Disclosure: Privacy Australia is community-supported. We may earn a commission when you buy a VPN through one of our links. Learn more.
Best Free Online Virus Scanners

You’ll usually be looking at trial versions of paid software when using free online virus scanners.
This usually means fewer features than its fully paid-for counterpart.
Still, on-demand scanners can still help you stay ahead of the worst threats by spotting acute problems.
Malwarebytes is one great example.
Top Free Online Virus Scanners in 2024
Avoid choosing just any online malware scanner. You could be ironically using something designed by a cybercriminal, luring you into a phishing scam, you should avoid becoming just another identity theft statistic.
- Pair with a budget-friendly antivirus for the best protection
- Add a cheap VPN for online banking/public wifi.
The list:
#1 Kaspersky
Key Features:
- Clear Scanning Results
- Supports URLs and Files
- Very Simple Website
- Online Payment Protection
- Network Firewall Two-ways
- Fast Scans and Anti-phishing

Pros
- High reputation
- Stellar security
- Low resources needed
Cons
- Only one file scan at a time
- No browser integration
Kaspersky Top Free Online Virus Scanners Review?
Kaspersky may not be at the top of every review list but based on sheer rigour without sacrificing performance, it’s some wonder.
We think it’s the go-to solution if you need something fast, simple and good enough. We might not agree that Norton and McAfee are its two biggest competitors, but our tests have shown KL to be adequate.
On rumours to do with links to Russia, we’ve seen no evidence that Kaspersky Labs are culpable. These guys continue to be favoured by independent labs tests.
How Good is Kaspersky Free Antivirus?
We’ve put Kaspersky above Bitdefender but it’s really a toss up here for the best free online virus scanner and remover. There’s no fancy frills with the free version. But you will have a world-class friend in the struggle against cyber risks – which even includes anti-phishing.
#2 Bitdefender
Key Features:
- Critical Locations Scanning
- Custom Files/Folders Scanning
- Full/ Deep System Scan
- Very Simple Mac Scanner/Remover
- Eliminates Pop-ups and Slowdowns
- High-Performing

Pros
- Strong reputation
- 30 mins deep scan
- High rated engine
Cons
- Great cheap mac scanners available
Bitdefender Top Free Online Virus Scanners Review?
Bitdefender, like Kaspersky, claims to have the highest-rated scores for the ability to detect and remove viruses. In fact, they’ve produced the highest anti-phishing scores around.
We’ve at least found this tool to be very solid. In our books – as long as you don’t expect to have some of the more useful features that Bitdefender offers in its paid version – this is a no-frills essential defence solution.
The best free online virus scan for Mac. Ward away the most likely mischievous gremlins when online, and this also works on Windows.
How Secure is Bitdefender?
Have a quick peep:
That’s the best case scenario. Independent tests seem to suggest that it’s a great, free online malware removal tool.
You’ll also be getting anti-fraud and anti-phishing safeguards. Just don’t expect peace of mind if you want to do online banking.
#3 Norton
Key Features:
- Updates On Opening
- Scans Unwanted Applications
- Do Deep System Scans
- Do Reputation Scans (Folder/Files)
- Requires Low Resources
- Rootkit Scanning

Pros
- Highly reputable
- Trusted engine
- Handles essentials
Cons
- Gives false positives
Norton Top Free Online Virus Scanners Review?
Do we need to tell you about Norton? The most well-known antivirus scanning system in the market has proven itself to have a rugged engine. Be aware that they are a little aggressive, and so tend to give false positives.
Keep an eye on the software quarantining programs, files and folders that are important to your work or the running of your system. The demand on system resources is also low. Actually, they’ve been shown to have one of the smallest effects on system performance.
How Secure is Norton Antivirus? ⚔️
If you’re wondering are there websites that can remove viruses from your computer – the answer is no. Computers require software to be downloaded first so that permission can be given to delete or quarantine files from the hard drive.
Norton gets top marks for making its scanner downloadable. Just download the Power Eraser and it will be able to both identify and remove malware. Provides quality online virus scans for Mac and Windows.
#4 Trend Micro
Key Features:
- Gives You Online Protection
- Protects Against Ransomware
- Anti-Phishing Protections
- Online Banking Companion
- Scans In Real Time
- Uses Machine Learning

Pros
- Super simple interface
- Micro Pay Guard
- Free for mobiles
Cons
- Lesser known
- Only free for mobile
Trend Micro Top Free Online Virus Scanners Review?
We wanted to add a great option for protecting mobiles, be it iOS or Android. Trend Micro gives you a simple solution in either case. This link will take you into the download page for both operating systems.
Scanning is in real time. Trend Micro can identify and repair, including providing ransomware protection. The user interface is extremely simple.
How Safe is Trend Micro?
Independent testing companies think Trend Micro has a strong antivirus engine. Better to have this nothing at all for online banking on your phone. In that regard, a very useful free online malware removal tool here.
#5 ESET
Key Features:
- One-Time Scan
- Free to Use
- Identifies and Removes Malware
- Gains Permissions
- Downloads to System
- Quarantines Infected Files

Pros
- Three scanning levels
- Set to monthly scan schedule
- Custom scans
Cons
- Limited to monthly schedule
- No real-time scanning
ESET Top Free Online Virus Scanners Review?
ESET is well-known for being very configurable. Don’t expect that on the free online scanner. It’s a no-frills option for identifying and eliminating any malware threats on your computer for free.
If you’re willing to forego real-time, continuous protection – and think monthly scans of your applications and files for any suspicious activity is good enough – this is a very simple option needing no registration or financial commitment.
How Good is ESET Antivirus?
ESET has had questionable results by independent testers. But what we like about them is it’s a one-time solution. In other words, you won’t have this slopping your system resources in the background.
This is particularly useful as a second opinion if you already have a full, paid piece of antivirus software. Note, there’s no online banking protection or defences against hacking. Best to keep that in mind.
Buying Guide
Is Free Antivirus Enough?

When you download a top performing free online virus scanner, the devices are checked for any source codes that are flagged in its definitions database (stored on the cloud).
This database is constantly updated, keeping on top of the latest threats.
There will be extra protective measures that you will be missing out on, however.
For instance, anti-phishing safeguards, ways to do online banking without worrying in a secure browser – and other extras such as better customer support.
But overall, you will get protection against the bulk of threats from a top-tier free online virus scanner and remover. Any strings of code that are known to be viable will be automatically removed or quarantined.
Is Cybercrime Growing?
The pandemic was an example of how crime is moving online. With more people spending more time online, cyber criminals targeted surfers.
For instance, fake COVID treatment articles and products.
In a testament to how this type of crime attracts people who love to disrupt networks, there was a spike in the number of medical centres, hospitals and research laboratories targeted by cyber terrorists. System networks were overwhelmed, and attempts were made to access sensitive information.
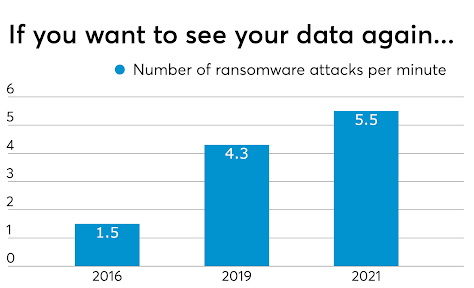
Every industry has been impacted. Even accountants are being briefed in ways to keep up with emerging threats and maintain customer confidence in the face of cyber risks.
The truth is that these bigger companies face overwhelming threats. They may eventually fall prey to one.
As an individual, member of a family household, or small to medium-sized business – regular automated checks from a top-performing provider is an essential.
This is a race. Cybercriminals have access to high-level equipment. They have access to quality analysis research. And use special penetration tools to test ahead of time whether particular malware designs will be detected by their target.
How Do Online Scanners Work & How Does Antivirus Quarantine Work?
A quarantine is the isolation, removal or deletion of an infected file from its original location. Edits also made to how the file works, limiting or disabling it from being able to run its executables. A great free online virus scan and removal tool will know what files to target, based on its continuously updated definitions database.
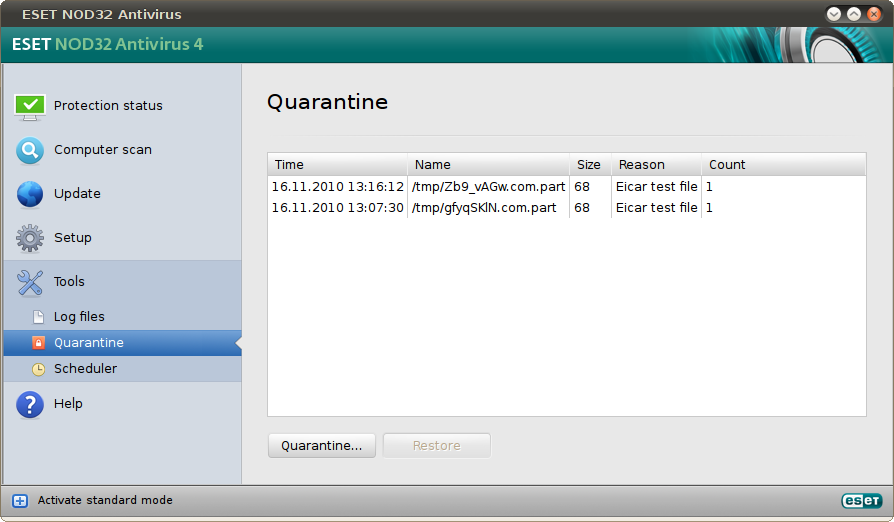
After the infected file is removed from its location and immobilised, it’s placed into a hidden folder that no other executable can influence. Even you won’t be able to access that file.
The infected file will stay there until you’re taken to the quarantine screen. Here, you need to make a choice on what to do next with the file. In a few cases, you may find that your online scanner cannot detect an infected file. Some scanners allow you to manually quarantine instead.
Are Quarantined Viruses Actually Removed?
Actually, infected files will steal your computer unless you decide otherwise. If you choose to, you can permanently remove them.
Otherwise, quarantined files will stay in a hidden folder on your hard drive. No need to worry however, the file will remain disabled. And you can delete it manually at a later date.
One caveat is that this sucks up hard drive space. So best practices are to regularly remove quarantined files completely. In the unlikely event that important program files are quarantined – files needed for your computer to run effectively – you should have the option to clean rather than delete. This targets only malicious codes inside the file.
The Simplest Way to Protect Your Computer & Identity
#1 VPNs
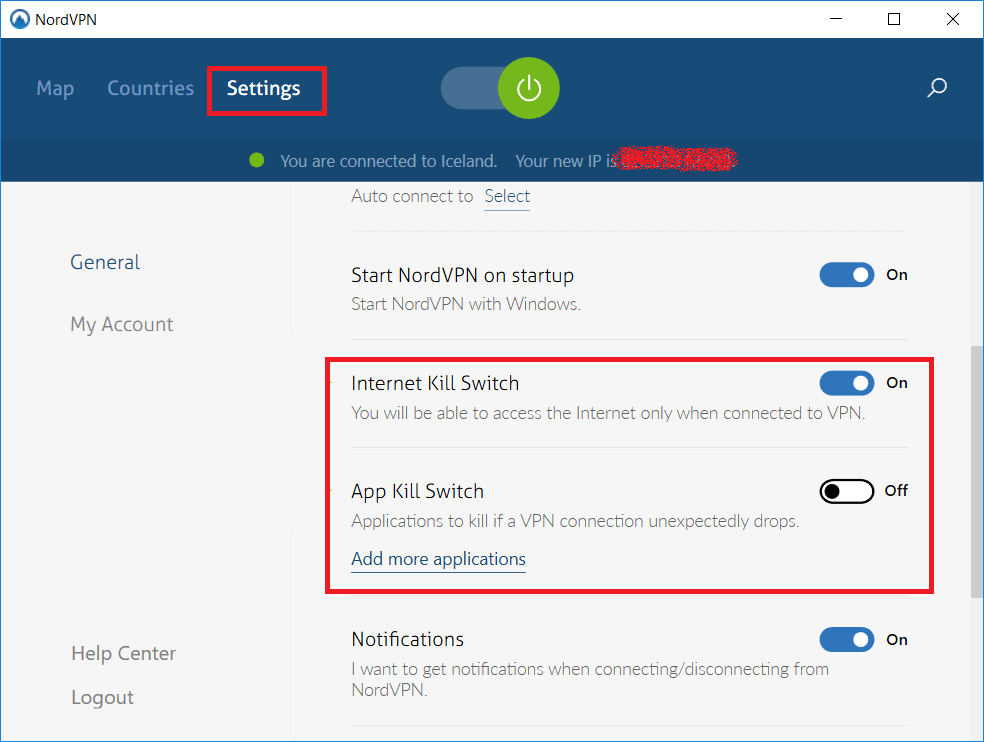
A VPN encrypts traffic flowing between networks and your devices.
When online, even ISPs will have radically less information about users with VPNs.
Sure, they’ll know someone’s online using a VPN – but not IP addresses or identities.
You can let a VPN run in the background. Don’t choose just any provider, however.
Go for a reputable VPN in 2024 with anti-leak protection (be warned that many free VPNs actually install malware onto your system).
A quality VPN will also have a ‘kill switch’, which automatically cuts your internet if there’s a break in the encrypted connection.
This means you’ll never be online without protection!
There are free VPN extensions for browsers. And as additions in antivirus software like Norton…
However, they tend to be slow but getting a professional VPN service like Nord VPN will get you the best speed possible.
We would also place getting the best secure browser in this category, as the safest – such as Tor browser – automatically anonymizes your web traffic. The Onion Router, therefore, protects your online identity, making it more difficult for people to take advantage of you for example when doing online banking. Keep in mind that some of the safest browsers can be sluggish.
#2 Dedicated Devices
One of the oldest tricks in the book for good risk management is to have a secondary machine that you use only for your most sensitive data. For instance, business data. If you are handling cryptocurrency or account information, tax data and so on, this machine can be your go-to referral point – one that you never connect to the Internet.
#3 Frequent Scans
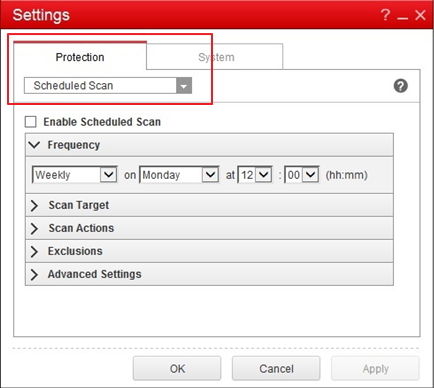
Takes only a one-time action. The rest is automated by the scanner.
This is one of the advantages of having a solution that sits on your machine…
Schedule the online scanner to run a full system scan weekly.
As almost all of us are actively online, this increases the chances that any new undetected threat doesn’t stay on your system for long.
Get it quarantined and cleaned.
And do it as soon as possible.
#4 Stick to Safe Sites
The most obvious sign that a website is potentially dangerous is if the URL bar does not show a secured lock symbol.
But you should also avoid sites that offer, for free, products that should otherwise be paid for – such as “free movie streaming” websites.
These are high-risk sources for online viruses, even if you do not download files and just stream
FAQ
What Are the Most Common Cyber Attacks?
Cyberattacks target networks, computer systems or personal devices with the intent to steal or alter information:
#1 Phishing Attacks

Phishing explained: – Phishing attacks are emails that pretend to be from trusted sources. Like a fish on a hook, the cyber attacker hopes to lure you into taking a specific action. Perhaps you download an attachment or click a link that eventually infects your computer.
Spear phishing explained: – This variety uses research about a specific target in order to tailor-make convincing messages. This type is much more difficult to defend against or identify.
The ‘From’ section of the email and subject line may be spoofed in order to convince you it’s coming from a provider you are in business with. Websites may be cloned. The intention is to trap you into disclosing personal information such as logins:
- ☑️ Be wary – do not hastily go through your inbox, but become accustomed to auditing messages
- ☑️ Do link hovering – but don’t actually click the link, so that you can see where it will direct you
- ☑️ Use sandboxing tools – so you can check links and suspicious emails without risking your machine
- ☑️ Analyze headers – the reply-to and return paths should match
#2 DDoS/Dos (Denial-of-service/distributed denial-of-service)
These attack types debilitate computer systems by overwhelming its resources. Both types do the same thing – crushing a network’s ability to answer service request demands – but they do this at different scales. DDoS attacks also spread malware.
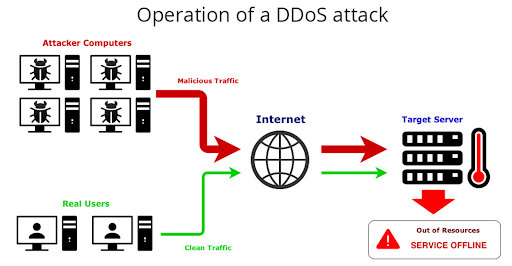
In DDoS attacks, cyberattacks control the malware, which can involve millions of inter-connected infected systems.
Unlike phishing attacks, the cybercriminal does not gain access to your system. Instead, it cripples the target. This can be a means of aggressively competing against other business competitors, by crippling their system resources. There are several types of DDoS and DoS attacks, including teardrop, PCP SYN flood, botnet, ping of death and smurf.
#3 Man-in-the-Middle & General Malware
Man in the middle – abbreviated as M ITM – attacks are what they sound like. Server and client believe they are talking to each other but there is a hacker who has inserted himself between them. This lets the attacker can steal data or insert data into the conversation, making it seem as though there has been no interference.
While general malware is any type of malicious code – embedded into software or files – that influences your device without you approving it. Oftentimes, it infects trustworthy files and programs, distributing yourself secretly. This includes worms, ransomware, spyware and adware, stealth viruses, polymorphic viruses, and many more.
Some of the strongest free online virus scan and removal tools provide protection for advanced malware forms like ransomware.
Conclusion
Using an online virus scanner is like getting a second opinion from a doctor. It’s hasslefree, no-frills. There’s no need to install bulky software. You won’t need to register – and it’s generally very fast to set up.
If there’s something you are asking yourselves – did you get hacked?, quickly test with a few choices from our list. And, if you only need the most essential protection, a great free online virus scanner can be your security centerpiece.
All in our list constantly update their definitions, keeping you ahead of the newest threats.





