Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
How Does SSH Work? All You Need to Know

The SSH, also known as Secure Socket Shell or Secure Shell is an administration protocol that lets you log in and controls your remote servers securely over the Internet (which isn’t all that secure by itself).
The entire communication between two bodies (server and client) is carried out in an encrypted manner with the help of strong cryptographic techniques.
Such highly secure communication is much better than other unprotected login protocols like rlogin or Telnet.
SSH protocol provides a secure authentication and connection – input from remote users is transferred to the host. Then the commands or output is relayed back through an “SSH window.”
Any user, be it Mac OS or Linux, can directly login to their remote server via this SSH window.
Windows users may rely on PuTTY, as it is a powerful SSH client.
Benefits of Using the SSH Protocol
An SSH protocol plays a vital role in corporate network communications, as it can:
- Provide highly secure access to users into their remote servers
- Give secure access to automated procedures
- Allow automated and intuitive file transfers
- Allow the flow of commands between two parties remotely
- Manage and monitor network infrastructure efficiently
Now that we know what SSH protocol really is, let’s get into the details on how it actually works:
How Does SSH work?
For Mac OS and Linux users, implementing SSH protocol is extremely simple. While Windows users need to go for an SSH client like PuTTY to establish an SSH connection.
The SSH protocol will establish a client-server model to carry out a secure authentication procedure between two parties and encrypt data that’s being transferred between them.
The two parties viz. server and client, each play a vital role.
- The server component looks for connections via a designated port. Its job is to negotiate a secure connection, authenticate the connection and create a secure environment for data transformation.
- On the other hand, the client component instigates the initial TCP handshake process with the server and negotiates a secure connection. Further, it is also responsible to check and authenticate the server’s identity using public-key cryptography and revert back with its own credentials for authentication as well.
Once the initial setup completes, the SSH protocol makes use of powerful symmetric encryption along with hashing algorithms to make sure the integrity and privacy of data transmission between two parties remain secure.
Authentication with SSH Keys
SSH window may utilize various methods for user authentication. But the most popular method amongst those is via public keys or passwords.
Generally, the public keys authentication process is used for automation. Even system admins use this method for quick single sign-ins. The process requires you to have a cryptographic pair of keys: the private key and public key.
The public key is configured on a server, which will authorize access to the server only to those users who have a copy of the private key.
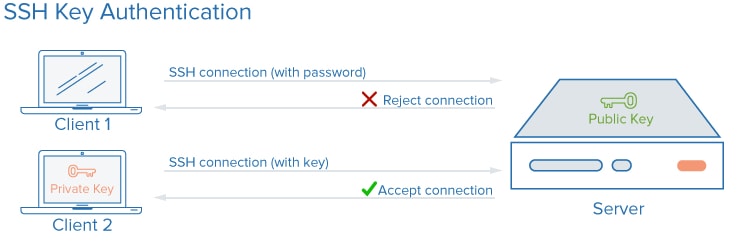
These authentication keys are known as SSH keys.
These keys grant access to users just like passwords and usernames do when we log in to websites or use great password management applications.
The biggest advantage of a key-based authentication procedure is to ensure secure automation. Automated SSH file transfers allow for the smooth integration of applications and better configuration management.
Data Privacy and Integrity Protection
As a secure connection is established between two parties i.e. SSH client and server, the data encryption process initiates as per the parameters negotiated initially during the setup. Two parties agree on which symmetric encryption algorithm will be used and create an SSH key for future use.
The industry-standard encryption algorithms make sure the traffic between the client and server is fully protected. Additionally, the SSH protocol also inculcates techniques to make sure the integrity of the transmitted data remains intact.
These techniques include the use of standard hashing algorithms.
Types of Encryption Techniques
1. Symmetrical Encryption
Symmetrical Encryption is when the client and the host- both use a secret key to encrypt and decrypt a message. This means any one party that has this key can decrypt the transferred data.
The symmetrical encryption is also referred to as “shared secret” or “shared key” encryption. Most commonly, only a single key is used for all operations, but some sessions may use a pair of keys where they can easily calculate the opposite key.
With the help of symmetric keys, the entire communication is encrypted during the SSH session. Both the parties viz. client and the server will acquire a secret key as per agreed terms. This secret key is never shared with a third party. The whole process of deriving a symmetric key is done with the help of a key exchange cryptographic algorithm.
But is this algorithm secure?
Such a key exchange cryptographic algorithm is completely secure as it does not really transmit the key between participants. Rather, the both the participants will share a crucial public data, based on which they have to individually determine the key.
If an unwanted third party captures this piece of shared data, they won’t be able to compute the secret key as they do not know the cipher being used.
Some interesting facts:
- Symmetrical encryption techniques can even protect password authentication from sniffers.
- The secret token is unique to every SSH session, and it is created right before the authentication process. Once the symmetric key is created, all the data transmitting between two parties must be encrypted by this key.
- Now, there are many symmetric key cipher systems out there, such as Blowfish, AES (Advanced Encryption Standard), CAST128, 3DES (now retired), and Arcfour, among others.
- The client and the server- both agree upon which encryption cipher to use prior to establishing a connection. This is done by publishing a list of their supported ciphers as per their preferences. Whichever cipher system tops the client’s list and is also available on the server’s list is used as the final algorithm.
2. Asymmetrical Encryption
Unlike symmetrical encryption which uses one or a pair of keys, the asymmetrical encryption makes use of two distinct keys to encrypt and decrypt the data. These keys are called the “private” and “public” key, together referred to as “public-private key pair”.
As you can guess, the public key is openly shared with involved computers. Though the public key is somehow linked to the corresponding private key, it CANNOT be used to mathematically calculate the private key.
The mathematical relation between both these keys is quite complicated- any message or command encrypted by a computer’s public key will be decrypted by the private key of the same computer only. Such a one-way technique means that the public key won’t be able to decrypt any messages encrypted by the private key, nor it can decrypt its own message.
For the established connection to be secure, the private key must not be shared with third parties. This NOT sharing of the private key is where the entire power of the connection lies.
That’s because the private key is the only element that can decrypt messages encrypted by its own public key.
Which is why, if any involved party who wants to decrypt a publicly shared message must have the related private key.
Here’s a short – and fun – video overview of how SSH authentication and key exchange works:
Some interesting facts:
- Asymmetrical Encryption is not used for encrypting the entire SSH session.
- Rather, it is only utilized during he initial key exchange algorithm of symmetric encryption technique. Before the connection is established, the client and server both create temporary asymmetric key pairs (public-private keys) and share their private keys to generate a “secret key”. This secret key is further used for symmetrical encryption.
- As soon as a secured symmetric connection sets up, the server will use the client’s public key to create and transmit it for client authentication. If the client can execute the decryption of the message successfully, it means that it owns the corresponding private key.
And, that’s when SSH session begins.
3. Hashing
Hashing is a one-way cryptographic technique used in SSH sessions. These one-way hash functions are never supposed to be decrypted.
Rather, these hash functions only create a unique “signature” of a fixed length for every input message. It does not expose any clarity regarding the message, hence, making it difficult to predict or exploit.
Moreover, these functions cannot be reversed.
Why?
Because, the cryptographic hash is generated from a specific input message, but the hash cannot generate that specific message.
Meaning, if the client has an input, they can create a corresponding hash signature and compare its values to see whether they own correct input or not.
The same hashing function and message MUST generate the same hash signature. If a different hash is created, that means the data is modified or exploited in some way or another.
Some interesting facts:
- Hashing technology uses Hash-based Message Authentication Codes (HMACs) to check the authenticity of messages and maintain data integrity. This verifies that the received message was not exploited or modified in any way.
- As mentioned above, the initial symmetric encryption negotiation takes place between two parties and that’s when MAC (Message Authentication Code) is also selected.
- The selection process is similar to selecting cipher systems stated above- a list of MAC choices is created by the client as well as the server. Whichever MAC option tops the client’s list and is also supported by the server is then chosen.
- Each transmitted message MUST contain a MAC, which will be calculated with the help of symmetric key, message contents and packet sequence number.
Evolutions in Network Management
As more vendors enter the IT and network security space, organizations often find themselves with a heterogeneous mix of network management tools. So it’s no surprise that SSH is being abandoned for newer, more secure network management protocols.
Some examples include SSH, WMI, Telnet, SNMP Monitoring. WMI, or Windows Management Instrumentation, is Microsoft’s implementation of the Web-Based Enterprise Management (WBEM) and the Common Interface Model (CIM) management technologies for distributed environments.
Often referred to as “SSH on Steroids” following a comment at the BlackHat 205 conference, WMI supports WMI execution of code as well as object serialization. Unlike SSH, WMI enables scriptable configuration via WSMan “drive” in PowerShell.
Conclusion
In conclusion, this comprehensive post has provided a detailed understanding of how SSH operates. It is our hope that this guide has shed light on the inner workings of an SSH session, as well as the security measures employed in this technology. While some may initially find these procedures overwhelming, they are, in fact, relatively straightforward.
The simplicity of the process lies in the fact that a computer can swiftly calculate a hash signature and authenticate the corresponding user within a matter of seconds. Although the underlying mechanisms may sound complex, they are inherently uncomplicated.
SSH leverages a range of encryption and authentication techniques to ensure the integrity of data and establish a secure connection between involved parties. By employing these methods, even if sniffers attempt to intercept the signal, they will only encounter encrypted data packets. Such a protocol surpasses the security capabilities of other protocols like Telnet and FTP.
We trust that this tutorial has served as an inspiration for you to harness various SSH technologies and create a robust system that aligns with your specific needs and requirements.



