Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
VeraCrypt Review: A Superb Open-Source Disk Encryption Software
If you’re looking for an encryption solution and open source software is your thing, search no further.
If you have an itch to encrypt some data, VeraCrypt is an open source disk encryption software that just might provide the salve.
On top of being open source, it’s free and it gives you protection against any possible attack on your files.

Some of its primary features include:
- The ability to create a virtual encrypted disk inside of a file and then mount the virtual encrypted disk as if it were a real disk
- Encrypt a whole partition or a storage device, like a flash drive or a hard drive
- Pipelining and parallelization make it possible for data to be read and written with the same speed as if the drive were not encrypted
- The ability to encrypt a partition or a drive if Windows is installed
- Modern processors allow encryption to be hard wire accelerated
- Gives plausible deniability if you were forced to reveal your password. Hidden volumes and hidden operating systems provide additional protection
What does all this mean? Let’s dive in deeper and make it crystal clear.
What Does VeraCrypt Do for You?
VeraCrypt improves and enhances the security of the algorithms used when systems and partitions are encrypted. They are made virtually immune to new developments in the case of brute force attacks.
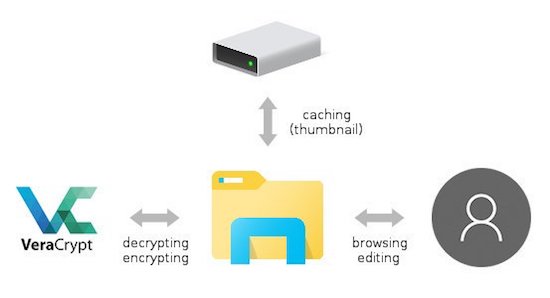
This is open-source, free encryption software. It can encrypt folders, files, and systems. It gives you extra protection against data theft and data leaks. It was created a way of addressing some of the security issues and vulnerabilities that were seen with TrueCrypt.
Other Features of VeraCrypt Include:
- Protection against Cold Boot Attacks
- No Backdoor Access
- Creates On-The-Fly Encryption Volumes
- Stops Data Leaks
- Prevents Data Theft
The ability to produce on-the-fly encryption volumes means that your data is encrypted automatically just prior to its being saved. And your data is decrypted instantly as it is loaded.
No additional intervention is required on your part.
No data that is stored inside of an encrypted volume can be decrypted or read if the user does not have the correct password, encryption keys, or key file. You can encrypt an entire filing system, including folder names, filenames, all of the content of each and every file, the metadata, free space, and more.
Why We Prefer VeraCrypt over the Competition
VeraCrypt and BitLocker compete with each other. We prefer VeraCrypt because it is open-source and easily accessible. With BitLocker, you need to be running Windows 10 Pro before you can even think about using the program.
Most people who go out and buy a new computer are going to get something that has a home version of Windows on it. VeraCrypt can easily be used and installed on Windows as well as a whole host of other operating systems.
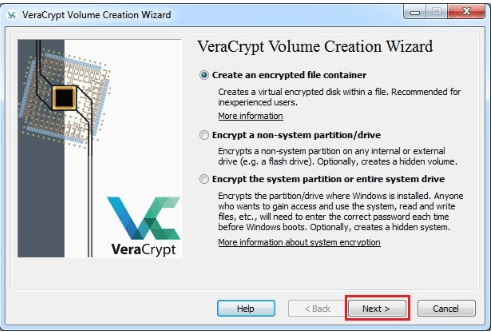
VeraCrypt is easy to use. You simply need to install the program and go through the setup process. Even non-tech savvy individuals can figure it out. It’s not a turnkey product.
By this we mean that in order to get the product to work, it is not simply a matter of toggling a checkbox. You’ll have to go to the process of creating a recovery disk in the event that everything goes bad.
VeraCrypt allows you to create a decoy operating system. If you are forced to decrypt, you only have to decrypt your operating system, but your data can stay encrypted. Basically, what we are getting at is that VeraCrypt is a powerful program.
To get the most out of it, you are going to need to be willing to really learn it and use it.
But once you understand just a few simple processes, you’ll be able to use it with little to no additional effort.
Benchmark
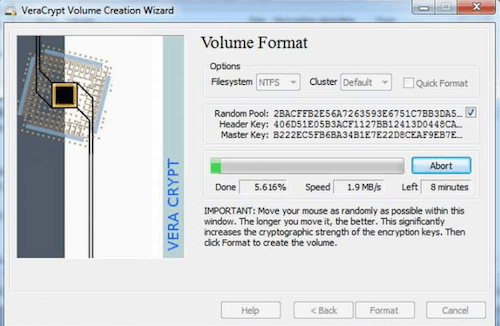
VeraCrypt comes equipped with a tool that allows you to benchmark the supported encryption algorithms. This way, you know which algorithms will provide you with the best performance.
You can select the supported encryption algorithm that you want when creating new containers or encrypting volumes on the system. We recommend that you select one of the fast algorithms as it will speed up the encryption process drastically.
VeraCrypt: A Product That Focuses on Security
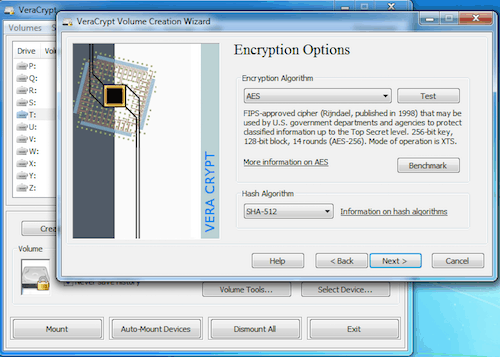
Encryption tools are only as good as the security they offer. VeraCrypt supports a number of encryption methods. It has strong security keys. One of the reasons for VeraCrypt’s strong security is that the same individuals who developed VeraCrypt also developed TrueCrypt.
There were some security issues with TrueCrypt. These security issues were addressed in VeraCrypt, making the product even more secure.
Of course, this does not mean that VeraCrypt is the perfect product. There are some concerns about malware and some physical access concerns.
And while we are pleased with the fact that the developers of VeraCrypt have done a lot to address issues that made TrueCrypt less secure than they wanted it to be, VeraCrypt still has some security issues that the developer will need to address.
The developers of VeraCrypt do not support TMP. This is because TMP has been compromised in the past. It’s not an easy feat, but it has been done. There are a number of good encryption programs out there. The fact is that VeraCrypt is stronger. It provides a seamless and transparent option for those interested in disk encryption.
The Power of Plausible Deniability
One of the most powerful benefits of VeraCrypt is that you have plausible deniability. In other words, you can deny knowledge of having sensitive information on your computer because there’s no way to prove that said sensitive information exists on your computer.
Of course, the individual or organization accusing you may assume that since you are encrypting your data, you are protecting something sensitive. But there’s no way to prove it.
VeraCrypt makes plausible deniability possible by allowing you to hide a single volume inside of another volume that’s invisible. VeraCrypt also allows you to create an encrypted OS.
There’s no way to prove that a hidden volume or a hidden operating system exists, therefore, plausible deniability.
A device that is encrypted using VeraCrypt or a partition that’s encrypted is going to have random data with no type of signature that would give an indication that the data it contains is not random. And it’s all but impossible to prove that an encrypted partition or an encrypted device is an encrypted VeraCrypt volume.
What Is a Hidden Operating System?
Creating a hidden operating system makes maintaining plausible deniability possible. As long as you follow the guidelines on creating the hidden operating system, the existence of the operating system should be impossible to prove. A great way to ensure plausible deniability when it comes to the hidden operating system is creating a decoy operating system.
VeraCrypt creates a boot loader that is stored on the VeraCrypt recovery disk or somewhere on the system, but it is not encrypted. So, obviously, if the boot loader is there, there must also be a system that’s been encrypted by VeraCrypt somewhere on the computer.
VeraCrypt helps you to get around this by allowing you to create a second encrypted operating system while you’re creating the real hidden operating system. The decoy system would not have any sensitive information on it. It’s not installed in a hidden volume, so existence is clear for everyone to see.
This way, if someone tries to force you to disclose the pre-boot authentication password, you can. All that you will expose is your decoy.
As a rule of thumb, if you’re going to create a decoy operating system, you need to use it frequently or else something might look suspicious. It’s a good idea to use your decoy operating system when you engage in activities that have nothing to do with sensitive data.
The last thing you want is for the individual trying to uncover your sensitive data to notice that your decoy operating system is barely used, which could cause them to become suspicious that there is some hidden system on the computer.

You can save your data on the decoy partition and not worry that your hidden volume is going to be damaged at all because the decoy system is not installed on the outer volume.
What this means is that your device is going to have two pre-boot authentication passwords that are completely separate. One will grant access to the decoy system, and the other one is for the operating system that is being hidden on your device.
This would also mean that you would have a third password for the outer volume. This is a regular VeraCrypt volume password that you could give to anybody without letting them know that a hidden volume or a hidden operating system exists. In total, you will have three passwords.
Two of them can be given to anyone without revealing the operating system that is used to protect your sensitive encrypted data.
Conclusion
VeraCrypt is a great privacy tool. It offers a high level of security, it is easy to use, and it is an open-source program, so it is free. VeraCrypt can be used for Windows, Mac OSx, and Linux.
With VeraCrypt, a single encrypted volume can be accessed simultaneously from multiple operating systems over a network. Still, on its own VeraCrypt does not provide the same protection you would get from the best VPNs around.
A top VPN will keep your company’s data or your personal data safe. A VPN will encrypt communication between servers. When your data is transferred, it is coded, so outsiders cannot read it.
Combining Veracrypt and NordVPN – Maximum Security + Anonymity
Your local device may be encrypted, but your internet traffic still isn’t. If you’re looking for the perfect pair, then we recommend NordVPN. NordVPN offers thousands of server locations in prime areas around the world.
They have a clear no logging policy and unparalleled customer support.
NordVPN is a user-friendly and simple software that reflects the company’s commitment protecting the privacy of their customers.
With this premier-level VPN, there are no hidden fees or clauses.

They do not try to upsell products, and you are able to use the service on as many as 6 devices with just one subscription.
A key feature of NordVPN is the proprietary technology they use to allow most of their servers get around geo-restrictions on services like Netflix. You can kiss geo blocking goodbye.
Because their jurisdiction is in Panama, you are protected from a number of the governmental surveillance programs that threaten to compromise your privacy.
- NordVPN has phenomenal customer support, offering a 24/7 live chat
- NordVPN has special servers that allow torrenting
- NordVPN’s plans range from $3.30 a month to $11.95 a month
NordVPN might be a little bit more expensive than some of the other VPNs on the market, but it’s important to remember that with VPNs, you get what you pay for.
Don’t waste your time or your money on subpar VPNs that at best and don’t work or at worst put your privacy and your security at risk.
You May Also Like:




