Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Emotet Returns in Time for Christmas

Back in January 2021, Emotet dramatically took the ‘L’ when it was blocked by security enforcers. But their victory was short-lived… Now, security researchers say Emotet is returning.
Table of Contents:
Why it’s so Dangerous
Let’s begin with the story according to Europol – Emotet was so dangerous as it was professionally ‘service-for-hire.’
Tailored by need. Sold to different types of threat actors… Taking so many possible forms, Emotet could be turned into ransomware, for instance. Or a banking Trojan; any of which could then be installed onto a victim’s device, as a Trojan.
Since 2014, the malware developed into any cyber-attacker’s ad hoc crowbar – with email spamming being its bread and butter entryway. The infrastructure is, indeed, streamlined for initial door opening of enterprise-grade networks. Europol dubbed it ‘world’s most dangerous malware.’
Of course, it grew exponentially through its use in large spam campaigns. How so? Via self-perpetuating malicious attachments: these circulated the malware, infiltrating devices then launched new spam campaigns by installing more payloaders like QakBot (Qbot), ie. ‘loader’ operation attacks.
One evasion technology that Emotet uses is multiply-generating download links for primary loaders. Making it extra slippery.
If even one path isn’t blocked or isolated, by a security product, the loader will successfully download. Gaining this reputation for jacking open machines, Emotet naturally became used to develop other devastatingly effective, global malware – infamous names such as Ryuk.
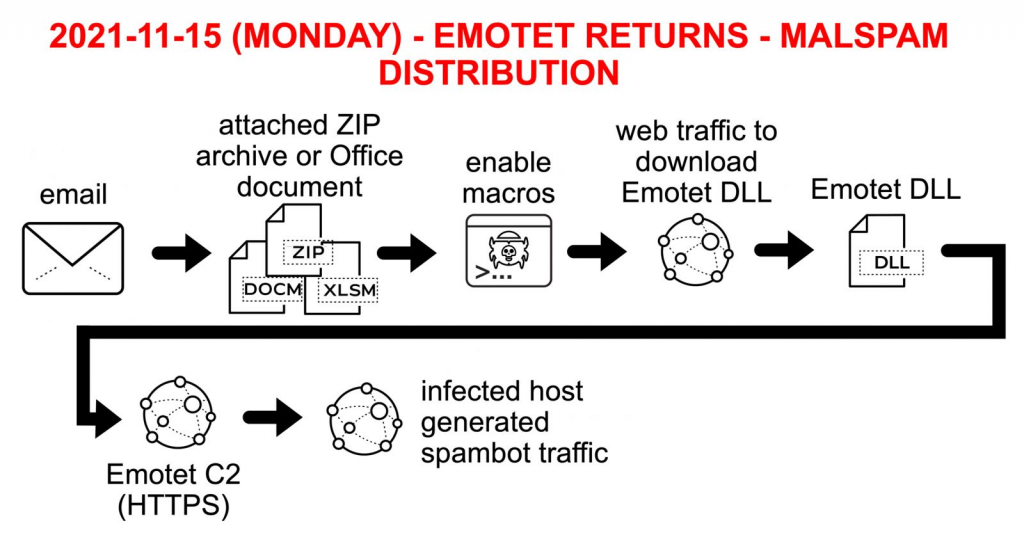
The typical Emotet attack chain playbook is as follows (Source: PaloAlto):
- Word doc infiltrates via email. Macros are enabled.
- Once opened, VBScript macro(s) load, executing PowerShell script.
- Script downloads primary DLL binary as a loader.
- Loader adds further DLL binaries able to self-update.
- Last DLL jacks valuable data or breaches more with C2 servers’ help.
New Emotet Variant
Let’s take the thoughts of cyber threat intelligence analyst at San Francisco-based Digital Shadows – Stefano De Blasi. He thinks it’s likely rebuilding its infrastructure using part of a pre-existing Trickbot.
It’s widely thought that the Emotet operators are jacking email chains, in order to redistribute malware… Email hijacking methods are increasingly used by threat actors, for their ‘social engineering’ campaigns.
Social engineering campaigns may take control of a target’s email account. Conversations are, for instance, monitored until an optimal moment arrives for inserting a malicious message into an existing thread. This type of cyberattack is more labour intensive but also yields a greater ROI.
So, this new emotet variant overall uses familiar paths: infected Office or ZIP files contain command-and-control (C2) payloads. Emotet is simply working hand-in-hand with Trickbot, the botnet that actually distributes it.
For the meanwhile, it will take time for threat actors to strengthen Emotet’s infrastructure. That said, its reputation makes it a hot pathway for many cyberattackers, seeking to scale up their operations.
New Emotet Activity
After the Emotet takedown, the new updated botnet (Epoch4, Epoch5) started stealing emails by spamming and reply-chain attacks.
The reinvented Trojan was first detected on 15 November and, in only 24 hours, managed to double its C2 infrastructure, from 8 active C2s to 14 – according to the team at abuse.ch research project of Bern University of Applied Sciences. Their advice? “Be prepared!” (Another security company tracked over 50 active C2 servers.)
Other than the new Trickbot, Emotet’s famous attack vector seems unchanged. It retains characteristics that make it an ideal ‘door open’ crowbar for ransomware groups.
What to Look Out For
Security teams needn’t diverge from basic cybersecurity practices, for the most part. A few tips on how to protect yourself against Emotet loaders:
- Network – polymorphic malware alters their code each time they load. So keep your OS and antivirus updated against known codes.
- Macros – restrict use of macros in Office files. Otherwise, old rules apply: avoid opening attachments from unknowns, carefully check headings first. Be especially wary of emails carrying a strong sense of urgency.
- Checks – against the Dutch National Police database: As part of its global remediation strategy, the DNP is conducting a criminal investigation of discovered addresses, passwords and usernames. See if your data has been compromised.
Conclusion
Emotet’s returned, and just in time for Christmas. (Is Emotet a virus? The world’s most dangerous.)
This prolific polymorphic adversary poses a significant risk. Emails gateways are the biggest way that it tries to get in, so use the best cybersecurity practices. But it shouldn’t demand a radical shift for blue teams, not yet at least.
Maintaining a high level of user awareness regarding phishing attacks is essential for effective cybersecurity. One effective measure to mitigate risks from malware is to restrict the use of macros in Office files, as this significantly reduces potential vulnerabilities. Additionally, implementing multifactor authentication adds an extra layer of security by requiring additional verification steps, thereby enhancing protection against unauthorized access.
Furthermore, monitoring for fake domains is a crucial practice to identify and prevent phishing attempts. Regularly scrutinizing website URLs, email addresses, and verifying the authenticity of communication sources can help in detecting potential threats. Educating users about the common signs of phishing, such as suspicious email content, unrecognized senders, or urgent requests for personal information, plays a vital role in promoting vigilance and preventing successful attacks.
It is also advisable to keep software and security applications up to date to ensure the latest patches and safeguards are in place. Conducting regular security awareness training sessions and providing resources to employees can further enhance their ability to recognize and respond appropriately to phishing attempts. By implementing these comprehensive measures, organizations can significantly reduce the risk of falling victim to phishing attacks and safeguard sensitive information and systems.



