Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
8 Things to Avoid When Buying a VPN Service
Staying safe online is harder than ever before. Managing to keep your computer safe from viruses and malware is one thing, keeping your online activity private and anonymous is another.
Many websites today track your online activity for many reasons; better product recommendations, targeted ads, even recommended news articles to read. These details are generally not shared with other companies. However, not everyone has good intentions.
The dangers come when your personal information gets used for malicious purposes.
- Your contact information sold to advertisers for unsolicited phone calls, non-stop messages and spam emails.
- Your personal information used by cybercriminals to extort you.
- Your personal data being used by criminal organizations to create a more targeted phishing scam. Making you more vulnerable to believing its authenticity.
While technology experts all agree that the best action you can take to preserve your online privacy is to reliable virtual private network (VPN) solution. The question is, how do you find the right VPN provider to use, especially when there are so many options available online?
Research is important because as the VPN industry has grown, many scams have popped up in an effort to steal money or information from unsuspecting consumers.
To protect yourself from these VPN scams, review the list we have made of the types of scams to look out for. If you want the research already done for you, check out our reviews of some of the best VPNs that steer clear of these practices.
VPN Basics – How It Works
Before diving into the most common VPN scams you’ll encounter, it’s important to know the fundamentals of how VPN’s work.
Companies that offer VPN services must maintain secure servers in a local environment or data center. These are known as endpoint servers. In addition, VPN providers must make a client tool available to its customers for installation on computers, smartphones, and other devices.
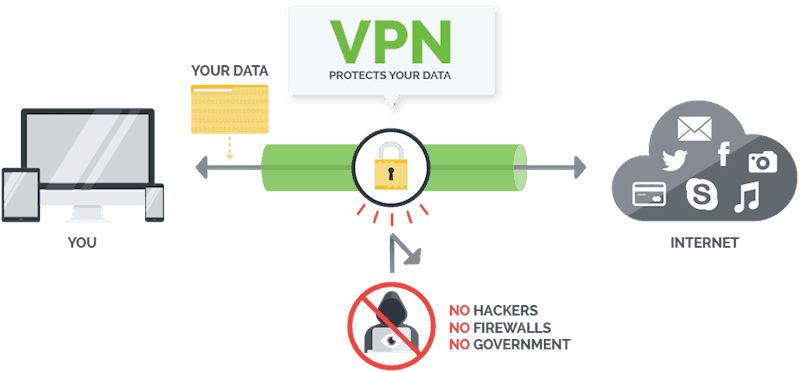
VPN sessions are initiated through the client tool, typically with authentication by username and password. At which point, a secure tunnel is formed between the user’s device and the endpoint server.
Your web traffic will still be passed through your internet service provider, but all data is encrypted to make it difficult to intercept. Once the data is received by the endpoint server, it is decrypted and routed to the appropriate destination.
That’s how it works. Now that you have a basic understanding of VPN’s, let’s jump right to the specifics of what you want to avoid.
Poor Performance – Slowing Client Speed

Relying on a VPN tool adds another step in all of your web transactions.
So each time you load a new webpage, your traffic has to hit the VPN provider’s endpoint server before it can finish the request.
As a result, there is a chance that using a VPN could result in slower load times in your browser.
However, reliable VPN companies work to minimize this effect as much as possible through a number of means, including the management of multiple endpoint servers split across different regions.
But some providers will look to cut costs and operate their service with underperforming hardware.
You should run network speed tests through a tool like SpeedTest.Net on a regular basis, as VPN performance may vary based on factors like time of day. Try running one test when connected to just your ISP and then compare the results to a second test with your VPN service enabled.
If the VPN test has significantly slower results, it could mean your provider is throttling your usage or speed.
Rotating Endpoint Servers – Avoiding Jurisdiction
In addition to offering security protection, VPN solutions come with the added advantage of assigning your device an IP address based on the endpoint server the provider is using.
As a result, your identity online essentially becomes anonymous and is hard to track geographically.
Clever internet users have found that by using a VPN service with endpoint servers in a specific location or country, they can actually get around certain geographic restrictions for video or app services.
However, this often constitutes as a breach in terms of service and can trap you in a VPN scam.
For certain VPN providers, when you launch their client tool you will be prompted to choose from a list of endpoint servers in many different locations. The ability to choose may seem like a big advantage, but you should be suspicious if you notice these addresses are changing on a regular basis.
If a VPN company needs to rotate their endpoint servers all the time, it often means that they are trying to avoid legal regulations. In fact, VPN services are blocked or restricted in many countries.
For the best security and performance, look for a VPN solution that has a stable set of endpoint servers.
Missing SSL Certificate – Lack Of Encryption
While browsing the internet, you are likely to see advertisements for different VPN providers.
Clicking on one of these ads should bring you to the company’s homepage, where you can learn more about their service and what payment options they support.
To create a new account, you usually only need to choose a username, password, and payment plan.
But before you rush to sign up for a VPN service, take a minute to fully examine the homepage of the provider.
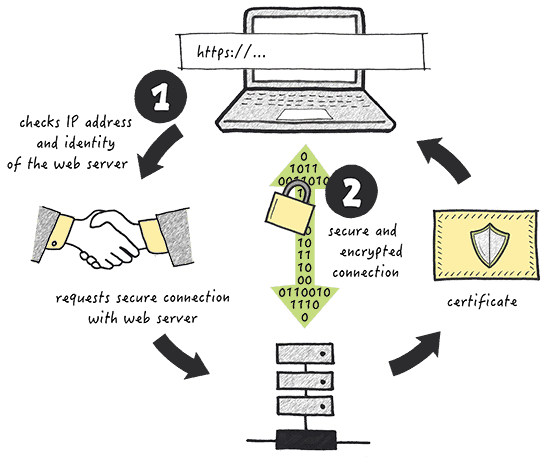
Specifically, check the top of your browser window for the address bar where the site’s URL is displayed. To the left of the address should be a padlock icon to indicate that the website has a valid secure sockets layer (SSL) certificate.
SSL adds a critical layer of protection between your web browser and the sites that you visit. The certificate tracks a public and private key, which are used to encrypt data transmission over the open internet.
As a result, even if a hacker manages to intercept your web traffic, they won’t be able to decrypt the contents and steal your information.
If a VPN provider’s homepage is lacking an SSL certificate or has one that is out of date, you should aim to avoid it at all costs.
It could be an indication that the service is actually a scam, because if you enter credit card information over the non-secure connection, your financial data is at risk of being stolen.
Installer Vulnerabilities – Local Device Security
In the early days of the internet, VPN services were available only for desktop computers and had to be configured through the operating system’s network settings.
Things are very different nowadays, especially because so many customers rely on VPN connections from their smartphones, tablets, and other mobile devices.
To be able to support so many different pieces of hardware, VPN companies have an incentive to build and distribute their own tools for installation.
When you first sign up for a VPN account, you’ll typically be redirected to an installation page that will start a download to your local hard drive.
Any sort of download from the open internet carries a certain level of risk, and that’s especially true for VPN installers, as they can be coming from unfamiliar organizations or countries. If you are not prepared, the VPN application could actually spawn a virus or malware on your computer.
Before installing any VPN tool, make sure you have a virus scanning tool on your computer that is fully up to date. If issues are detected during installation, you need to immediately delete all related files from your hard drive as quickly as possible.
One of the latest trends related to VPN scams is cryptojacking, where a rogue installer actually hijacks part of your operating system and runs a cryptocurrency mining bot in the background. This can damage your hardware and leave your computer vulnerable to other types of attacks.
Phishing Attacks – Impersonation
After signing up for an account with a VPN provider, you should only receive emails from them regarding new features and billing updates. If you suddenly start getting an influx of suspicious-looking messages in your inbox, it could be an indication that your email address has been shared with cybercriminals.
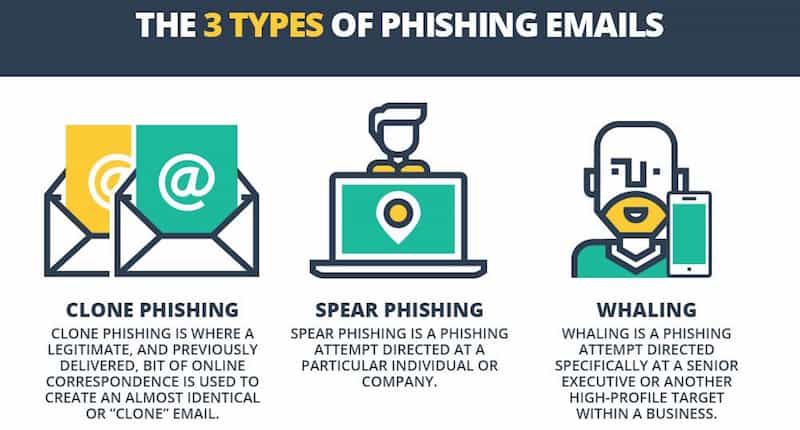
Phishing scams are one of the most common forms of hacking. It usually begins with an email message that claims to be connected to your VPN provider or another technology company.
The email will suggest that there is a problem with your account and urge you to click on a link to fix the problem.
When you click on a link from within a phishing email, your browser will typically be directed to a malicious URL that was disguised in the message.
If you enter your VPN credentials or billing information into the fake webpage, you could expose private information to the attackers. In other cases, the phishing page may launch an installation program that can hijack your device.
Pricing Tricks – Your Data As The Product

Running a VPN company is a costly endeavor.
The provider needs to maintain a collection of endpoint servers, often across multiple data centers, as well as developing the client tool for a variety of operating systems and devices.
To add to that, VPN companies are expected to offer customer support and other basic services.
For those reasons, you should expect to have to pay a monthly or yearly fee in order to maintain full access to a reputable VPN service.
The cost of VPN services may vary based on a number of factors. Specifically, you may be able to save on VPN solutions that have a cap on the amount of bandwidth you can use. If you only expect to use the VPN on rare occasions, then this may be a smart option for you.
You are bound to stumble upon certain VPN providers who claim to offer their service for free. Unfortunately, we all know that nothing is free.
These deals are often too good to be true and may potentially be a business front for a larger scam. Do plenty of research before downloading and installing a free VPN client on your device.
Free VPN services typically have poor performance and security vulnerabilities. In many cases, the company will harvest your data and use that to make money.
The worst case scenario is that a VPN provider could sell your password and other personal information to cybercriminals who can carry out dangerous attacks.
Trying a reputable VPN solution that offers a free trial is a much safer option, although there can be scams involved there as well.
Free trials will typically expire after one week or one month, but before you can begin one, you’ll need to enter credit card information.
Most companies will set your account to start billing right when the trial ends, and figuring out how to cancel your trial can be cumbersome.
You should also research a company’s price change policy, because if you sign up for a month-to-month plan, there is a chance the cost could fluctuate without your knowledge.
Logging Policies – Online Traffic Data Sharing
When evaluating different VPN solutions and looking for potential scams, you should focus on the logging policies that companies have in place.
Because all VPN traffic flows through the provider’s endpoint servers, the company technically has the ability to monitor and track your internet activity.
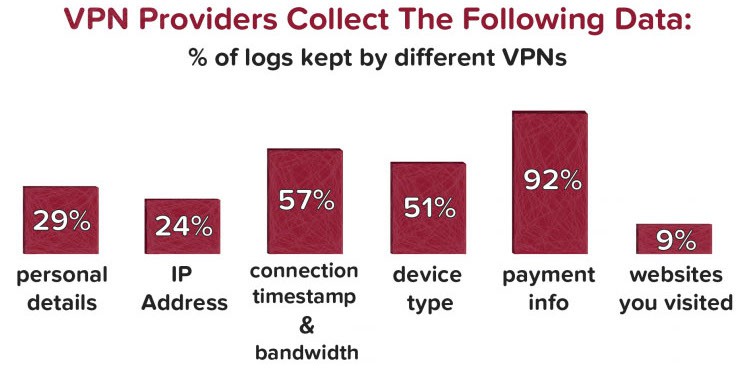
For companies that maintain bandwidth limits for their VPN customers, certain logging mechanisms are required in order to track that usage.
But in order to fully trust the VPN company, that data should be kept as anonymous as possible so that your name and email address are not being collected on a regular basis.
The risk with logging is that the company could potentially share the data it stores with outside parties, like advertisers, who are interested in monitoring online activity.
This can represent a breach of your privacy, especially since most people invest in VPNs for the purpose of being anonymous online.
The most trustworthy VPN providers outline their full logging policy on their homepage.
If you are considering downloading a new VPN client but can’t find the company’s logging policy, there is a good chance that your activity will be tracked.
Customer Service – Lack of Real-time Support

VPN companies are often small operations with a minimal staff. This can make it a challenge to get in contact with a real person when you have a question or issue to discuss.
Some customers can feel scammed if they cannot communicate with the VPN provider regarding their account.
When researching VPN options, look for providers who publish a customer service phone number in addition to an email address.
If a company is only accessible over email, it can pose issues for getting account support. You want to be able to quickly report problems to a company, such as billing errors or connectivity issues.
The Bottom Line
If it seems to you that the VPN industry is something like the Wild West, you’re partially right.
There are plenty of scammers looking to take advantage of the gullible and the ignorant. But because you’ve educated yourself with this article today, that’s not going to be you.
In the vast ocean of scum and villainy, the good news is that there are still plenty of credible service providers floating around, just like NordVPN and Surfshark.
You just need to do your research and you will find the best among them. As long as you always remain informed and vigilant, you will never be a victim.
Now get out there and find yourself the right VPN!
You May Also Like:



