Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
VPN Tests and Checks – Here’s How to Do It

Every time you connect to the internet, you are taking on a certain amount of risk when it comes to data privacy.
Look no further than all of the breaches and hacks that get reported in the news, whether they are related to financial websites, social media networks, or malware scams.
So is there any way to stay truly safe and anonymous online? A strong virtual private network (VPN) solution is your best bet for achieving such a goal.
But before you run a Google search and download the first tool you find, be aware that not all VPN’s are created equal. In fact, many contain vulnerabilities of their own that can result in your private data being leaked to advertisers, government agencies, or cybercriminals.
Use the guide below to learn more about VPN’s, how leaks occur, and what you can do to test and check for them. For more info on our top VPNs for Australia check our homepage.
How VPN’s Work – A Quick Breakdown
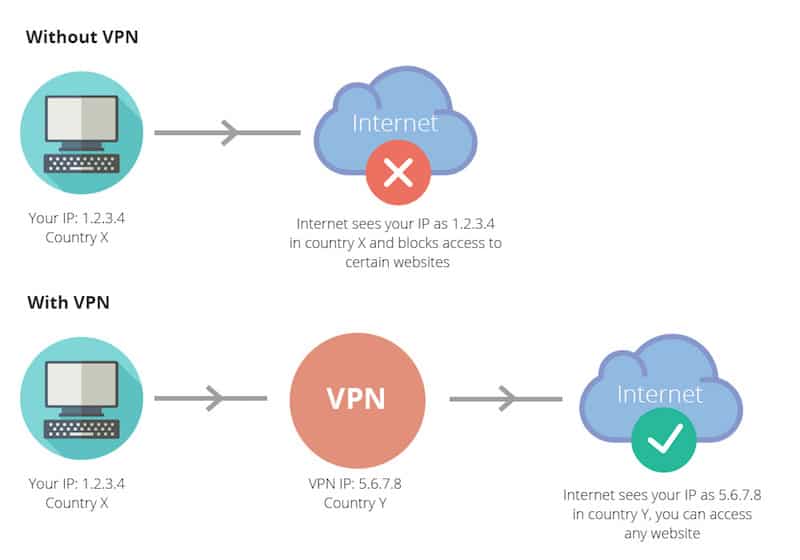
When you connect to the internet from your home or office, your computer or mobile device first talks to the ethernet or wireless router that is managing the local area network.
In most setups, the router then communicates with an internet service provider (ISP), which is the company who you pay for internet service.
The ISP’s infrastructure is responsible for moving network traffic onto the open internet, where it can be routed accordingly based on IP address.
For example, when you load a social media website, your browser sends a request through the ISP that will reach the website’s servers. An appropriate response is packaged together and shipped back to the ISP and then directed to your network, device, and browser.
With this configuration, your ISP has full knowledge of your online activity and can trace the requests you send. In addition, the IP address assigned to you by the ISP can be used by third-party companies to locate your geographical location. Learn how to hide your IP address.
A VPN adds a whole new dimension to this equation. They require two fundamental pieces: the client application and the endpoint server.
When you sign up for a VPN service, the provider will issue you a client application with instructions for installing it on computer or mobile devices. Each time you run the application, you’ll have to authenticate with a username and password exclusive to you.
The VPN client application opens a sort of digital tunnel that connects you straight to the endpoint server. You still use the bandwidth allotted by your ISP, but all of your web requests are encrypted and tagged with an IP address assigned by the VPN provider.
Once the VPN endpoint server receives your encrypted request, it decrypts the data and routes it to the open internet just like a normal ISP would. VPNs add a critical level of security, because even if a hacker manages to infiltrate your local network, any data they steal will be unreadable.
VPN Location – Why It Matters
There are thousands of VPN providers on the internet today.
Before you start sifting through each one, consider the geographical factor.
Transparent VPN providers will be open about where their endpoint servers are located on the globe, and this can be an important factor when thinking about VPN leaks and vulnerabilities.
In some cases, you may want to use a VPN that is based in your current country. Having the endpoints located nearby will offer high performance speeds and other benefits.
This is especially true in corporate environments, where companies require their remote employees to use a VPN session whenever accessing internal information and systems.
But depending on your needs, you may want to consider VPN solutions with endpoint servers located on other continents.
Keep in mind that IP addresses are grouped together based on geography, so when you receive a new address from your VPN provider, all websites will think you are located in that country or region.
Some VPN providers offer endpoint servers in multiple locations, allowing you to choose exactly where you want your IP address to be based.
Be aware that certain countries and territories actually ban the use of VPN clients because of the way they can hide information from government agencies. But there are still threats of purposeful leaks even in countries where VPN’s are fully legal.
For example, if a VPN provider is operating in a country with strict data tracking laws that require companies to make customer information available to government agencies, then there is a chance your internet traffic could be logged and exposed.
Because VPN providers have the ability to decrypt all of the requests that enter the endpoint server, their systems must comply with the regulations of their country.
Activity Tracking – What You Don’t Want
As mentioned before, the primary responsibility of a VPN endpoint server is to take an incoming web request, decrypt it, and then route it to the appropriate place on the open internet.
This transaction is meant to be anonymous, but in reality, it all depends on the trustworthiness of the VPN provider you use.
When you first sign up for a VPN service, the provider collects your name, email address, and potentially other personal information.
There is nothing to stop them from connecting that data to the activity that they monitor on their endpoint server. Advertisers and other third-parties would be eager to obtain that type of data for a variety of reasons, not all of them legal.
The best rule to follow is to be wary of any VPN provider offering a completely free service. Those services typically offer poor performance with potential security implications.
If you are not paying a monthly or yearly fee for your VPN client, there is a good chance your web activity is being tracked or shared without your direct consent.
However, this is not always the case. Check out our list of the best (and worst) free VPNs for Aussies to distinguish between them.
Logging Tracking

Some VPN providers will issue promises that they do not monitor user activity or sell their data to third-parties.
However, there is a related type of tracking related to logs that can also represent a data leak.
So before you invest in any VPN tool, make sure to fully research the provider’s logging policy.
In many cases, logging is necessary for a VPN company’s operations. This is especially true if the provider places bandwidth caps on individual users. In that case, the company will need to keep logs of how long you are connected and how much data you use.
If security and anonymity are top priorities for you, then you should look for a VPN solution that offers unlimited bandwidth and a zero logging policy. With that type of client, you can be assured that none of your activity can be tracked by your ISP or the VPN provider.
IP Address Leaks – Don’t Let Them Know Where You Are
The most common form of VPN vulnerability is an IP address leak, which occurs when an outside website or service is able to detect the true IP address assigned by your ISP even when you are connected to the VPN client.
This allows third-parties to detect your true location and potentially execute a cyberattack.
To start investigating a potential IP address leak, open a web browser before connecting to your VPN and navigate to whatismyipaddress.com. This site will display the IP address assigned by your ISP.
Then launch your VPN client and reload the webpage to check your new IP address. This is the one that all websites will see while you have an open VPN session.
How a VPN Can Fail at Masking Your IP Address
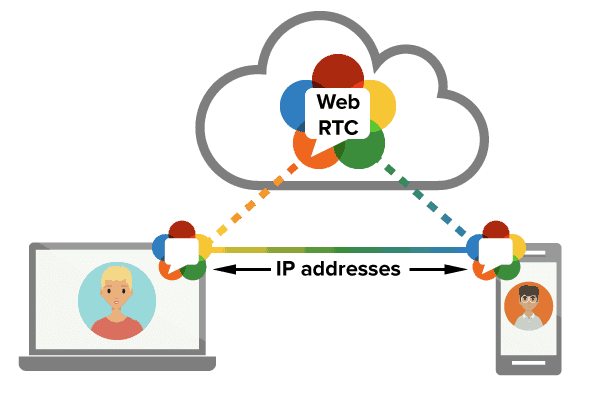
Due to a service known as Web Real-Time Communication (WebRTC), many VPN clients are at risk of revealing their users’ local IP address.
WebRTC is used by a lot of popular applications and websites in order to update live content on a webpage, such as a social media site or email inbox.
Because of the way that data is transmitted between your browser and sites that use WebRTC, certain VPN clients fail to disguise the source IP address.
As an initial check, the whatismyipaddress.com site has a WebRTC leak test that will show you how your browser is transmitting your IP address. If the test can detect the IP address assigned by your ISP, then it means your VPN or web browser is leaking that information.
Certain premium VPN providers will offer an assurance that their products are not vulnerable to WebRTC leaks. If your client is affected, there are actions you can take.
WebRTC leaks occur at the browser level, but Mozilla Firefox is the only application that allows you to block WebRTC transmissions entirely. This can be done through the about:config page.
For Google Chrome users, you will need to install a browser plugin like WebRTC Leak Prevent. This tool can control certain hidden privacy settings within Chrome and block any attempts of third parties who try to obtain your ISP-based IP address.
DNS Leaks – Like Leaking Your IP
The open internet relies on a protocol known as the domain name system (DNS). It functions as a global database that tracks what IP addresses are linked to what website URLs.
This way, when you type in a .com or .net address into a web browser, your ISP knows exactly where to route your traffic.
DNS servers are located all across the globe. Typically, your ISP will operate their own set of DNS servers to keep traffic moving as quickly as possible. When connecting to a VPN service, a different DNS server should be assigned, although this is not always the case.
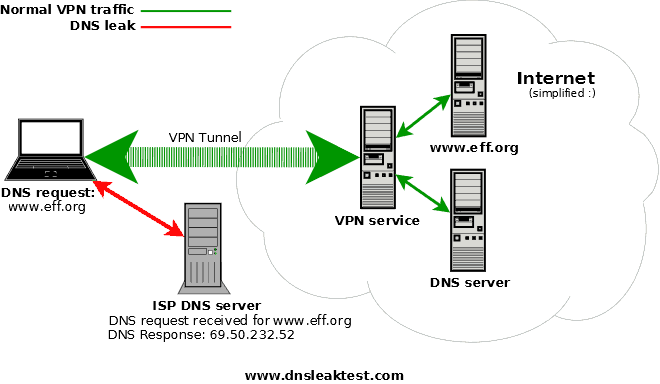
To check for a potential DNS leak with your VPN client, go to dnsleaktest.com and click on the “Standard Test” button. The site will run a series of checks to see how your device is obtaining DNS information.
At the end of the test, the page will attempt to identify your ISP and geographical location. If this is correct, then it means your VPN has a DNS leak.
Fortunately, you can take action on a DNS leak right away. The easiest solution is to override both your ISP and VPN settings and use a set of manual DNS addresses instead. OpenDNS and GoogleDNS both offer free services that anyone across the globe is able to use.
To adjust your DNS servers, open your device’s network settings and look for the manual DNS option. To use OpenDNS, enter 208.67.222.222 and 208.67.222.220 as the primary and secondary addresses.
For GoogleDNS, use 8.8.8.8 and 8.8.4.4. Once saved, your device will use these DNS servers for URL information and bypass your ISP and VPN completely. Here’s a video explaining how to do it.
Reviews You Can Trust

VPN companies need to come up with creative ways to advertise their product and attract new customers. As a result, you’ll find that nearly every provider claims to offer the most security and protection.
Obviously this can’t be the case, which means you can’t always trust the marketing information they display.
Instead, rely on reputable reviews from sites like Privacy Australia, who have run their own tests and studies to determine how secure VPN clients really are.
At the end of the day, you’ll need to decide what you value most from a VPN client: price, performance, and security. Check our Mission page or our Testing Policy to learn more about how we test.
Other Security Measures
If you are still concerned about the security of your VPN client or simply want to add other protection, there are steps you can take on your device or browser to ensure that you are truly anonymous online.
First, enable incognito or privacy mode on browsers like Chrome and Firefox, as this will prevent outside companies from storing cookies on your computer and tracking your activity.
For additional privacy, consider installing the TOR browser on your device, which routes all of your web traffic through a secure network to disguise your identity.
Lastly, don’t forget that your online security is directly tied to the network you are using. If you often connect to public wi-fi networks, you will routinely be at risk for security breaches or cyberattacks.
If you absolutely need to do so, then make sure that you have a good VPN client installed on your device from reputable providers like NordVPN or Surfshark to ensure your information is always safe.
Happy Trails!
You May Also Like:



