Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
China’s New Data Security Law: Why Businesses Need to Know About it

Mid this year, China’s new Data Security Law (the ‘DSL’) was passed by its national legislature: the Standing Committee of the National People’s Congress.
Since September, the DSL has been in effect, and marks China’s first comprehensive data protection ruling. It carries their strongest consumer protections at the global scale to date.
Fines reach upwards of 50 million Chinese yuan (roughly A$10.86 million), or 5% of an infringing company’s annual revenue.
While I have my own take on China’s approach to personal privacy (which you can view for yourself), in this guide I’ll mostly stick to practical business level implications instead of discussing the personal privacy implications of this.
Table of Contents:
Scope of New China DSL
In short, the DSL gives users opt out rights regarding targeted advertisements, effectively requiring companies to let users opt out.
Furthermore, companies need to get consent from users before they collect personal data. They must notify users if they intend to share any of this with third-party companies – who themselves need to clear consent from users.
Let’s explore what this new law means, in greater detail:
Scope of regulation and global jurisdictional reach
Governing powers of the DSL reaches extraterritorially, beyond activities conducted within China’s borders – concerning anything with the potential to injure China’s public, legal or national security interests, which includes those of any Chinese organisation or citizen.
This encapsulates how data is processed, which includes storage, use, transmission, disclosure, collection, and provision of data – as well as managerial oversight.
The implications of the DSL and PIPL enforcement are unclear; how discrete regulatory penalties will be, and extraterritorial reaches of the law will probably be buffered by pre-existing agreements and treaties that China has with other countries.
But the DSL does grant numerous Chinese federal authorities to regulate data security concerns:
- At the local level, regulatory bodies are responsible for securing data in their concerning industries and areas, and for categorising certain types of key data.
- On a national scale, data security approaches and key policies are being overseen by China’s Central National Leadership Organ – who are working in tandem with other data management bureaus.
China DSL Penalties
They’re pretty severe: violations of the data security law will result in imposed fines of up to 500,000 yuan (a bit over A$100,000). Non-compliance is also metered down to the individual level, potentially resulting in additional fines, with remediation being a mandated requirement.
Failure to adequately remediate triggers a warning, first; and for major security incidents causing catastrophic large-scale breaches for instance, noncompliant entities can face up to a 2,000,000 yuan fine (a bit over A$400,000) – with the invalidation of business licences and possible suspension of operations.
Finally – through China’s New Data Security Law, their Central Government has been given judicial powers against foreign entities and states acting against China’s trade and investment rights, to do with data technologies.
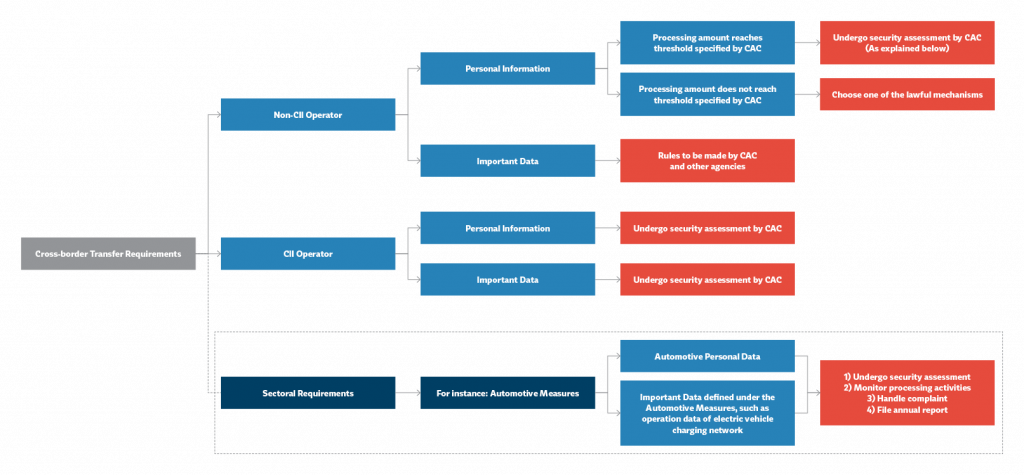
Data Migration Cross-Border
“Important data” is catalogued under a unique framework for CIIOs, and one for non-CIIOs. The former is obligated under the CSL: mandating that important data, collected in China, must be locally stored.
To migrate data outside of China, for a legitimate business reason, data must first undergo a security assessment that meets P&P’s of the Cyberspace Administration of China (CAC).
Requirements for non-CIIOs have yet to be established. But overall, the DSL will mean no organisation or even individual entity in China will be allowed to transfer data stored in China to any foreign enforcement or judicial body.
Those who don’t comply with this face a fine of up to 1 million yuan (about A$200,000) with extra fines for responsible individuals. For the most serious infringements, this rises to up to 10 million yuan (A$2 million) alongside the invalidation of business licences and a possible operational suspension.
Categorisations of data
The DSL and PIPL are being established in collaboration with China’s “CSL,” Cybersecurity Law: in 2017, the CSL was created to tighten regulations of data networks and the protection of information. (China’s Personal Information Protection Law, known as the PIPL (‘China: DSL vs PIPL’), was passed in August 2021, only just coming into effect early last November.)
Important Data
The CSL first established the idea of “important data” definitions.
Which means data that – due to where it will be processed – requires extra protection, approval from a security assessor, and is obliged to be reviewed at the local level before its cross-border migration by a critical information infrastructure operator (“CIIO”).
CIIOs are mostly bodies responsible for overseeing industrial sectors in China that include energy, finance, information technology, transportation, and communications. The CSL only requires this process for CIIOs holding important data. But the DSL increases its scope to include all businesses that need to process important data extraterritorially.
National Core Data
The DSL also establishes the idea of “national core data,”which is a data class with tighter regulations due to its potential influence on national economic and security interests.
So far, the scope of national core data also encompasses things that could impact key public interests and the livelihoods of citizens.
Data operators are also obligated to cooperate with requests from China’s judicial authorities on national security matters, or face criminal and monetary penalties.
So far, it’s unclear how businesses can evaluate their data activities to adequately secure national core data – but the regulators are taking it seriously enough to threaten fines of up to 10 million yuan (roughly A$200,000).
What to Do Next
Much of the DSL mirrors what you find in other data security laws, especially the GDPR.
There are few notables, however; mainly the broadness of its framework, which goes further than the GDPR. Not only will personal data of Chinese citizens be regulated, but also any data considered important to China’s economic interests and national security.
This represents a potential landmine. Global organisations should be especially wary of much tighter data migration restrictions, which also surpasses the GDPR.
Some of the formulations for its implementation are still fuzzy and will need further regulatory legislation, so companies doing business inside and with China should review their data transfer and processing activities, checking for compliance gaps.
We overall recommend global companies, in business with China, evaluate to what extent the DSL and PIPL apply to their data operations, and what further security check-points should be fulfilled.
Seeing as China’s new data security law is already active, the time is already upon you to ensure you’re compliant with its extensive obligatory list. Company should consider these following steps, to assess risk:
- Data mapping exercises – Have you undertaken steps to identify if your company extraterritorially sends data acquired inside China? Of this portion, can you identify any processing gaps that may compromise Chinese economic or national security interests, thereby increasing your risk of regulatory scrutiny.
- Evaluate your data – What portion of your data is likely to fall into the ‘important data’ or ‘national core data’ DSL classification?
- Buffer data migration risks – Can you shrink data transfer & processing security gaps; and do you have a redundancy/remediation plan for security emergencies?
- Regular risk assessments – Are you tracking your operational data risk, and validating this by giving reports to informed auditors?
China-ready DPO – is someone responsible for making internal procedures for Chinese data protection, transfer, and compliance; have you established an oversight board for reviewing compliance and data security?
My Take Away
Allow me to briefly share my thoughts on the impact of the Digital Security Law (DSL) on personal privacy in China…
While we’ll never know whether Tik-Tok spying on Aussies was a real thing, it seems unbelievable (for a country that disallows the practice of personal non-state-approved religions), to be super concerned about personal rights.
I think what we’re seeing here is a further clamp-down of any threat to China’s domestic and foreign powers over data control and surveillance; a sort of monolith, a government that is insulating itself from its own growing private sector and the US (by limiting powers both have over citizens).
[The Hacker News (THN) did an interesting piece on all the ways it expands government control.]In essence, the primary objective of the Digital Security Law is to prevent the leakage of data that could have a substantial impact on China’s interests. Consequently, it is evident that the law is primarily focused on safeguarding governmental insulation from both external global influences and internal localized influences. This perspective may come as a surprise to readers, as it highlights the law’s emphasis on protecting national interests rather than solely addressing personal privacy concerns.
Conclusion
Back to the business practicalities – leadership needs extra caution around some uncertainties embedded in China’s new data security law, pertaining to definitions of “important data” – as mandates are operating at both local governmental and cross-border levels.
There’s a fair amount to go on so far.
For now, we are waiting for further rulemaking that will clarify the DSL’s guidelines, particularly with important and national core data. According to the DSL and PIPL, company data processors must – in summary:
- Monitor for possible gaps. If a security breach or gap is discovered, users should be promptly alerted; remediations are also a mandated must for continued operations.
- Have a suitable data security management program. That meets the DSL’s specifications at the technical level. This includes security awareness and training.
Issue and obtain data legally, as it pertains to the DSL and PIPL. In other words, accordingly with its limitations, scope, and personal user rights.