Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
PPTP vs L2TP/IPSec vs SSTP vs IKEv2/IPsec

Internet security has become an important topic in today’s world. Every time you go online, whether it’s from a computer or a smartphone, your personal information is at risk. Hackers are out there trying to steal data and you can’t even be sure which companies to trust.
If you want to get serious about protecting your privacy on the internet, then the best step you can take is investing in a good virtual private network (VPN) service for all of your devices. You’ve probably heard about VPN’s in the news but may be unsure of exactly how they work.
In this article, we’ll run through the benefits of using a VPN and dive into the various protocols being used today. Keep in mind that not all VPN’s are equal, and the protocol technology they choose to use is a big reason why.
Why You Should Use a VPN
The easiest way to understand a VPN’s function is to think of it as your own private tunnel on a busy highway.
When you use a normal internet connection, all traffic flows out of your home wifi network and to the open internet. Your internet service provider (ISP) is responsible for routing this data to the appropriate place.
When you turn on a VPN client, your traffic is first sent through a secure tunnel before reaching the open internet.
Data still travels through your ISP’s network, but it is fully encrypted so that hackers cannot intercept and decode it. In addition, VPN’s provide you with an anonymous IP address, which makes it even harder to track your online activity.
In general, it’s a smart idea to use a VPN when you connect to the internet. VPN clients are available for all operating systems and types of devices, including tablets and phones.
VPN’s are especially important if you travel a lot or rely on public wifi hotspots, as these are vulnerable to cyberattacks.
Overview of VPN Protocols
When you search online you’ll find hundreds of different options for VPN clients and services. So what exactly differentiates one from another?
It’s important to focus on the protocol technology that a VPN tool uses, as it will determine how secure and reliable the solution really is.
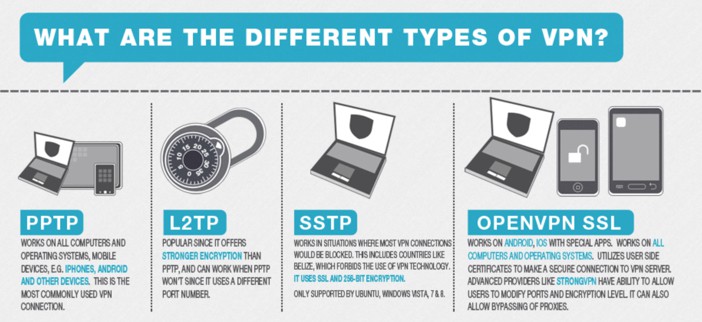
As VPN technology has evolved over time, new protocols have emerged while older ones have lost favor. VPN’s all aim to perform the same function of securing online traffic, but they do so through different methods of authentication and encryption.
Authentication is concerned with how you log in to a VPN client or service. Credentials are required to identify yourself and keep your data private. The encryption method of a VPN protocol handles the actual encoding of information so that no one else can steal and read it.
PPTP
The of the first network protocols invented for VPN services was called the Point to Point Tunneling Protocol (PPTP). In the early days of the internet, PPTP was the only VPN option available.
This was partially because it was designed by Microsoft and included in early versions of the Windows operating system. Both good free VPNs and also some of the more expensive counterparts in our list of the best Australian VPNs category use PPTP protocols.
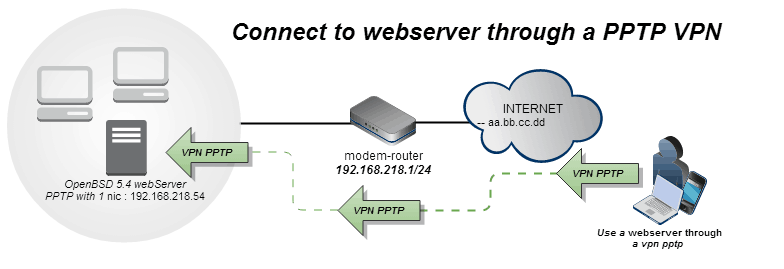
Traffic sent over PPTP uses port 1723 through the Transport Control Protocol (TCP). It supports a number of different authentication methods and will carry network requests through a tunnel that uses Generic Route Encapsulation (GRE), which is a protocol designed by Cisco.
Although PPTP has big companies behind it, the protocol has a number of security concerns that has led to a drop in popularity.
Some VPN services still offer it as an option because it is the easiest protocol to set up and configure, but the vulnerability in the PPTP encryption method means it cannot be trusted for day-to-day use.
L2TP/IPSec
After the first security flaws were found in PPTP, Cisco went back to their design process and helped create a strong protocol. L2TP/IPSec is actually comprised of two separate pieces: Layer Two Tunneling Protocol (L2TP) for routing and Internet Protocol Security (IPSec) for encryption.
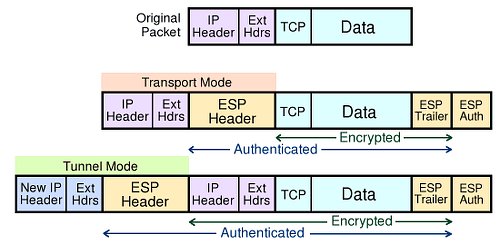
By shifting the VPN tunnel to Layer 2 of a network, which is known as the data link layer, Cisco made it harder for hackers to infiltrate the secure connection. In addition, IPSec added a 256-bit encryption key that offers enough security to have it be considered as top-secret compliant.
L2TP/IPSec is offered as a VPN solution on most modern operating systems, although in general it does take longer to configure.
In addition, sometimes network speeds with L2TP/IPSec can be slower than other VPN protocols. The added security of L2TP/IPSec still makes it a compelling option for internet users.
SSTP
Although VPN’s are now recommended for all types of devices, in the early days of the internet, they were primarily used by companies who needed a way to securely access systems from remote locations.
Because Microsoft had such dominance in the corporate world, they played a major role in the development and maintenance of different VPN protocols.
The Secure Socket Tunneling Protocol (SSTP) was a project run and owned completely by Microsoft. It uses TCP port 443 and functions in the same way as SSL certificates on the web, which are represented by the padlock symbol next to the URL address in your browser.
SSTP is considered to be a very secure protocol, but it is only available for Windows computers and comes with other limitations. It cannot handle all types of internet traffic and is primarily used to allow remote desktop users to connect to systems from external networks.
IKEv2/IPsec
As mentioned before, authentication is a critical piece of how all VPN’s operate. Each session you open on the secure tunnel will be assigned to your device and user information, so that web requests can be routed back and forth to your local network.

L2TP was the first authentication method to be paired with the IPSec encryption protocol. Nowadays, some VPN providers offer the option to enable Internet Key Exchange version 2 (IKEv2) as an alternative form of authentication. IKEv2 can be used with router-based VPNs or certificate-based services.
IKEv2/IPSec is considered to be a highly secure VPN protocol because of its reliability and security when negotiating a new tunnel session.
Unfortunately, some mobile devices may not have native support for it or are only able to be configured with an earlier version, known as IKEv1, which may be susceptible to cyberattacks.
If you read my article on the best Australian trading platforms, I recommend IPsec as the go to protocol for secure online transactions.
OpenVPN TCP
In the early 2000’s, the open-source development community began to look for a new alternative form of VPN protocol.
The result has come to be known as OpenVPN, which is currently available through a free or commercial license and can operate in one of two mechanisms: TCP or UDP.
The TCP version of OpenVPN routes traffic over the same channel as the PPTP protocol but does it in a much more secure manner. SSL is used during the authentication key exchange and then a custom encryption method secures the transfer of data.
A big piece of this is the OpenSSL library, which offers a range of ciphers and algorithms for encryption. OpenVPN TCP is a very flexible protocol, but because of that you need to be careful when choosing between providers.
Many companies are adding third-party plugins or scripts to run on top of OpenVPN TCP. These may add useful functionality, but they could also affect performance or even introduce new security concerns.
OpenVPN UDP
As mentioned earlier, the OpenVPN protocol is also supported by another mechanism. With the User Datagram Protocol (UDP) version, data is sent over a stateless channel that does not need to conduct a digital handshake between the message sender and the receiver.
TCP does include this handshake, which can take time but also guarantees that messages are delivered and acknowledged on both ends of the VPN.
The aim of OpenVPN UDP is to reduce latency as much as possible when connecting to the open internet. Because each request does not need to perform a separate handshake, the VPN layer can move packets of data faster without waiting for other network nodes to respond.
Most providers who use OpenVPN configure their clients to use the UDP option by default.
The UDP protocol is most often used in streaming audio, video, or gaming services when a certain amount of packet loss is expected and will not ruin the experience.
When it comes to OpenVPN, the UDP option does offer superior performance and speed, but reliability can suffer because your secure data may not always reach the intended destination.
SoftEther
SoftEther is another open-source project that markets itself as an alternative to OpenVPN and the other protocols maintained by Microsoft and Cisco. It is currently available for Mac and Windows computers, as well as servers running different builds of Linux.
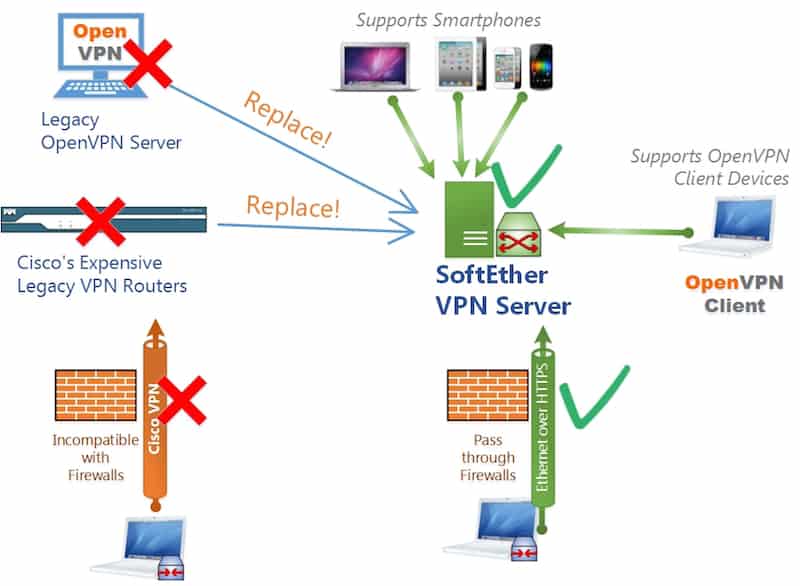
One of the big advantages of SoftEther is its compatibility with all of the other VPN protocols. It can operate alongside infrastructure that you already own while setting up a VPN environment for remote access or site-to-site tunneling.
SoftEther uses a custom form of encryption based on the SSL standard but is still able to integrate with most common firewalls and security blockers.
The SoftEther VPN includes a user interface for configuring the security settings and protocols, but it is more complex than the built-in options provided with most modern operating systems.
SoftEther works best in a cloud environment like Amazon Web Services or Microsoft Azure, where it can be deployed across an entire enterprise.
WireGuard
While many of the older VPN protocols have reached a level of maturity where new development is rare, the WireGuard protocol represents one of the newer options and is still undergoing heavy development today. The aim of WireGuard is to offer a simple, fast VPN solution for both individuals and organizations.
WireGuard began as a project intended to run on Linux, but it has now expanded to provide support for other operating systems and mobile devices.
When you install the WireGuard protocol, it actually adds a brand new interface to your network settings that is embedded at a low level of your device so that outside interference is minimal.
WireGuard is considered to a state-of-the-art VPN solution thanks to its approach to encryption. The tool uses something known as cryptokey routing to control a range of IP addresses that are allowed through the secure VPN tunnel. This relies on a network of peer nodes that communicate with one another through WireGuard.
WireGuard is committed to being an open-source VPN solution, but since the project has yet to release a stable version of their software, there is still some risk in using it as your only VPN tool.
The Bottom Line
In today’s word of data breaches and hacking, it’s more important than ever to take steps to ensure your online safety. A big part of staying private online is making sure your data flows through secure channels. Investing in a reliable VPN provider and tool is the best way to do that.
When trying to compare the different VPN solutions available on the market, make sure to research the technologies and protocols each one uses. As we’ve shown, some protocols are out-of-date while others are still maturing. You want to find a VPN tool that balances speed, reliability, and security.




