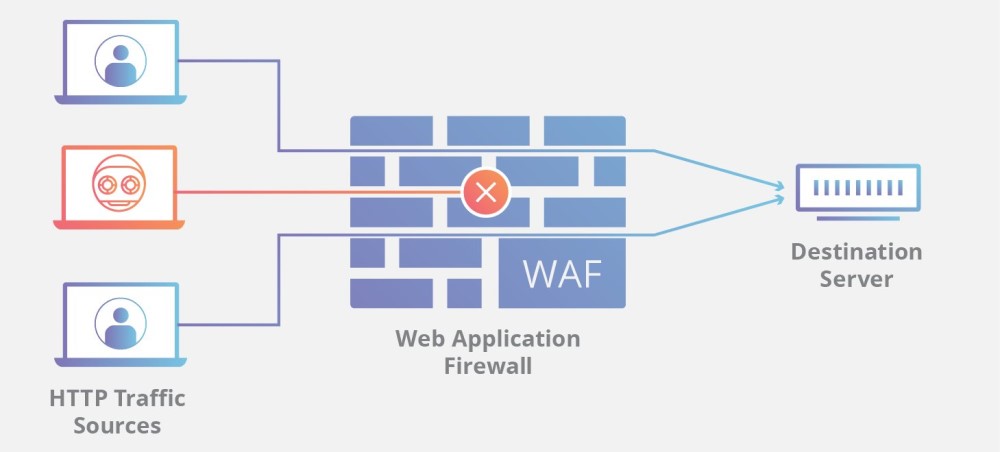
These firewalls need to be constantly updated so they’re always ready for new DDoS attack variations. Of course, even the best web application firewall won’t be able to defend against a full-on DDoS attack in many situations provided that the hacker has enough bots at his disposal. But it’s a good first line of defense anyway.
Use Active Country Blocking
As the name suggests, this will include blocking traffic to your website from specific countries. This is because website firewalls only see IP addresses and don’t focus on regional origin or other geographic markers.
This being said, country blocking is pretty easy for any skilled hacker to bypass, so this is more of a security measure to take to prevent your website from being particularly low hanging fruit.
You can use this strategy to block out websites or countries where your security team finds a higher than average number of recent DDoS attacks, for example. Be aware that this also limits legitimate traffic from that country, so you may need to weigh the risk of a DDoS attack against the legitimate traffic you might receive from that geographic source.
Always Monitor Your Website Traffic

It’s important, particularly if you’re running a large business network, to monitor your website traffic.
Certain peaks can give you clues as to whether a DDoS is currently being carried out or is one going to arrive in full force soon.
Virtually all DDoS attacks are detectable as huge upticks in traffic (although, as discussed, some attacks are better camouflaged than others).
Screening your website traffic in this way requires a bit of monitoring and your own common sense.
If you run a small online business and your last biggest peak was 1000 visitors, it’s pretty curious when you get a million visitors on a random Tuesday, right? You should additionally pay attention to the time at which traffic peaks occur. For instance, it’s a lot less likely that you’ll get a huge spike in even legitimate business traffic at 2 AM as opposed to regular business hours.
You can further analyze traffic for the country of origin. Does it make sense that your business got a ton of traffic from Russia when you have a small bakery website in Melbourne?
Overall, monitoring your website traffic is some of the best ways you can research your own network vulnerabilities and DDoS attack possibilities. Over time, as you get a sense of how your website or server traffic flows, you’ll be able to levy greater DDoS defenses against legitimate threats and stop some DDoS attacks before they become overwhelming.
Have Some Scalability In Place
It will likely be a good idea to have some scalability and scaling tools in place before a DDoS attack ever occurs. This might mean choosing a hosting provider that gives you the things you need to rapidly scale up your server resources at the flip of the switch.
Scalability translates to greater traffic capacity for your servers and/or website. This could be crucial if you want to withstand a DDoS attack or last long enough for other defensive measures.
You can also outsource some scaling to other companies or services.
We’ll detail those services below.
Best Methods of Stopping DDoS Attacks
In the event that a DDoS attack does occur, there are ways you can defend yourself.
Have a Response Team In Place

If you’re running things for a larger online business, it’s a no-brainer to have some kind of security response team in place in case a DDoS attack occurs for real.
If you have a response team ready to go, you might be able to preserve things or enact more active defenses in response to a DDoS assault.
Furthermore, a dedicated security team can ensure that all your cybersecurity defenses and protocols are up to date. Said defenses are the best way to prevent DDoS attacks by detecting them early.
Even if it’s just yourself, you should come up with an incident response plan or a few steps you can take so you aren’t spinning your wheels in the mud as the attack is carried out.
For instance, you can implement a systems checklist and see what’s already shut down and what you still have available use. You can also shut computers or servers down ahead of time to prevent hackers from potentially breaching your security.
One last benefit to assigning yourself or others as security chiefs for DDoS attacks means you might be able to detect these attacks early. This gives you a better chance of minimizing the damage they can wreak.
Have Security Systems Ready
It almost goes without saying that you should have a few different protection strategies already in place before your site goes live. This doesn’t mean just a simple firewall.
You should have intrusion prevention systems and threat management networks. These will combine regular firewalls, great VPNs, antispam tools, load-balancing tools, content filtering, and several other DDoS defense tools. All of these layers of defense together will do a much better job of protecting your network from a DDoS than just one of them alone.
You and any employees should already be practicing good Internet and network security.
Using complex and frequently updated passwords and quality password managers, ensuring that everyone in your network doesn’t visit suspicious websites, and other “digital hygiene” efforts are crucial for minimizing your network’s vulnerability to attacks like DDoS assaults.
It’s not an exaggeration to say that small efforts every day can go a long way toward securing your network from intrusions and shutdowns.
Call Your Hosting Provider or ISP

Of course, you can always call your ISP or hosting provider. By telling them you’re under a DDoS attack, they might be able to help.
For instance, they can drop packets that are destined for your web server before they actually arrive and cause serious damage.
Learn more about the best hosting providers.
They can also take other preventative or defensive measures to stop as much bot traffic from hitting your server and their other hosting servers over time.
Plus, your hosting provider or ISP might have additional security tools that you may not have for your personal website.
Even without their special security tools, it’s always a good idea to call your ISP in the event of a DDoS attack. In the worst-case scenario, they might be able to shut down your server in a way that doesn’t damage or scrub things. A controlled shutdown might be better than waiting for your server to be overwhelmed by traffic as intended by the hacker.
It’s also a good idea since you’ll be able to warn the ISP that traffic overflow from your server may affect other servers in the network.
Use Tools to Fight Against a DDoS Attack
There are specific anti-DDoS tools you can use in the event of an attack.
Let’s go over just a few of them.
Cloudflare

Cloudflare is one of the best tools for these purposes, as it’s scalable right off the bat.
This makes it a great choice for both smaller servers or websites or for larger networks that use multiple servers or handle traffic from thousands of people.
It combines several DDoS mitigation defenses into a single software solution. Without getting into too much detail, it can stop malicious traffic from getting to your network while still allowing legitimate traffic to come through. Furthermore, it’ll help your network remain functional for your legitimate users.
Even better, the company provides a reputation database so they can keep track of threats from repeated attackers. They do cost around $200 every month or even more if you want enterprise-level security.
Security Event Manager
The SolarWinds Security Event Manager, or SEM, is a tool that allows you to track network behavior and flag various DDoS threats before they become overwhelming. It’s a great way to shut down a DDoS attack before it becomes too hard to deal with. Note that this requires that you monitor your traffic constantly so you can catch a DDoS attack in the act before it becomes too serious.
For instance, it features several automated response tools that allow you to block suspicious IP addresses or even USB drives. Furthermore, it can disable any malicious devices or turn off various administrator privileges. This can potentially stop a DDoS attack from rampaging through your network if it starts from somewhere within your network (i.e. an inside job).
Furthermore, SEM has tools to help it monitor USB and file integrity. It’s essentially a one-stop-shop for general file observation and traffic monitoring. We like that you can try it out for 30 days for free before having to purchase the tool. Pricing is handled on a per-node basis.
Imperva

There’s also Imperva, which provides a DDoS tool that allows you to shield your network from attacks through high-capacity packet processing.
You can use their tool to protect you from DDoS attacks in perpetuity or on-demand if you think a new attack is about to crash against your servers. Furthermore, its dashboards are automatically updated to show any attack details while they are still in progress. This can help your security team find more solutions in the moment.
Basically, the tool processes high-traffic packets and scrubs them of bot traffic while still trying to let legitimate traffic through. This tool is only good for DDoS attacks, so you’ll need additional security measures for other digital threats.
Use a DDoS Mitigation Service
One other thing you can do to defend yourself against a DDoS is to call on a DDoS mitigation service or company. These are networking specialists that have the large-scale infrastructure you need to withstand a DDoS attack. In a nutshell, they allow you to transfer all of your suspected DDoS traffic to their servers where they won’t likely buckle under the sudden stress.
In many cases, using a DDoS mitigation company only takes a few minutes. Furthermore, some mitigation companies also perform traffic scrubbing services.
So they can reroute legitimate traffic to your site to keep things up and running and help your actual customers or users get what they need.
These services do require ongoing subscriptions, usually on the order of a few hundred dollars every month.
Is the Cloud the Way to Go?

One of the ways modern companies are tackling the threat of DDoS attacks is outsourcing their DDoS prevention efforts to companies like the mitigation services mentioned above.
But many of the best companies will also use the cloud to great effect.
The cloud doesn’t have as many bandwidth limitations as traditional server networks.
This also translates to greater server resource availability. Imagine being able to reroute outrageously high amounts of DDoS bot traffic to a cloud-based DDoS mitigation solution.
All that traffic could go to the cloud almost forever without straining any hardware server resources to any real degree.
Furthermore, companies that use cloud-based apps benefit from the cloud’s tendency to absorb malicious traffic before it reaches the intended destination. Ultimately, cloud-based DDoS solutions might very well be the way of the future because of the inherent advantages that this digital environment presents.
Summary
All in all, DDoS attacks can be harmful and worrisome, but there are plenty of ways to defend yourself against them. While it’s unlikely that these attacks will ever fully be eliminated from the digital sector, the good news is that new DDoS prevention and defensive strategies and tools are always being developed.
Take your pick from the above solutions or reach out to talk to us about other ways in which you can defend yourself against DDoS attacks. Good luck!





