Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
How to Efficiently Stop Browser Hijacking

We all know the frustration of having a pop-up suddenly explode over the screen and pester us with incessant advertisements.
Even worse, many of us have experienced our browsers suddenly growing a great number of new extensions or search bars like weeds in an unkempt garden.
These are examples of browser hijacking, and our guide today will go over what this troublesome Internet issue is, how to avoid hijacking, and how to deal with any hijacking that occurs regardless. Let’s get started.
What is Browser Hijacking?
Without getting too technical, browser hijacking occurs when unwanted software modifies your web browser settings without your permission. In other words, it takes control of your browser in one or more ways, which can then be used for various purposes.
Even without all the negatives we’ll discuss, this is bad for one overriding reason: you didn’t give permission for your browser to be controlled by another party
It’s a lot like someone remote controlling your computer and messing around with things. You wouldn’t want that to happen with any of your tools, and your browser being hijacked can lead to several serious risks.
Because Internet browsers often act as windows to the Internet at large, those who hack browsers can then open your computer up to all kinds of threats. While an Internet browser is a useful tool when under your full control, it can become a huge security risk or threat and your personal information may become compromised.

Regardless of the form that a browser hijacking takes, it’s always malicious and whoever performs the hijacking is always up to no good. Thus, you should always consider a hijacked browser to be a big deal.
Hijacked browsers can redirect you to unwanted sites, cause pop-up ads to suddenly start appearing, and expose your computer to potential malware viruses and other digital problems.
Where does browser hijacking come from? Most of the time, browser hijacking programs, viruses, or plug-ins come from Internet criminals. They primarily hijack browsers to get credit card or other financial details or to artificially boost the traffic to certain websites.
One great example of this can be seen when a hijacked browser transports you to different websites in rapid succession or forces you to view multiple pop-up ads one after the other. Boosting traffic is a way for Internet tycoons to gain revenue over time, so they’ll often employ hackers to wrangle swarms of hijacked browsers and artificially boost their traffic numbers.
Examples of Browser Hijacking
Browser hijacking can take the form of the examples described above, or it can be even more malicious. For instance, a hijacked browser can easily allow a hacker to access your personal information and delve deep into the sensitive data of your hard drive.
This can all happen even as you watch and without your permission, allowing said hacker to potentially steal aspects of your identity and cause unprecedented damage.
What do browser hijacking programs look like? There are several commonly known malicious toolbars and other browser software that are notorious for hijacking your browser either instantly or over time. Some of the most well-known include:
- CoolWebSearch
- RocketTab
- AskToolbar
- Coupon Saver
- GoSave
- Conduit Toolbar
- Babylon Toolbar
Wikipedia has arguably the most extensive list of various types of browser hijacking software and other harmful search engines. You can find it on their main encyclopedia page for browser hijacking.
Browser hijacking symptoms can take many forms. For instance, many automated bots or malware bugs can change the settings of your browser. This may not sound too bad at first, but it can lead to other browser security breaches and further risks.
Your homepage can suddenly change, or your browser search engine may shift without your consent. Many search engine companies will employ these means to get people to use their search engines when it becomes too difficult for the computer user to fight back and return to a tried-and-true search engine like Google.
They can also cause various webpages to display improperly. Some malware viruses are designed to prevent you from visiting the websites of certain companies’ competitors.
One of the more common symptoms of browser hijacking involves the explosion of new plug-ins or toolbars in your Internet browser. Suddenly all these extra (usually colorful) tools blast across your browser and make it incredibly cluttered and difficult to navigate. Before you know it, you can actually click on several plug-ins and install various programs on your computer.
These symptoms are particularly harmful to older folks who may not have the same level of computer literacy as most adults these days. In addition, lots of older people have less patience to deal with browser hijacking shenanigans and may intentionally click on proffered advertisements just to get them to go away.
Ultimately, browser hijacking software or viruses can come from lots of sources. You may accidentally pick up a browser hijacking bug from visiting a particular website or from using a search engine riddled with the stuff.
There’s no limit to the creativity that hackers will employ in order to hijack your browser, so understanding the risk that hijacking poses is necessary if you want to adequately defend yourself.
The Impact and Risks of Browser Hijacking
The reasons why someone may try to hijack your browser are almost as varied as their potential hijacking methods. But rest assured that the reason is never good. Several common motivations for browser hijacking include persistent advertising displays, information theft, or even spying on several users. Spying can take place both for general data collection or for identity theft purposes.
Many skilled hackers will drop into your browser very temporarily to capture critical information without alerting you to the presence of consistent browser hijacking software.
For instance, they can take temporary control of your browser when you log into a page with sensitive information like your bank account. They can even use this to find your Social Security number or answers to your security questions, making it easy to get access to your other accounts.
Since most people use the same few passwords or security question answers for the majority of their secure accounts, this makes hackers’ jobs of stealing personal information a lot easier.
In many cases, cybercriminals can access various financial accounts and either steal money directly or the financial data itself. They can then sell that data on the dark web and allow others to steal from you passively or all at once.
Horror stories of peoples’ bank accounts suddenly diminishing overnight aren’t fabrications meant to scare people off the Internet: they can be very real.
Even worse, it doesn’t take a master cybercriminal to use browser hijacking software or viruses. In fact, there are several otherwise legitimate marketing companies that ride the line between illicit and legal activity, using browser hijacking software to monitor which websites users visit and record how much time they spend on certain websites.
This data can be invaluable for marketing purposes, as they can utilize it in their own ad campaigns or sell it to other marketing companies for a hefty price.
Pop-Ups
One of the most common types of browser hijacking is something most people don’t know is part of the same larger problem. Pop-ups occur when various vendors or websites force unauthorized software programs directly into your browser window.
This application usually takes up the whole screen and may make it particularly hard for you to exit the pop-up; in essence, they force you to consider the advertised product or service.

Many pop-ups even come loaded with other malware or virus bugs that can be injected into your computer not unlike a biological counterpart whenever you accidentally click the wrong button or use the search engine proffered. Even if the pop-ups aren’t explicitly malicious, these files take up valuable storage space and will always slow down the processing speed of your computer.
How to Prevent the Most Common Browser Hijacking Methods
Browser Extensions
Browser extensions are helpful add-ons or plug-ins that can improve the performance or versatility of your browser. Lots of people see these colorful or attractive add-ons and think that they are boosting the value of their browser, but they’re often wrong.
In fact, many browser extensions can slow down the performance of your browser and make it vulnerable to hijacking.
Even extensions that are ostensibly developed to protect your browser may hide special scripts that can secretly hijack your browser and give a hacker a backdoor into your browser’s controls or provide them with key information.
Dealing with compromised browser extensions or add-ons is multi-angle. First and foremost, you need to remember to check reviews by developers and other users to determine whether a plug-in or extension can actually be trusted.
User experience is the first line of defense, particularly since many browser hijacking scripts are very well hidden and don’t manifest until sometime after installation.
Checking for a plug-in’s reputation is as simple as Googling it.
Then you should consider what the extension is supposed to do or provide. Read the installation instructions or features list whenever you consider installing a new extension.
Try to imagine whether a permission or requirement is actually needed for the plug-in in question. For instance, a simple list saving extension doesn’t need permission to read all the things on every page you visit or access your contact list. This type of extension is likely a mask for a malicious browser hijacking bug.
Above all else, only install browser extensions or plug-ins you’ll actually use. If you don’t need them, get rid of them; they’re only taking up space on your computer.
Installation Tricks
One of the most common ways in which hackers hijack browsers happens when people are tricked into installing different malware bugs. Many third-party developers or software makers will include malware bugs as part of the installation process for another offered program or product. For instance, say you want to download a music synthesis program but it comes with several caveats.
Lots of people will click through the installation windows without fully reading the agreement. In many cases, certain boxes are already checked, indicating implicit agreement to install additional plug-ins or toolbars in your browser. In this way, the program creator can claim plausible deniability if you ever try to sue them or accuse them of unlawfully installing software on your computer.
The best way to stop this browser hijacking problem is to read all installation instuctions carefully. Some are even worded in particularly tricky ways; for instance, some browser toolbars will only be installed if you uncheck a box. This trick is designed for those who are otherwise prepared for browser hijacking schemes.
You may need to click an advanced tab or manual checkbox in order to find options to deselect downloads or installation agreements. As you can see, many browser hijacking malware creators will make it as difficult as possible for you to avoid installing their garbage.
Read each word carefully whenever installing third-party software. Even when you purchase software from major companies like Google, they often include browser hijacking add-ons or plug-ins as part of the standard installation process. Take charge of what you put on your computer and don’t “agree” to let someone install any browser hijacking software.
Phishing Attacks
Another super popular browser hijacking method involves tricking people into visiting websites or downloading malicious software through emails.
Emails are incredibly low effort and cost-effective on the part of the hacker, as they can send out thousands of emails in mere minutes. It’s like casting an extremely wide net into the Internet’s ocean. Even if they don’t get many fish, they’ll almost certainly get some.
Again, older folks or those who aren’t particularly Internet literate are more vulnerable to this tactic. They may find an email that is attractively crafted and composed specifically according to their interests. They’ll download the attachments included in the email, which will automatically install browser hijacking software or malware.
In very sophisticated cases, just clicking a button in the email (like a link) will install the software relatively instantaneously.
Dealing with phishing emails is very simple, thankfully. First and foremost, knowing what phishing emails look like is the best way to avoid clicking on them in the first place.
Over time, you’ll learn what your spam filter automatically keeps out of your main inbox. You can usually train your filter to recognize more sophisticated phishing emails over time, too.
These emails are usually sent from addresses with odd endings, like, “@ph.ac.tr.ar” or something similar. They’ll also usually be written with improper grammar and spelling or have long and strangely winding stories.
Remember, these emails are rarely handcrafted and are usually formed with a template so they can be mass-produced.
It’s not too hard to see through the deception once you know what to look for.
Try not to ever click on a phishing email in the first place to avoid accidentally clicking an infected link. But what if you aren’t sure about a link in an email that otherwise looks legitimate?
A good trick is to right-click the link, then copy and paste it into a Word document or text tool like Notepad. This will allow you to see what the address looks like in raw form.
It’s a good rule of thumb to only visit URLs that include “https” in their name, as this indicates a level of security and legitimacy that spammers are unlikely to have.
Other Protection Methods
Google, being arguably the premier Internet presence in the world, has a special safe browsing list. In a nutshell, it’s a list formed as Google keeps active track of harmful websites.
Their Safe Browsing service checks URLs against their database of unsafe web resources. If the service detects that you’re about to visit a potentially harmful website, they’ll let you know and give you time to direct away.
It’s one of the best publicly available tools since it’s frequently updated with the latest potential threatening websites.
You can also frequently clean your directories and histories, especially if they let you get rid of cookies. Cookies are small automatic bots used by various programs and websites to keep track of your browsing habits and make it easier for you to revisit the same website multiple times.
But cookies and other digital flotsam can make it easier for hackers to hijack your browser.
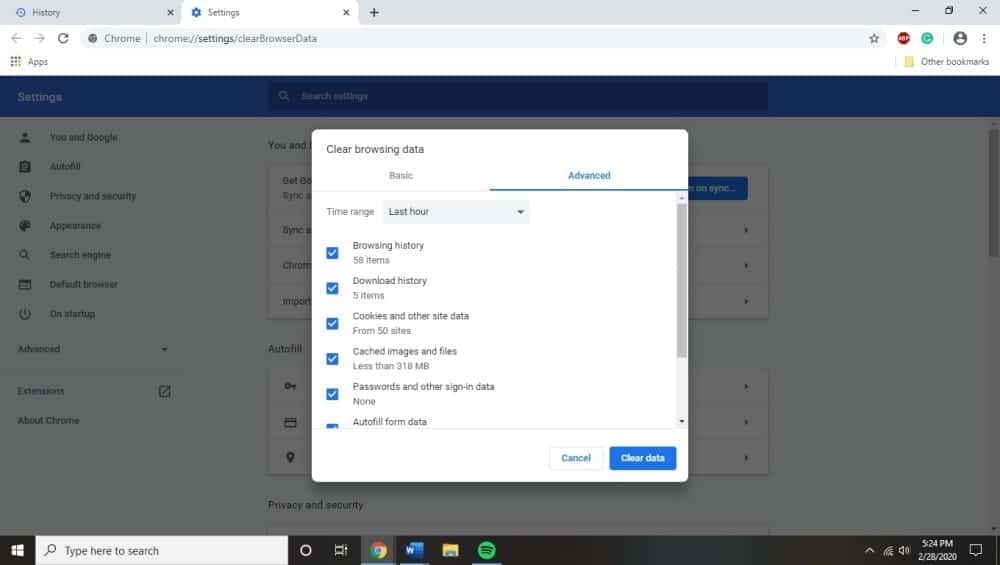
Clearing out your history and directory regularly (about once a week) is a great way to ensure that there is as little chance of your browser falling victim to hijacking from these sources as possible. Additionally, remember the age-old adage that nothing is ever really free.
Free programs often come with lots of strings attached in the form of browser hijacking extensions or other malware bugs.
It’s almost always better to go with a paid service for something you truly need, as you can be more assured that they aren’t loading it up with lots of extra software as a tradeoff.
Finally, make sure that you frequently update your chosen web browser and have your operating system up to date.
Doing both of these will allow your browser and operating system to maintain high security standards and receive the typical security updates developers push out every month or so. It’s a great passive way to increase your overall security and avoid super common bugs.
Getting Rid of Malware or Viruses that Cause Browser Hijacking
Of course, some browsers can become hijacked because of malware or other viruses. These viruses deliberately take control of your browser and install extensions or other tools to help hackers gain control of your browser settings.
Obviously, the first line of defense is excellent antivirus. Having a subscription to a top-tier antivirus software service is a must in this day and age. These software services will be constantly updated and often come with tools to help you regularly scan your computer for malware and eliminate it if any is detected.
However, some browser extension malware can circumvent your antivirus defenses. It’s just a matter of your antivirus software not recognizing the malware because of its code or structure.
In this case, you might need to reinstall your browser fresh. This involves uninstalling your browser manually from your control panel or programs list.
Once uninstalled, you can then reinstall the browser by downloading it fresh from the Internet. You need an additional browser in order to reach the Internet after you uninstall your browser of choice, of course. Keep this in mind before you uninstall your primary browser.
More drastic solutions might see you completely wiping your computer and rebooting the operating system from the ground up.
Windows and macOS both allow this feature, but it often includes wiping away valuable data or files that you might want to keep. Only do this as a last resort.
If you’re not at that level of seriousness yet, you might be able to remove adware or malware from your browser depending on your browser type.
Windows
Uninstalling harmful programs from Windows is pretty easy.
Firstly, you’ll head to the control panel by typing in the same words in the search box at the bottom left corner of your screen.
This should allow you to find an “uninstall a program” button under the “programs” category. Next, you can select the program that you think is causing you trouble, click it, and hit the uninstall button at the top of the corresponding toolbar.
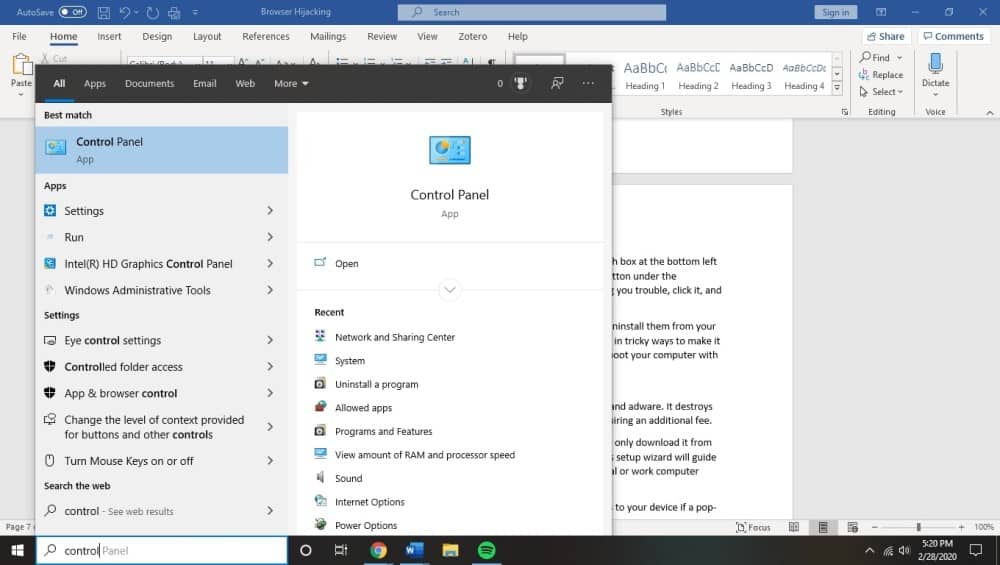
Many programs will require you to click through several steps in order to fully uninstall them from your computer. Be sure to read things carefully; some harmful programs are worded in tricky ways to make it supremely difficult to actually get them off your computer, and may instead reboot your computer with a fresh version of the software installed once more.
Malwarebytes
Malwarebytes Free is another great free tool you can use to get rid of pop-ups and adware. It destroys lots of malware bugs that other antivirus software miss frequently without requiring an additional fee.
To start, download Malwarebytes and install it on your computer. Make sure to only download it from the official site to avoid the problems we’ve been discussing.
The Malwarebytes setup wizard will guide you through the installation process. Identify your computer as either a personal or work computer when the appropriate window blooms on your screen.
Once it’s finished installing, go ahead and allow Malwarebytes to make changes to your device if a pop-up occurs asking permission. Malwarebytes is a trusted program.
Next, click the “Scan” button once Malwarebytes is active on your computer. This will initiate an automatic update sequence and begin to scan your computer for different malware. After the scan completes, you can then click the “quarantine” button, which will lock away any viruses that Malwarebytes detected.
You’ll then need to restart your computer and finalize the malware removal process and any harmful registry keys.
HitmanPro
Another popular scanner, this program uses cloud science to scan for malware. In a nutshell, HitmanPro sends any suspicious files to the cloud to be scanned by separate antivirus engines created by both Bitdefender and Kaspersky: popular antivirus developers.
HitmanPro isn’t free, and costs about $24.94 for one year for use with a single computer, but it’s well worth the cost if you have a particularly hardy virus you really need to get rid of.
You can download HitmanPro from their main website, then install it once it’s finished downloading on your computer. Like with Malwarebytes, go ahead and give the software permission to make changes to your computer.
After it’s finished installing, you can perform a system scan, which should be the default function proffered once you boot up the program for the first time.
HitmanPro will scan your computer over a few minutes, after which you can click “Next” once again and remove any malicious programs found.
Be sure to click the “activate free license” button to use this program for 30 days free. You may decide to continue with the software once you see what it does for your computer.
Resetting the Browser
You can alternatively reset your browser settings, which might be a creative solution to get rid of various redirects or browser hijacking plug-ins. The process for this is pretty similar across different browsers, but we’ll go through each so you know exactly what to do. In addition, saved bookmarks and passwords may not be cleared or changed depending on the browser in question.
Chrome
For Google Chrome, begin by clicking on the menu icon and then clicking the settings button. This main menu button is represented by three vertical dots. Clicking this should create a new settings window or tab depending on your consideration. Scroll to the bottom of this page and click on the link marked “Advanced”.
Next, click, “reset settings to their original defaults” by scrolling down until this section is visible. This will result in a confirmation dialog being displayed. It’ll detail any components that will be restored to their default states; double check this to make sure everything looks good before finalizing the process by clicking “reset settings”.
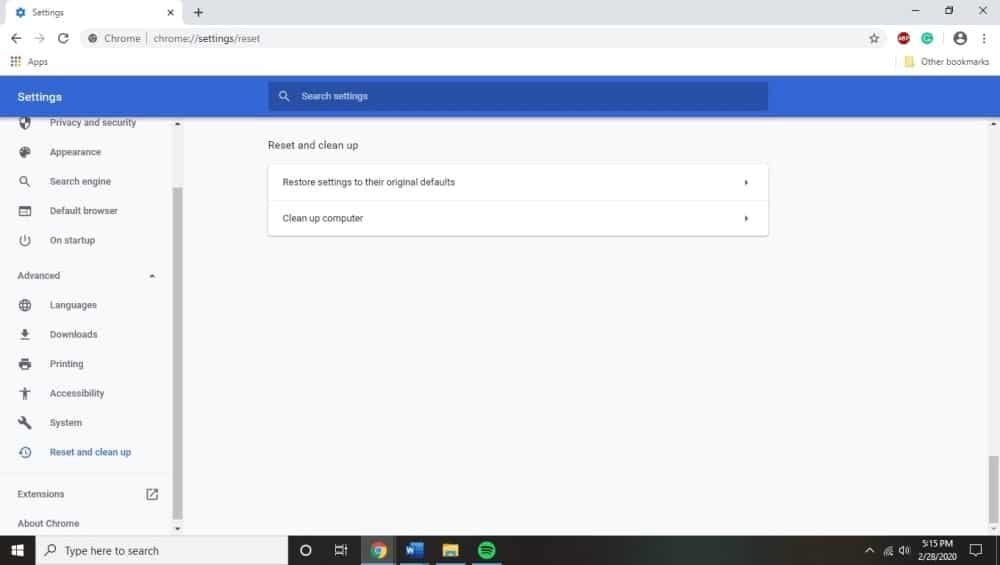
At this point, your browser should be completely reset, and you can install antivirus plug-ins to hopefully prevent this from happening in the future.
Firefox
Click on the main menu button in your Firefox browser, which is in the top right corner and represented by three horizontal lines. A drop-down menu will appear, at which point you should select the “help” button.
From there you can click on “troubleshooting information”, then “refresh Firefox”, which will appear in the upper right corner of the same page. After clicking this, clicking “refresh Firefox” will cause new confirmation window to open. Click “finish” to finalize the process and restore the browser to its default settings.
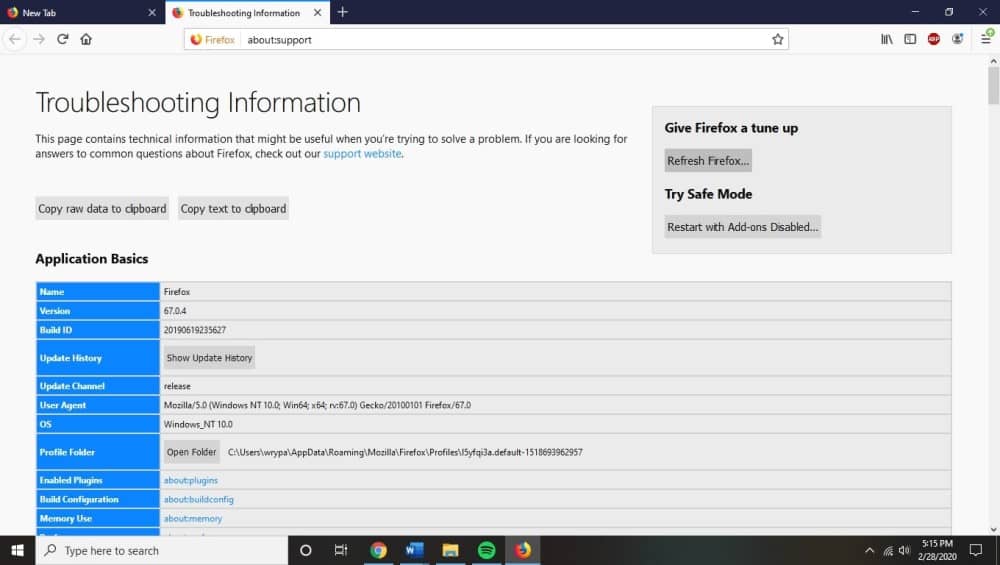
Interestingly, Firefox stores all of its old data from that profile in a new folder that will be placed on your desktop. You can potentially use this information to restore your original browser settings if the reset didn’t fix your hijacking problem.
You can alternatively delete it if things are back to normal.
Microsoft Edge
For Edge, click on the main menu button in the top right-hand corner (three horizontal dots). Then click the “settings” button that appears afterward. The left side of the window should have a “reset settings” button as well.
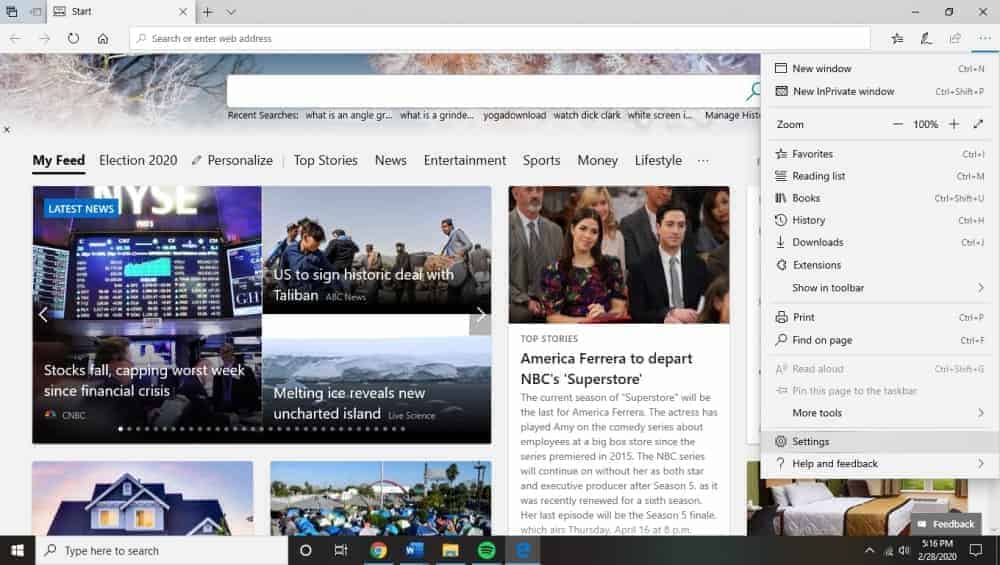
The new window will include a “restore settings to their default values” button: click this now.
Click through the confirmation dialog, as it’ll tell you which components will be restored to their default states.
Internet Explorer
Internet Explorer is oddly slightly different from Edge, even though they are both made by Microsoft. Open your Internet Explorer browser and click the gear icon in the top right-hand corner of the interface. Click “Internet options”.
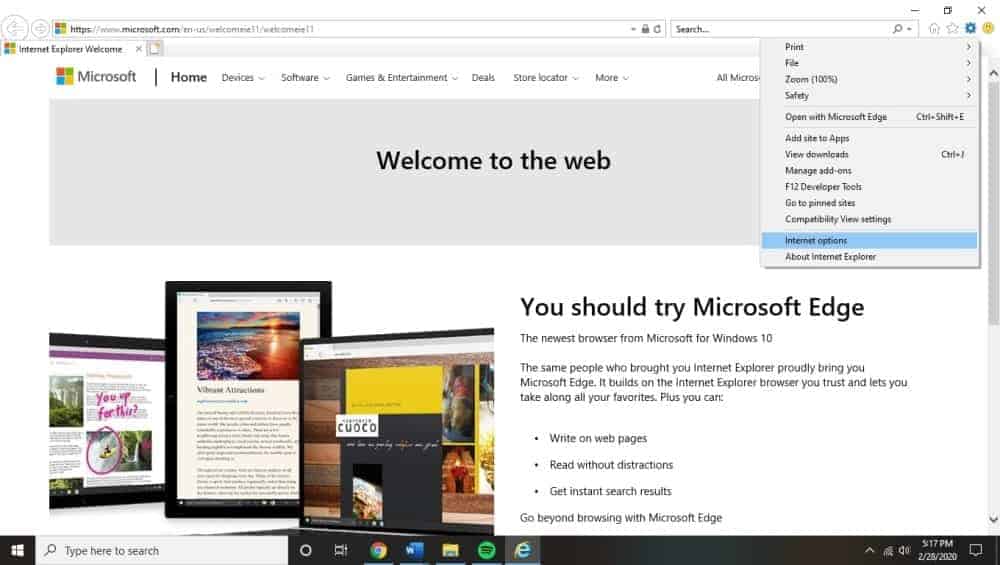
You should then be able to select the “advanced” tab, then the following “reset” button. This will bring up a new section, at which point you should check the “delete personal settings” before clicking the reset button to finalize the process. The final confirmation dialog box will include a “close” button to let you know that you’ve finished.
Summary
Overall, while browser hijacking can be quite annoying and potentially risky for your security, it’s a threat that can be overcome with vigilance and the right program assistance. Browser hijacking is a constant threat for anyone who enjoys the benefits of the Internet, but avoiding:
- free programs
- installing programs without reading all of their terms and conditions/requirements
- downloading plug-ins or add-ons that you don’t really need
- avoiding phishing emails
- not visiting websites that are not secure
This will all go a long way toward keeping your browser safe from hackers and improving your browsing experience. If you do ever encounter a browser hijacking bug, there are lots of different solutions you can bring to bear on the problem, ranging from antivirus removal services to browser resetting. Good luck!




