Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Simple Guide to Hiding Your IP w/Pictures
Each time that you connect to the open internet, whether it’s from a computer, smartphone or tablet, your device uses an internet protocol (IP) address to send and receive requests. This IP address ensures that your outgoing and incoming data knows its source and its destination.

Depending on the setup of your network, your device might keep their IP addresses on a permanent basis. This is known as a dedicated IP address. Otherwise, your devices will retrieve a new IP address each time you restart or reconnect. This is done through a service known as Dynamic Host Configuration Protocol (DHCP).
In some cases, you may have the desire to hide or cloak your device’s true IP address. This is most often done to circumvent IP-based filtering on applications like streaming video or file sharing. In addition, IP addresses are based on geography, so hiding yours can help to disguise your location in the real world and help you avoid being tracked.
With a masked IP address, your internet service provider (ISP) will still handle all incoming and outgoing traffic, but to external servers, it will appear like you are using a different IP address. Read on to learn about the three primary methods for hiding your IP address.
Using a VPN to Hide Your IP Address
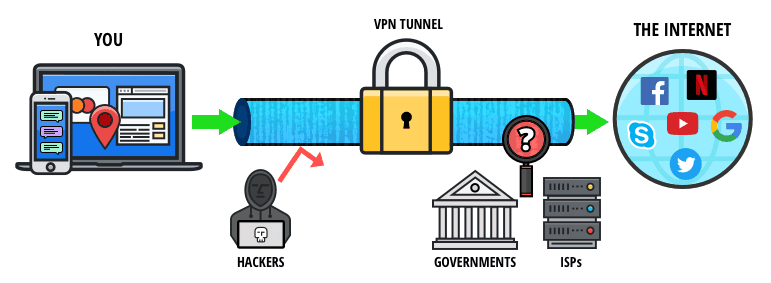
The most recommended way for altering your IP address is through a virtual private network (VPN). A VPN service operates like a tunnel between your computer or device and the hosting provider’s server. Your data is transferred through a secure, encrypted channel that your ISP cannot track or monitor.
To get started with VPNs, first you need to choose a service provider. You will find a range of free and paid options while searching the web. Try to avoid VPN services that claim to be free, as they are often poorly secured and very slow due to the amount of traffic they receive. Paid options will require a monthly or yearly subscription but will offer better and more consistent performance.
Once you’ve signed up for a VPN service, the provider will give you instructions on how to download the proper VPN client. This tool can be installed on your computer or mobile device and typically requires very little configuration. When you run the client for the first time, you’ll be prompted to enter your username and password.
Your device will initially contact the VPN host using the IP address that was assigned by your local network or ISP. But after that point, the VPN client will display the new IP address that your system is using. This address is what all outside websites and services will see. So if you are using a VPN host based in Australia, it will look as if your device is located there as well.
Using a Proxy Server
A proxy server functions like a VPN service except for one critical difference. They both utilize a remote server that can route your internet traffic and provide you with an anonymous IP address. However, a proxy server will not encrypt or secure your data like a VPN will.
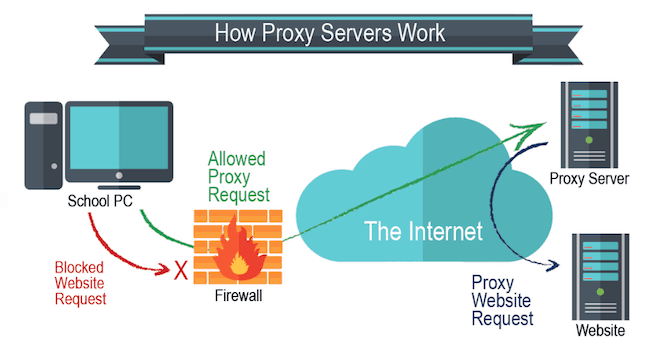
When connecting to a proxy server, all you need to know is the server’s address and port information. From there, you can go to the “Internet Options” tool on Windows or the “Network” preferences on a Mac to configure it. Note that you may need to reboot your computer in order for the proxy settings to take effect.
It’s also important to note that proxy server connections can only be used to hide your IP address for browser-based activities. If you are using external applications or other protocols that do not go through a browser, then your normal IP address from your ISP will be displayed.
Using a Cloaking Browser
If you don’t want to bother with the hassle of setting up a connection to a VPN server or a proxy server, there is a third option you can consider. The Tor web browser is an application for Windows and Mac OS X which is similar to Google Chrome or Mozilla Firefox, except it will randomize your IP address during every new session you open.
When you use the Tor browser, advertisers and other third parties will not be able to track your location or online activity. Be aware that this is much more secure than the “Incognito” feature on Chrome, which will simply open a new browser session with no cookies or cache.
You May Also Like:





