Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
What is Encryption? (Why it Matters for Aussies)
For as long as humans have had secrets, and that’s a long time, there has been a need to hide them from others. Welcome to the world of encryption.
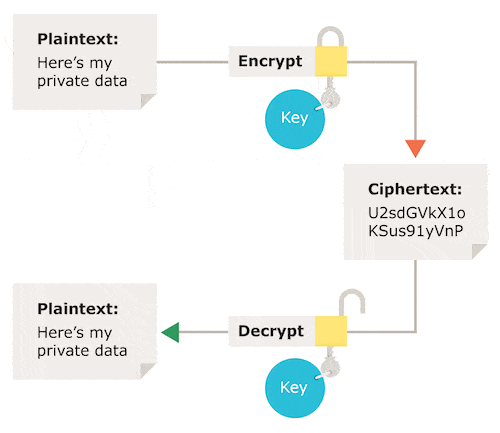
Encryption, in the world of computing, is a process where data is taken from something that is readable or easily understood and then encoded in a way that can only be decoded by another person or device if they possess the proper decryption key.
Encryption is what makes data secure.
Encryption takes digital information that a person can see or read, such as financial information, customer data, or photographs, scrambles it in such a way that a person looking at it is unable to make out what they are seeing. However, encryption is a process that can be reversed.
We can think of it like this, encryption is a lock. If you have the right decryption key, you are able to unlock, or read, the encrypted information. If you do not have the right decryption key, the only way to gain access is by breaking the lock.
This is where selecting the right type of encryption is important. If your encryption is the equivalent of a cheap padlock you get at the local hardware store, it can be easily broken.
However, the best encryption is comparable to the lock on a bank vault. It is virtually unbreakable.
Why Is Encryption so Important?

Privacy is essential to our personal lives. Data privacy is key to our security, reputation, and economic prosperity.
In the same way that you lock your home and that governments prevent access to critical infrastructure with the goal of protecting property in the physical world, encryption prevents cyber criminals from getting access to your data.
Governments around the world are introducing proposals to weaken the power of encryption, potentially putting your security at risk.
Encryption protects you when you shop, when you communicate, and when you bank. More and more of your life is carried out online. This is why you should be concerned about doing what you can to improve the security of your data and retain privacy.
Encryption is part of your everyday life online. You are probably not aware of it, but businesses and governmental agencies use encryption to secure your personal information.
It prevents identity thieves from robbing your information and logging in to your bank account. Encryption prevents hackers from reading your emails and personal communications.
Speaking on the subject of cyber security and encryption, former Secretary of Defense, Ash Carter, discussed the important role data security and strong encryption play in national security.
At the time, he urged entrepreneurs and innovators to play a role in making cyber security better. He was later quoted as saying, “Encryption is a necessary part of data security, and strong encryption is a good thing.”
How Does Encryption Work?
You start with unencrypted data. This data is frequently referred to as plaintext. This is another way of saying readable text that has not been encrypted.
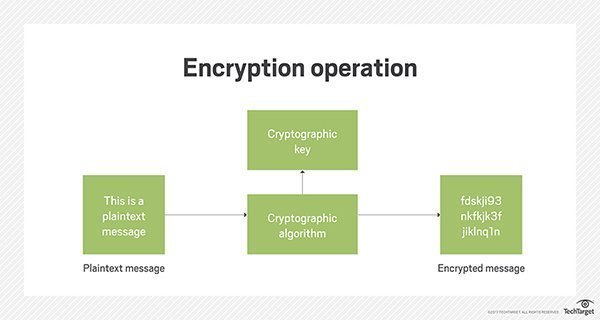
Next, that text is encrypted with the help of an algorithm, plus an encryption key. The end result is the generation of ciphertext. This text can only be understood if it is decrypted using the appropriate key.
Decryption is the reverse of encryption. Similar to how locking is the reverse of unlocking. When something is decrypted, the same steps are followed for encryption, only in the reverse order. The most popular forms of encryption algorithms break down to two categories:
- Symmetric
- Asymmetric
Symmetric Key Ciphers
A symmetric key cipher is often referred to as a “secret key.” It will use one key that it must share with any device looking to decrypt the encrypted data. The most popular symmetric key cipher is Advanced Encryption Standard. This key was first designed to protect government information.
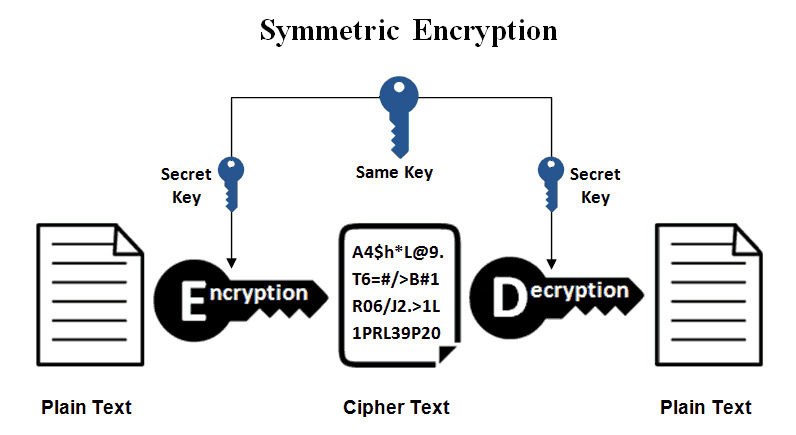
A symmetric key cipher can be compared to a person who only has one key for their house and locks the door when they leave. The only way someone can unlock the door, without breaking the lock, is if the homeowner gives them their key or an identical copy of their key.
Symmetric key encryption is a lot faster than asymmetric encryption. The sender has to exchange the key needed to decrypt the encrypted data to the recipient before the recipient can decipher the text. It is necessary to securely distribute and securely manage a number of keys.
For this reason, the majority of cryptographic processes utilize symmetric algorithms to encrypt the data, however, they use asymmetric algorithms to exchange the key.
Alberti Cipher – Where It All Started
The Alberti Cipher was one of the original polyalphabetic ciphers. First developed by Leon Battista Alberti, the Alberti Cipher was the first true example of advanced polyalphabetic substitution utilizing mixed alphabets and variable period.
The original device called “Formula” was comprised of two concentric disks that were attached via a central pin and rotated independently.
Asymmetric Cryptography
Asymmetric cryptography is often referred to as “public key” cryptography. In this process, two different keys are used. However, the keys are linked to each other mathematically. One is referred to as public and the other as private. The public key can be used by anyone. The private one is a secret.
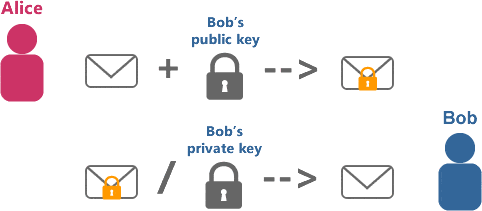
Think of it like the following scenario. Alice asked Bob to send her an open padlock via the mail. Bob keeps his own copy of his key. Alice receives the lock and uses it to secure a box that contains a message and then sends the locked box to Bob.
Bob can now use his key to unlock the box and read whatever information Alice has stored inside. If Bob wants to send a message back to Alice, he would need to ask Alice to send him an unlocked padlock and follow the process Alice followed when she sent him her message.
The most widely used form of asymmetric cryptography algorithm is RSA. This is because the private key or the public key can encrypt the information.
Feature That Keeps on Giving
The decrypting device needs to have the opposite key. This feature helps guarantee confidentiality, authenticity, integrity, as well as non-repeatability for electronic communications as well as data at rest. This is done via the use of digital signatures.
The biggest benefit that comes from using an asymmetrical key system is that no one needs to send their key to each other. This makes it impossible for someone to intercept the key and copy it while in transit.
If in the worst-case scenario Bob lost his key or had his key copied, the only information that would be compromised would be the information that Alice sent to Bob using his padlock.
However, the messages that Alice sent to other people would stay secret because they would be providing different locks for Alice to use when communicating with them.
Encrypting Data in Transit Versus Encrypting Data at Rest
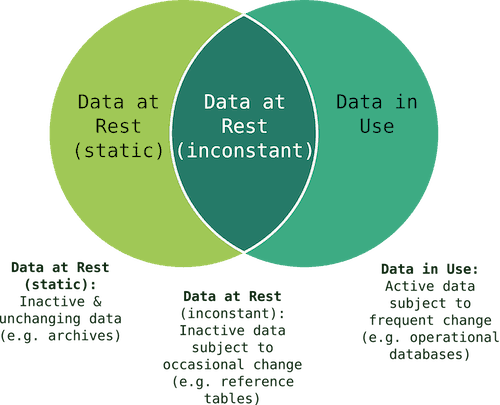
Data protection falls in to two basic types of encryption. There is data that is at rest, and there is data that is in transit.
If someone hacks your hard drive or your database, encryption makes that data impossible to read.
If your data is in transit, that is if you’re sending an email, communicating between browsers, or sending information to the cloud, and that data is intercepted, encryption makes it unreadable.
The following are some ways to achieve data encryption:
- Full Disc Encryption: This is the most common way to protect the at rest information on your computer’s hard drive. Files that are saved to your disc are encrypted automatically. Folder encryption and volume encryption are intermediate options that provide security without requiring full disc encryption.
- File Encryption: File encryption encrypts your at rest data on a file by file basis. This means that the files cannot be understood or read if they are intercepted. This is not an automatic process but is something that must be done for each file. What is a great about file encryption is that the data stays encrypted even once it leaves its place of origin.
- Encrypted Email Servers: Secured Multipurpose Internet Mail Extensions is a form of public key encryption that allows simple mail transfer protocol email servers the advantage of being able to receive and send encrypted messages as opposed to simply sending simple text messages.
- End-to-End Encryption: This hides the content of messages, only allowing senders and receivers to read it. With end-to-end encryption, any potential vulnerability in the communication chain, be it intercepting the messages while they’re being delivered or security weaknesses on the sender’s or receiver’s side, are tackled. Major platforms including Facebook and iMessage use end-to-end encryption.
- Pre-Encrypting Data Synced with the Cloud: Software of this sort pre-encrypts data before it arrives in the cloud. This means that anyone who hacks the cloud cannot read it. It is important to note that files that are stored on a local machine are not encrypted by the software and are still vulnerable.
Data Encryption Algorithms

- Advanced Encryption Standard is the most popular form of data encryption algorithm. Designed by the US government, it offers 128, 192, as well as 256 bit algorithm. 192 bit and 256 bit algorithms are used in circumstances that require extreme protection.
- IDEA – International Data Encryption Algorithm is an block cipher encryption algorithm that uses a 128 bit key. This cipher has a long track record of not being broken.
- RSA is an algorithm that uses paired keys. This is standard for sending information via the Internet. In the past, there were some challenges with the algorithm getting broken. However, these challenges have since been resolved.
- Blowfish and Twofish are block ciphers. They are commonly used on e-commerce platforms. Their most common use is protecting payment information. Both systems offer symmetric encryption. The keys vary in bit length. Twofish is the newer of the two programs. It has longer encryption keys.
How Hackers Challenge Encryption
A hacker’s main purpose in avoiding encryption is to get at your private and sensitive information. They know that your private and sensitive information is valuable and can be sold to others who will exploit that information for their well-being and your detriment.
The most basic method hackers will use to attack encryption today is to use brute force. A brute force attack is one where random keys are used until the right key is found. This underscores the importance of having a strong key. The longer the key, the lower the possibility is that a hacker is going to be successful in their attack.
As the key size increases, the number of resources a hacker will need to have to perform their computation also increase.
Another method of breaking ciphers is side channel attacks. Electrical circuits by nature leak.
They create emissions as byproducts, making it easier for an attacker who does not have access to circuitry to understand how the circuit is working and based on that deduce the data that is being processed. The two sources of valuable information a hacker will use are heat and electromagnetism.
However, as Kevin Mitnick, an American computer security consultant, author, and hacker stated:
Companies spend millions of dollars on firewalls, encryption, and secure access devices, and it’s money wasted because none of these measures address the weakest link in the security chain- the people who administer, operate, and account for computer systems that contain protected information.
Companies spend millions of dollars on firewalls, encryption, and secure access devices, and it’s money wasted because none of these measures address the weakest link in the security chain- the people who administer, operate, and account for computer systems that contain protected information.
The point is that you are responsible for the security of your information. If you do not take the time to learn about the encryption options that are available for your information or learn about the benefits of using the best VPN for your circumstances, you are putting your privacy, your social future, and your financial future at risk.
The History of Encryption
Privacy has been a concern for mankind since the beginning. Different societies around the world developed unique ways of preventing their personal information from falling into the wrong hands.
Scytale

The history of encryption begins around the year 700 BC.
The Spartan military used scytale to send sensitive information during times of battle.
The sender and the recipient each had a wooden rod that was the same length and the same diameter. To encrypt the message, the sender would take a piece of leather and tightly wrap it around their wooden rod.
They would write a message on the rod, unwind it, and send it to the recipient. The recipient could only decipher the message after wrapping the piece of leather around his scytale.
Alberti Cipher

In 1467, Leon Batista Alberti invented the poly alphabetic substitution cipher. This cipher revolutionized encryption.
The cipher had two metal disks that spun on the same axis. It contained a mixture of alphabets and variable rotations.
The Jefferson Wheel

First introduced in 1797 and consisting of 26 cylindrical wooden pieces with an iron spindle, the Jefferson wheel had the letters of the alphabet inscribed on the edges of each wheel in random order.
Turning the wheels would scramble and unscramble words. When a person received the Jefferson wheel, they would spell out the coded message on the wheel.
They would then look for a different line of letters that made sense. This form of encryption was used once again by the U.S. Army between 1923 and 1942.
The Enigma Machine

Making its debut in 1943, the Enigma machine was a series of electromechanical rotor ciphers used by the Nazi military. At the time, it was considered unbreakable.
The Nazis would change their cipher daily.
Until Alan Turing and his team were able to capitalize on the weakness of the machine, the Enigma gave the Nazis an unprecedented advantage.
ASE and Captcha
The year 1997 led to the invention of two revolutions in encryption and security. The National Institute of Standards and Technologies developed Advanced Encryption Standard.
As discussed earlier in this guide, this 128 bit encryption is still used today.
A device that would be able to check a billion billion AES keys every second would require 174,449,211,009,120,166,087,753,728 years to crack this encryption.
The year 1997 was also the year that Captcha was first introduced. A randomly generated image of text that can only be read by humans appeared on the screen.
The waviness and unique features of the text makes it impossible for electronic devices to read. In order to gain access to a site, a human user needs to input the series of letters or numbers that is displayed in front of them.
The year 1997 was also the year that Captcha was first introduced. A randomly generated image of text that can only be read by humans appeared on the screen.
The waviness and unique features of the text makes it impossible for electronic devices to read. In order to gain access to a site, a human user needs to input the series of letters or numbers that is displayed in front of them.
It is clear to see that cryptography and its methods have been developing for hundreds of years. Today, AES has proved to be one of the most advanced and secure forms of encryption the world has ever seen.
The military and government have long been at the forefront of encryption research with the goal of protecting military secrets. It is not surprising that research in the field of encryption is ongoing.
How Do VPNs Encrypt Your Information?
A VPN secures the traffic between the device you’re using and the VPN server. This makes it difficult, if not impossible, for spies and hackers to see your data while it’s being transmitted. A VPN is a private network.
A VPN uses tunneling. This is a process that allows your data to be sent privately and securely over the Internet.
To understand how tunneling works, you need to remember that all of the information that is transmitted over the Internet is broken into small pieces called packets. Each packet has important information.
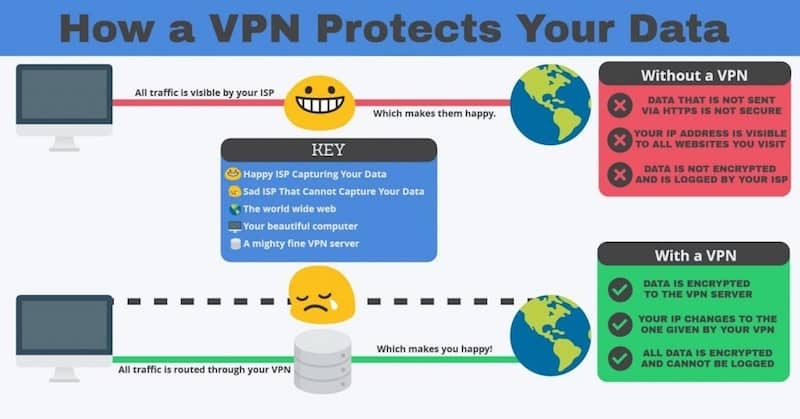
With a VPN tunnel connection, every data packet you send is put inside of another data packet before it is transmitted over the Internet. This is a process known as encapsulation. The outer packet provides a level of security, preventing its contents from being viewed by the public.
Tunneling is just one facet of the protection you get from a VPN. A VPN encrypts the data that you are sending over the Internet so that the packets can only be accessed by your VPN’s client and server. The VPN’s client and server are connected together.
There are many VPN security protocols that are used to keep your data encrypted. One of the most common is IPSec, also known as Internet Protocol Security. Another one is OpenVPN.
These protect your data by first taking each encapsulated data packet and encrypting its contents using an encryption key. The encryption key can only work between the VPN’s server and client.
Second, a sub protocol is used, known as the encapsulation header. This encapsulation header is going to hide some of the packet information. Part of what is hidden is your identity.
These two key features, tunneling and encryption, are just part of what makes your data more secure with a VPN. Authenticated connections are another tool designed to keep prying eyes away from your private and personal information.
The Benefits of Encryption
The primary benefit or purpose of encryption is to protect confidentiality and privacy of data that is either stored on a computer or transmitted via the Internet or an internal computer network. Encryption prevents unauthorized individuals from accessing and exploiting your private data.
For example, credit card companies require merchants to encrypt their customer’s data both when the information is being stored and when it is being sent over networks.
Individual consumers have a responsibility to take steps to protect their personal privacy. In 2017, more than 190 million smartphone users were hacked.
In 2016, Apple showed willingness to cooperate with the federal government and violate their users privacy policy. This is important for you to think about.
Your personal information, including Social Security numbers, private instant message conversations, banking information, and sensitive photographs, are at risk of being used by nefarious individuals, whether they are criminals or governmental agencies.
Why Does Encryption Matter?
The United States, along with 13 other countries, is part of what is referred to as The 14 Eyes. These countries are cooperating with each other in gathering intelligence.
While this might seem relatively benign, the truth is that these governments are using programs that allow them to intercept the information that is communicated online and via text, the things that you download, as well as your banking information. What you think is private can quickly become public.
You deserve to be able to send and transmit information securely and privately. Many mistakenly believe that online security and encryption should not worry them because they do not have anything to hide.
The truth is that information that may seem irrelevant and unimportant to you, when it falls into the wrong hands, can be used to damage your reputation, hurt you financially, and expose private aspects of your life to the world.
Protect yourself by learning more about encryption and then taking advantage of encryption software designed to keep you and those you care about safe.
You May Also Like:





