Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
7 Strong Password Ideas in 2024

The best passwords hold up against dictionary and brute force attacks. But this doesn’t mean a good password isn’t simple to remember.
With these strong password ideas, you can make your account safe enough to store state secrets.
Table of Contents:
- Why do some passwords get hacked
- Strong Password Idea 1
- Strong Password Idea 2
- Strong Password Idea 3
- Strong Password Idea 4
- Strong Password Idea 5
- Strong Password Idea 6
- Strong Password Idea 7
- Technical Guide
- Using memory palaces
- Password managers
Why do some passwords get hacked?
The longer you’ve been using the same password, the higher the chance it’s compromised. Especially across several accounts. Why? Over the years, naturally, websites are targeted.
With every successful attack, a certain number of private account details are leaked to the hackers. Just registering puts you at risk.
How sites leak you 🚰
Let’s take 2020 – in that year alone, 64% of all company sites were breached (source: techjury). Many don’t immediately detect breaches. For instance, Equifax was hacked a few years ago. Leading to millions of very secure data points being stolen. During the investigation, it came to light that the Equifax hack happened for 6 months without its security team realising.
Although companies are legally forced to tell the customers when there’s a breach, they won’t always detect it right away. Which is why a strong password is a final failsafe.
Passwords to avoid ✖️
In case it needs to be said, stay away from silly or obvious passwords. Things like sequential numbers or letters get obliterated by brute force attacks. That goes for not using clever-clog answers like “password” as your password, or memorable keyboard paths like qwerty.
Choose unrelated passwords. Without any personal sourcing. This means avoiding your address, date of birth, name, etc. If an attacker targets you specifically, they’ll put at their disposal every bit of information they have about you. Don’t make it easy for them to make guess attempts.

Avoid using keyboard paths. For instance, it’s a common trick some users use to choose a personal password, such as their child’s name. Then to select keys on the keyboard that lie, for instance, above or to the left of each character.
But this once again makes you vulnerable to a brute-force attack – if you are specifically targeted and personal guess attempts can be made. Remember, substituting actual characters for visually similar ones or algorithmic substitutions is a piece of cake for brute-force bots.
Deliberate misspellings or other quirks. Adopt the same wariness with this approach, too. Using personal details with just a punctuation mark for instance could be a piece of cake for intelligent bots as long as information is known about you.
For instance, Jessica 1989 and Jessica $19.89 are not impossible for a brute-force attack to crack open. Or if you were to misspell a word to make it more unique. Brute-force bots spots also have databases for common misspellings… Now we know what’s doesn’t, let’s explore what does work:
Strong Password Idea 1 ➡️
Secret Agent method 🕶️
With the conclusion of the Daniel Craig portion of the James Bond franchise, you’ll need to take on the use of secret codes into your own hands.
The Bruce Schneier method is one the fastest and yet most impenetrable methods of password creation. Using basic cryptography, you’ll have a highly memorable password with more personal meaning to you than any secure pin code you’ve ever used.
How the Bruce Schneier method works
It’s as simple as deciding on a sentence that already has personal meaning to you, that you remember easily. You transform this into a password using a simple rule.
For example, let’s take the first two letters of every word in “Fly me to the Moon and let’s dance among the Stars” which would give you:
FlmetothMoanlemedaamthSt
Notice that we also capitalised the first letter of every noun and the first word. So this gives you a mixture of lowercase and uppercase letters, which is important. And an ultra-long password.
With the above example, you may notice that the first few parts are sort of guessable. Because the first few words of Fly me to the moon have very short words anyway, it’s easy to fill in the blanks at a glance. So try to choose a sentence either with longer words or less well-known.
Let’s go through a few examples and see which ones you can guess. This will give you a good indicator of whether your own choice is decipherable or not.
While it doesn’t strictly make a difference, if someone peeks over your shoulder while you type it in, it’ll be harder to remember at a quick glance.
OnRitoruthal
One ring to rule them all.
FrDaidogiada
Frankly darling I don’t give a damn.
ThnaBo,JaBo.
The name’s Bond, James Bond.
Final tips: Make it at least nine characters long. Go for rarer expressions 👆 than the ones used in my examples above. Finally, use a mixture of capitalism and lower cases. It’s all in your hands, 007.
Strong Password Idea 2 ➡️
Cryptic dictionary 📚
Dictionary attacks are one of the most rudimentary hacking methods. But they are overwhelmed by a few simple tricks that make you impervious even to brute-force attacks.
In fact, not using a single word as your password puts you at a head start. But you can create a genuinely strong password via a collection of words you decide on.
While the cryptic dictionary method is not as instantly memorable as the Bruce Schneier method, it’s still much more intuitive than trying to remember a bunch of random mixed characters – like something out of a barcode. Here’s how it works:
The unique passphrase approach
It’s simple. You’re going to use multiple words as a phrase. But keep things as cryptic as possible, choose uncommon or bizarre words.
The choice could be names of local businesses, celebrities, historical objects, any words you’re familiar with in other languages, and so on. A hacker may guess Bugger, but it would be unfathomably difficult to attempt to guess a strong password example such as the following:
BuggerWugger!WigginSalaamAlai
If you’re curious, these words are all important bits of vernacular used in the popular science fiction novel Ender’s Game by Orson Scott card.
To me, these words are all extremely memorable and contextually in order, but to the average person meaningless – and wholly unguessable by any bot. It helps if you try to build a mental image of the password as you progress along it. So that you only need to summon the image to mind, to recall the password.
Strong Password Idea 3 ➡️
Password generator 🎛️
Password generators are pieces of software that create random, custom passwords for users. They’re used across the board – commonly when first registering to a service and being automatically given an account, such as a bank account.
Typical passwords, for accounts that contain extremely sensitive data, such as financial, will be made up of mixed symbols, letters, and alphabetic characters, to the absence of any recognisable English or otherwise word.
This can make it tricky to quickly recall your password in the future. Which is why most users modify their passes to something more memorable. But for our purposes, random password generators that use English dictionary words are perfectly fine for designing a strong password.
Tips: Ensure that at least 3-4 words, of a good size each, make up your password. With none of them being everyday words. When generating your password, you can also make sure your device is not being intercepted, by using a VPN.
Password generator safety
When assessing whether a password generator is safe, you have to evaluate two things: the quality of the password, and the security of the generator from illicit third-party attention.
I suggest avoiding any online password generator tool – stick to additional services that come with a reputable platform, such as some A.V. tools, which perform anti-malware services primarily but can also have password generators as add-ons.
Strong Password Idea 4 ➡️
Substitution: Alphabet ➰
These take a little longer. But they have the same principle as the Bruce Schneier method.
Choose your sentence, which could be your favourite line in a personally favourite song of yours. Or some other random phrase you use. Swap the letter in the alphabet with the next one down, for each… Depending on the length of the password, these can (very theoretically speaking) take billions of trillions of years of computer power time to crack.
Epzssfnfncfsuifujnf
“Do you remember the time”
Nzifbsuxjmmhppo
“My heart will go on”
Tips: I prefer substitution passwords less because particularly savvy brute-force attacks take all sorts of algorithmic patterns into consideration, based on popular culture references. They take as much time to encode/decode for the user, who is trying to log in…
Which is why this may be more useful for those more special accounts you log into infrequently. There isn’t enough inherent randomness in this method for it to be rocksolid against that strategy. Try to use a line that only very few know.
Strong Password Idea 5 ➡️
Substitution: Vowels 📜
The same risks as listed above apply: Brute-force bots use instantaneous pattern recognition that is sometimes AI powered. As an illustration, think back to a time when you began typing out a word in your phone, and completely mistyped it…
In a few cases, you’ll have noticed your phone was still successfully able to suggest the correct word. And it gave you the option to modify your mistyped entry to the correct one.
This is the natural way that predictive learning software functions. Your most powerful defense against this form of natural cyber intelligence is to lengthen your random phrase, so that as many words as possible need to be protected.
And to keep it random rather than sourced from popular culture. (Just ensure it has personal meaning to you, while being nonsensical to most outsiders.)
How vowel substitution works
It’s extremely simple. Just choose a memorable phrase and substitute one vowel for another – for instance, e with u. (As always, use at least 12 characters, and make sure you keep the phrase random):
- Every Wednesday, we meet in the middle | Uvury Wednesday, wu muut in thu middlu
- My favourite Netflix show is Invincible | My favoeritu Nutflix show is Invinciblu
- I love bars when there’s free booze | I lovu bars whun thuru’s fruu boozu
Strong Password Idea 6 ➡️
Shortening words
Once again, choose a memorable phrase, but this time around remove the first 3 letters for each word (doesn’t matter if this deletes an entire word):
- You should see how I shape up on Fridays | sho sha Frid
- Football is my favourite sport after cricket | footb favouri sp af crick
- Four billion dollars, for the world’s most expensive nosebleed | F bill doll worl mos expens noseble (..bonus points if you can guess where that quote comes from)
Strong Password Idea 7 ➡️
Math approach 📟
Create a quirky mathematical Q&A and use that as your password. Some examples, to give you an idea of how easily this works:
- MyBaby+MyPuppy=6Legs.
- 920-620=300.
- Sunshine+Rain=Rainbow.
Technical Guide ⚙️
Now you know how to make a strong password – with it still being memorable. But before you leave, here’s a bit of education on how hackers actually guess at weak passwords.
Dictionary attack
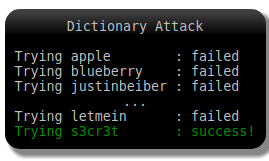
Just as it sounds, dictionary attacks are where hackers use a dictionary to try to guess your password. There won’t be a great number of combinations of numbers and symbols used – instead, the attacker will use lists of words available in any dictionary.
This is one of the most rudimentary ways to get somebody’s password. If you happen to use a word available in our dictionary, as your password, your only chance of getting through a dictionary attack is if your word is so incredibly uncommon that it isn’t available in most dictionaries.
Or if you use a string of words combined in unusual ways, such as ZeitgeistNovemberRainSludge.
Tips 💡 –
- No single word passwords: Make sure your password isn’t a single word.
- String together: Strings of multiple words disrupt this attack tactic.
- Rare words: You’re also better off using several unusual words.
Brute-force attack

Brute-force attacks simply throw everything but the kitchen sink at you, until striking lucky. The cyberattacker uses automation software, so that as many combinations as possible as quickly as possible can be attempted.
While it might seem like a rudimentary strategy, there have been some recent advances in the methodology. For instance, in 2012, one resourceful attacker revealed a 25-GPU cluster programmed to unlock any Windows password of eight characters or less.
This cluster was so effective, it was able to crack passwords containing uppercase and lowercase letters, symbols, numbers, all inside of six hours. Just a repeat, every parcel encountered of this specification was able to crack.
You might wonder how. The 25-GPU could make 350 billion guesses per second.
Making anything underneath 12 characters susceptible to being cracked. The guiding principle is the longer the password length, the better. Password length is crucial.
Tips 💡 –
- Longer is better: Keep password long.
- Use combinations: Use combinations of characters, mixing up cases/symbols.
- Don’t substitute: Brute force password crackers understand what characters can commonly be interchanged for alphabetic letters. In fact, they’re just that good as cracking common spellings with symbolic versions. So avoid substituting alphabetic characters with similar symbols. For instance, MOONCHILD with M00NC3ILD.
Phishing 📧
The most loathed of all cyber attacks. Phishing is where cyberattackers use various social engineering tricks to coerce, deceive, or pressure you into unknowingly giving over the proverbial keys to your account.
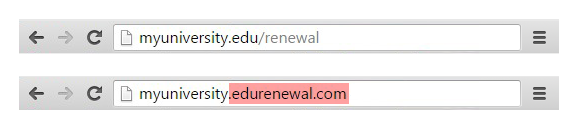
For instance, a phishing email message may falsely say there’s an issue with your credit card. It will tell you to click a link to correct things. You’ll then be sent to a replica site made to resemble your actual credit card company.
On the other end, the scam artists are silently surveilling your every move, hoping their ruse is winning and you are now typing in your password. The instant you do, it’s all theirs. (These scams are sometimes done over the phone.) Trust no stranger online.
Keylogging viruses
Keyloggers snapshot every one of your keyboard presses, letting the hacker record your passwords, and other activities. Zeus and Dridex are the two most used keylogger viruses.
All far programs that assimilate themselves through email attachments and are designed to focus on searching out login details for banks. To defend against this, you need a robust antivirus, know-how for defending against phishing, and good online hygiene.
Recycled credentials
This is simply when passwords and usernames gathered from other breaches get reused on random websites. Attackers try to gain access to sites, unrelated to the one actually breached, on the off-chance that it works. Credential recycling is sometimes called password spraying.
Cyberattackers typically amalgamate tens of thousands of unique credentials from a single breach. Because most people reuse the same password, this less targeted type of attack has high effectiveness.
Using memory palaces 🏰
In times begotten, needing to memorise huge amounts of information wasn’t an option because information wasn’t easily accessible.
It wasn’t until the 19th century that paper became affordable enough for the quantities needed to make up books in mass production. Furthermore, not many people were able to read and write. Which is why it’s no wonder that the ancient Greeks adored memory palaces. This technique is still used today by memory experts, who need to commit huge amounts of data to memory.
Also known as the mind palace, journey method, pegword method, or the Roman room – memory palaces let you use your spatial memory, to mentally arrange otherwise random and meaningless information and easily remember it.
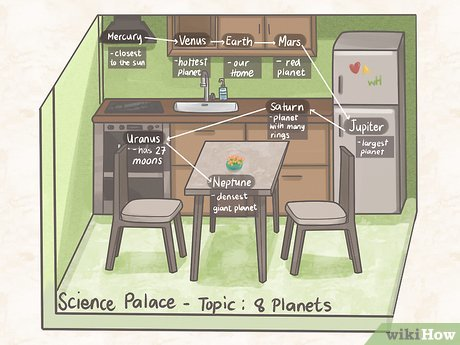
Steps:
- Choose a real location or space you are very familiar with.
- Picture that space in vivid detail. For instance, if you chose your home, picture clearly all or a good number of its rooms.
- Imagine you’re walking in order, from your front door through your home.
- For each word, mentally place a visual item in order, as your journey progresses from start to finish. For instance, the password example I gave used Bugger as the first word. So a giant ant could be waiting for you on the front doorstep.
- Optimally, the password is already very memorable, so a mind palace will only reinforce things. But when laying out each word with a supporting visual cue, make sure to EXAGGERATE. This way, it stands out in your mind.
Password managers

Password managers store all of your passwords, effectively doing all the memorisation for you.
Once you generate your long (hopefully, at least 12 character-long) and random password, you can store it in your password manager vault.
These usually have some kind of MFA to double protect it password managers cannot be hacked fully without your private password key.
My personal favourite password manager is NordPass.
Closing thoughts 💡
Check if your email address has been compromised in the past.
Due diligence helps with security. So does using multi-factor authentication (MFA), which adds an extra layer of protection.
Authenticator smartphone apps are the most trustworthy, as some hackers are able to intercept phone MFA; have a look at Google’s Authenticator for Apple, and Android – Authy is another good example. Each is free.
But even if you’ve been diligent about keeping your computer safe, any website you’re registered with could get hacked. Attackers may then try to force their way into your account by forcing their way in using your username.
Passwords remain your first and last line of defence, so keep ‘em tight! The key is length and unique combinations. Other than that, you can mostly just have fun.
You Might Also Like:





